k8s环境之cicd部署+远程触发
Posted 一夜暴富--gogogo
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了k8s环境之cicd部署+远程触发相关的知识,希望对你有一定的参考价值。
一、jenkins ci构建
def createVersion()
return new Date().format('yyyyMMddHHmmss')
pipeline
agent any
environment
_version = createVersion()
parameters
gitParameter branchFilter: 'origin/(.*)', defaultValue: 'develop', name: 'BRANCH', type: 'PT_BRANCH'
string defaultValue: 'mvn clean package -am -pl consumer', description: '打包命令', name: 'mvnArgs', trim: false
tools
maven 'MAVEN'
jdk 'JDK'
nodejs 'NODEJS'
stages
stage('pull')
steps
cleanWs()
checkout([$class: 'GitSCM', branches: [[name: "$params.BRANCH"]], doGenerateSubmoduleConfigurations: false, extensions: [], submoduleCfg: [], userRemoteConfigs: [[credentialsId: 'bed05d8f-61e-b90591a2af54', url: "http://git.com/svw/api.git"]]])
stage('MVN')
steps
sh "$params.mvnArgs"
stage('docker-build')
steps
script
env.COMMIT= sh(returnStdout: true, script: 'git rev-parse --short HEAD').trim()
sh """
#!/bin/bash
echo $COMMIT
echo $_version
docker login test.com --username 1xxxxxx1 --password xxxxxxxxxxxxx
cd vota-api-consumer/
docker build --build-arg consumer -t test.com/dev/consumer:$params.BRANCH-$COMMIT-$_version .
docker push test.com/dev/consumer:$params.BRANCH-$COMMIT-$_version
