了解K8S的RBAC
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了了解K8S的RBAC相关的知识,希望对你有一定的参考价值。
参考技术A Role-based access control(RBAC)基于企业内个人用户属于角色来访问计算和网络的常规访问控制方法。简单理解为权限与角色关联,用户通过成为角色的成员来得到角色的权限。K8S的RBAC使用rbac.authorization.k8s.io/v1 API组驱动认证决策,准许管理员通过API动态配置策略。为了启用RBAC,需要在apiserver启动参数添加--authorization-mode=RBAC。目前支持RBAC,ABAC(基于属性的访问控制),Node(默认node和apiserver就是采用这种模式),Webhook。API概览
Role和ClusterRole
rule下verbs有:
"get", "list", "watch", "create", "update", "patch", "delete", "exec"
rule下资源有:
"services", "endpoints", "pods","secrets","configmaps","crontabs","deployments","jobs","nodes","rolebindings","clusterroles","daemonsets","replicasets","statefulsets","horizontalpodautoscalers","replicationcontrollers","cronjobs"
rule下apiGroups有:
"","apps", "autoscaling", "batch"
一个Role只能授权访问单个namespace。
kind:RoleapiVersion:rbac.authorization.k8s.io/v1metadata:namespace:defaultname:pod-readerrules:-apiGroups:[""]#""indicates the core API group resources:["pods"]verbs:["get","watch","list"]
一个ClusterRole能够授予和Role一样的权限,但是它是集群范围内的。
kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1metadata: # "namespace" omitted since ClusterRoles are not namespaced name: secret-readerrules:- apiGroups: [""] resources: ["secrets"] verbs: ["get", "watch", "list"]
RoleBinding和ClusterROleBinding
RoleBinding将role中定义的权限分配给用户和用户组。RoleBinding包含主题(users,groups,或service accounts)和授予角色的引用。对于namespace内的授权使用RoleBinding,集群范围内使用ClusterRoleBinding。
kind: RoleBindingapiVersion: rbac.authorization.k8s.io/v1metadata: name: read-pods namespace: defaultsubjects:- kind: User #这里可以是User,Group,ServiceAccount name: jane apiGroup: rbac.authorization.k8s.ioroleRef: kind: Role #这里可以是Role或者ClusterRole name: pod-reader # this must match the name of the Role or ClusterRole you wish to bind to apiGroup: rbac.authorization.k8s.io
示例
apiVersion: v1kind: ServiceAccountmetadata: name: test-account namespace: kube-system---kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1metadata: name: test-account namespace: kube-systemrules:- apiGroups: ["", "apps", "autoscaling", "batch"] resources: ["services", "endpoints", "pods","secrets","configmaps","crontabs","deployments","jobs","nodes","rolebindings","clusterroles","daemonsets","replicasets","statefulsets","horizontalpodautoscalers","replicationcontrollers","cronjobs"] verbs: ["get", "list", "watch"]---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata: name: test-account namespace: kube-systemroleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: test-accountsubjects:- kind: ServiceAccount name: test-account namespace: kube-system
如果集群中有多个namespace分配给不同的管理员,但是他们的权限是一样的,那么这样可以先定义一个ClusterRole,然后通过RoleBinding将不同namespace的管理员做绑定,这样可以解决多次定义Role的问题。
参考链接
https://kubernetes.io/docs/reference/access-authn-authz/rbac/
Jarque-Bera test|pp图|K-S检验|
Jarque-Bera test:



如何绘制pp图?