docker rmi test.com/dev/consumer:$params.BRANCH-$COMMIT-$_version
echo "$params.BRANCH-$COMMIT-$_version" > tagid
curl --location --request POST --insecure \\
'https://cicd:1xxxxxxxxxeb56f47001e9fa50@cdi-apicom/job/svw-devconsumer/buildWithParameters' \\
-F 'token=11bxxxxxxxf47001e9fa50' \\
-F "tag=`cat tagid`" \\
-F 'data='
"""
二、cd构建—k8s部署的jenkins
def label = "slave-$UUID.randomUUID().toString()"
podTemplate(label: label, containers: [
containerTemplate(name: 'kubectl', image: 'cnych/kubectl', command: 'cat', ttyEnabled: true)
], serviceAccount: 'jenkins', volumes: [
hostPathVolume(mountPath: '/home/jenkins/.kube', hostPath: '/var/lib/container/jenkins/.kube'),
])
node(label)
parameters
// string defaultValue: ' ', description: '请输入需要部署的consumer服务的image tag', name: 'image_tag', trim: false
string defaultValue: 'tag', description: '镜像tag', name: "COMMIT", trim: false
//string defaultValue: 'Version', description: 'tage', name: "Version", trim: false
stage('运行 Kubectl')
container('kubectl')
// echo "$image_tag"
// echo "$service-$COMMIT-$Version"
sh "kubectl set image deployment/consumer consumer=test.com/dev/consumer:$tag -n dev"
三、k8s部署jenkins
apiVersion: v1
kind: ServiceAccount
metadata:
name: jenkins
namespace: dev
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: jenkins
rules:
- apiGroups: ["extensions", "apps"]
resources: ["deployments"]
verbs: ["create", "delete", "get", "list", "watch", "patch", "update"]
- apiGroups: [""]
resources: ["services"]
verbs: ["create", "delete", "get", "list", "watch", "patch", "update"]
- apiGroups: [""]
resources: ["pods"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/exec"]
verbs: ["create","delete","get","list","patch","update","watch"]
- apiGroups: [""]
resources: ["pods/log"]
verbs: ["get","list","watch"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get"]
- apiGroups: [""]
resources: ["persistentvolume", "persistentvolumeclaims"]
verbs: ["update", "get", "list", "patch", "watch"]
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create", "update", "get", "list", "patch", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: jenkins
namespace: dev
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: jenkins
subjects:
- kind: ServiceAccount
name: jenkins
namespace: dev
jenkins.deploy.yaml
apiVersion: v1
kind: Service
metadata:
name: jenkins
namespace: dev
labels:
app: jenkins
spec:
selector:
app: jenkins
type: NodePort
ports:
- name: web
port: 8080
targetPort: web
nodePort: 32080
- name: agent
port: 50000
targetPort: agent
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: jenkins
namespace: dev
spec:
selector:
matchLabels:
app: jenkins
template:
metadata:
labels:
app: jenkins
spec:
nodeSelector:
cm: test #给节点打标签 固定jenkinspod----因为会指定config认证文件,如果pod漂移就需要所有节点都已添加认证文件了
terminationGracePeriodSeconds: 10
serviceAccount: jenkins
containers:
# affinity:
# nodeAffinity:
# requiredDuringSchedulingIgnoredDuringExecution: # 硬策略
# nodeSelectorTerms:
# - matchExpressions:
# - key: cm
# operator: In
# values:
# - test
- name: jenkins
#image: jenkins:2.60.3
image: jenkins/jenkins:lts
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8080
name: web
- containerPort: 50000
name: agent
resources:
limits:
cpu: 1000m
memory: 1Gi
requests:
cpu: 500m
memory: 512Mi
livenessProbe:
httpGet:
path: /login
port: 8080
initialDelaySeconds: 60
timeoutSeconds: 5
failureThreshold: 12
readinessProbe:
httpGet:
path: /login
port: 8080
initialDelaySeconds: 60
timeoutSeconds: 5
failureThreshold: 12
volumeMounts:
- name: jenkinshome
mountPath: /var/jenkins_home
securityContext:
fsGroup: 1000
runAsUser: 0
volumes:
- name: jenkinshome
hostPath:
path: /var/lib/container/jenkins #需要在同级目录下创建添加.kube/config文件 pipeline要调用kubectl命令
type: Directory
# persistentVolumeClaim:
# claimName: ota-jenkins-cd-pvc
四、jenkins远程触发配置
由于带了map的选择打包构建,会有参数来选择service是发布哪一个
但是如果是远程构建,远程jenkins也采用map的形式,只能通过传参来触发构建
#需要第一个jenkins安装插件Parameterized Remote Trigger
原理:jenkins接口调用
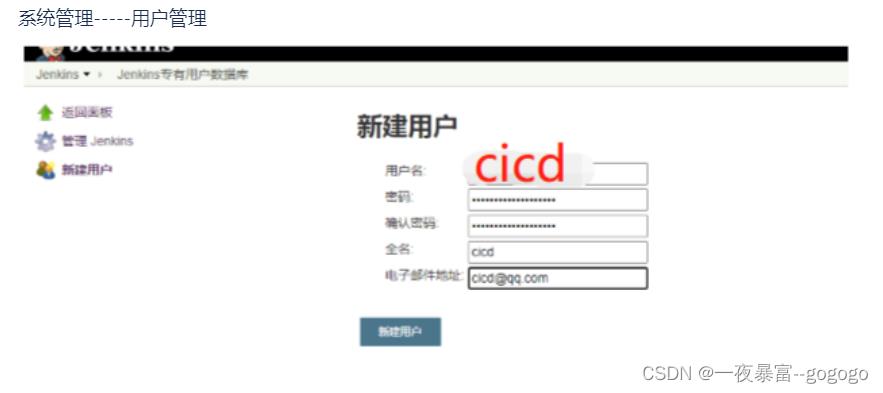
1.在cdjenkins新建cicd用户
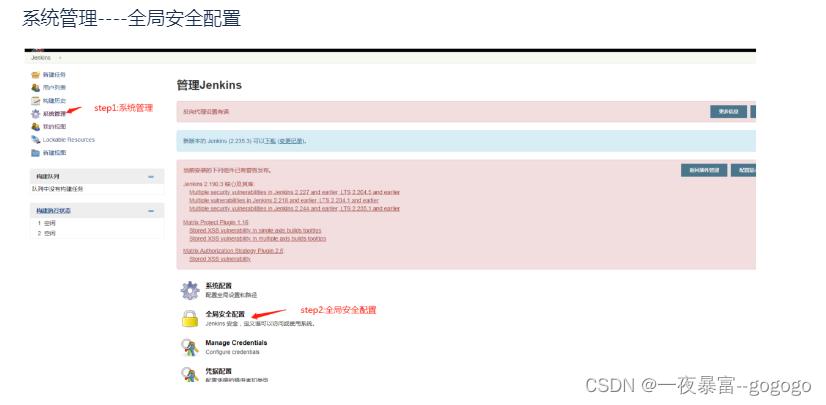
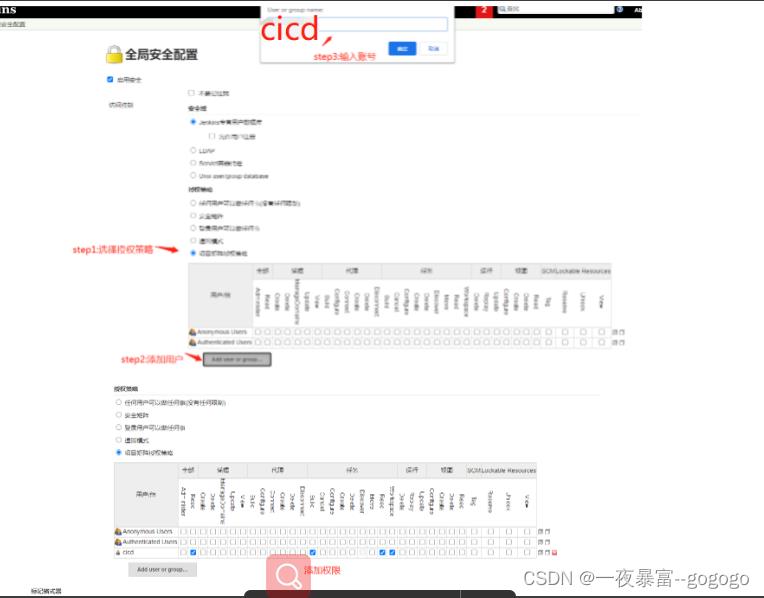
2.开启全局安全配置
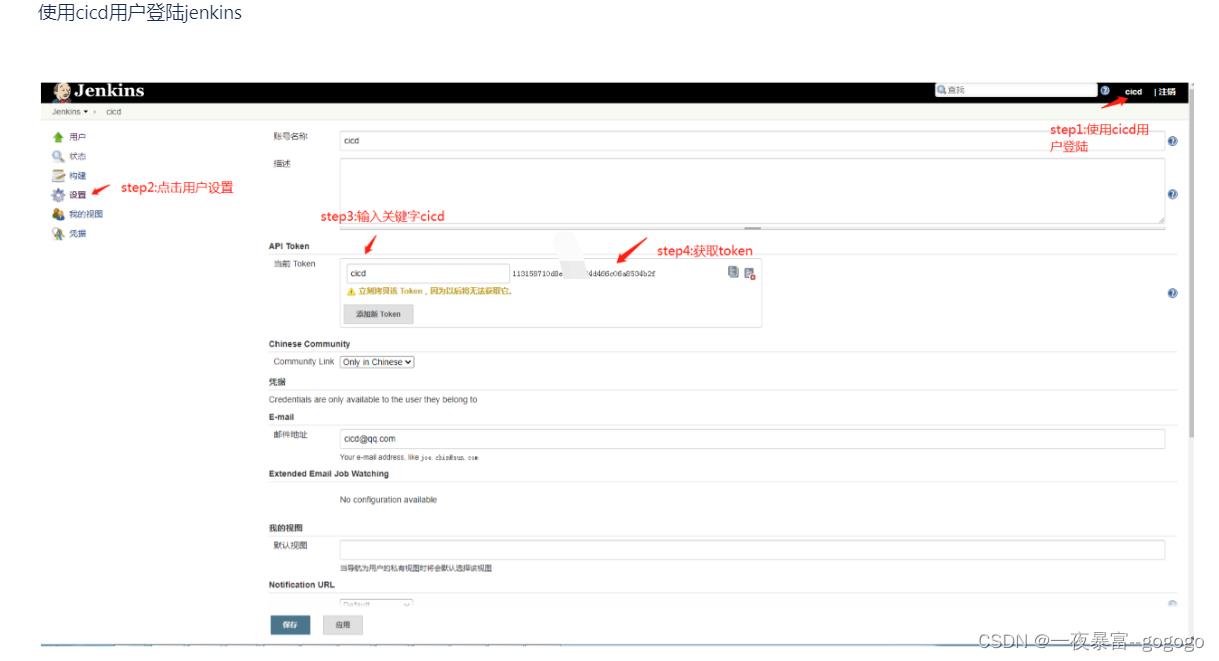
3.获取CICD用户远程api-token
4.在需要被触发的任务中选择触发远程构建,并写入身份验证令牌

5.触发
#https://用户:api-token@jenkins地址/jenkins/job/任务名称/build?token=身份验证令牌
curl -X POST https://cicd:1131xxxxxxx71b84d466c06a8534b2f@jenkins_url/jenkins/job/$JOB_NAME/build?token=bml5b3VsYWRxZGFkYXNkYWRhcWR4QEAjQCMK
带参数触发
echo "$params.BRANCH-$COMMIT-$_version" > tagid
curl --location --request POST --insecure \\
'https://cicd:11be7bac2xxxxxxxxxx5eb56f47001e9fa50@cdi-api-gp-ota-dev.mos.csvw.com/job/svw-dev-cd-viov-security/buildWithParameters' \\
-F 'token=11be7bxxxxxxxxxxxxxx15eb56f47001e9fa50' \\
-F "tag=`cat tagid`" \\
-F 'data='
五、踩坑历程
1.cdjenkins 构建报错
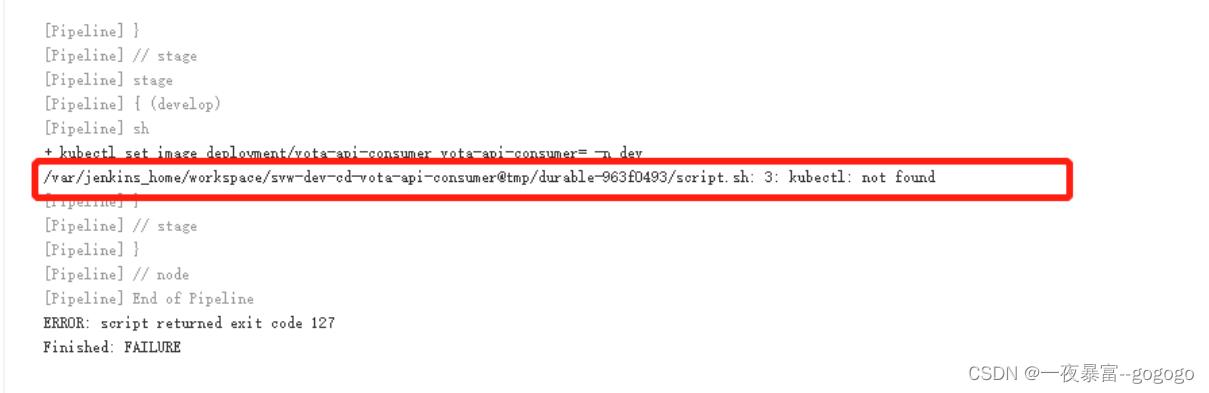
解决:
1.在jenkins home path 也就是/var/lib/container/jenkins同级目录下创建添加.kube/config文件
2.通过nodeselector给节点打标签将jenkins pod 定死在一个认证的可执行kubectl的节点
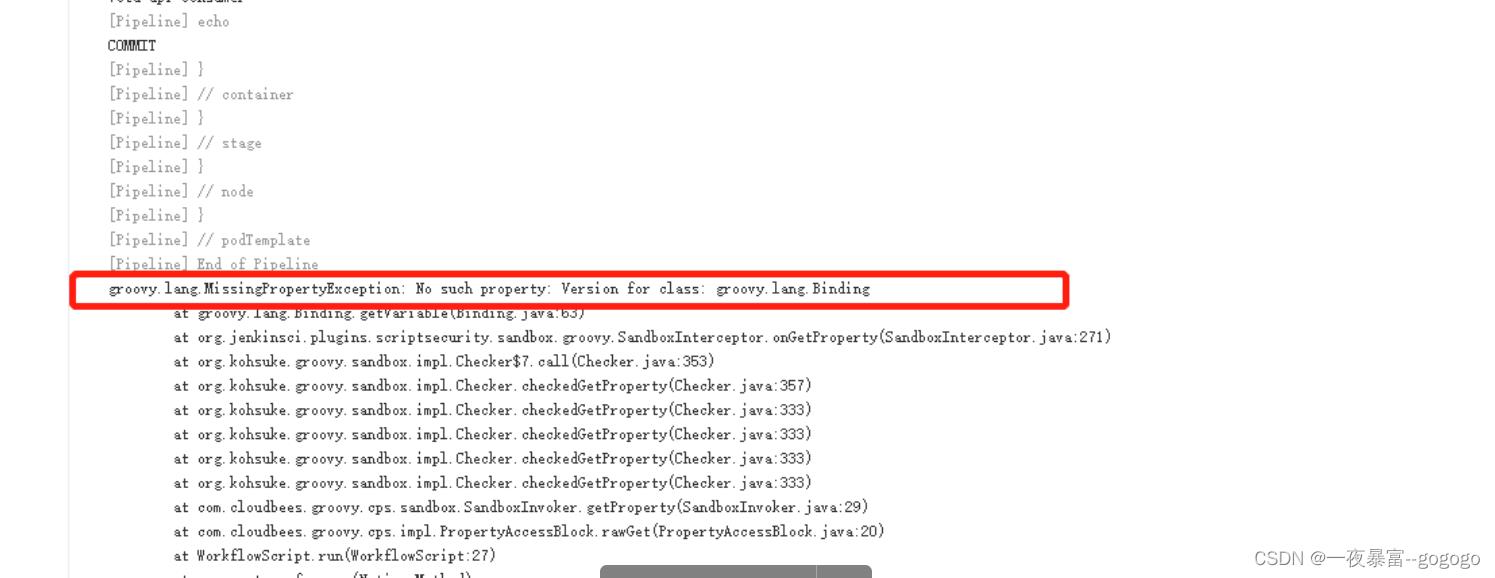
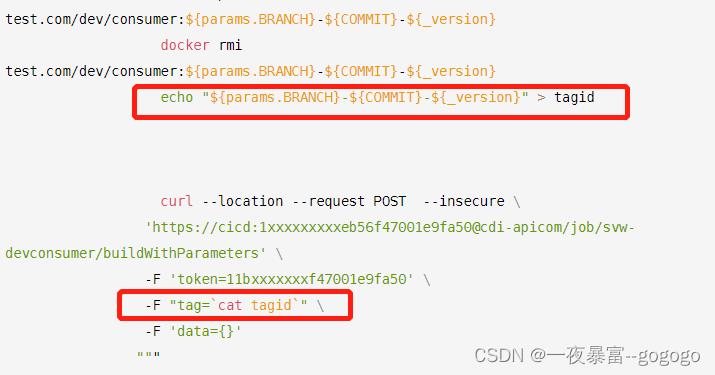
解决:因为version参数在ci的jenkins是个变量,cd这边不能通过远程触发传参的方式获取值
将镜像的tag写死在文件里,echo 进tagid的文件在通过cat获取值,写死成常量即可远程传参获取
具体在ci的pipeline中体现
以上是关于k8s环境之cicd部署+远程触发的主要内容,如果未能解决你的问题,请参考以下文章
CICD实现方法之二--Gitlab+Jenkins+K8S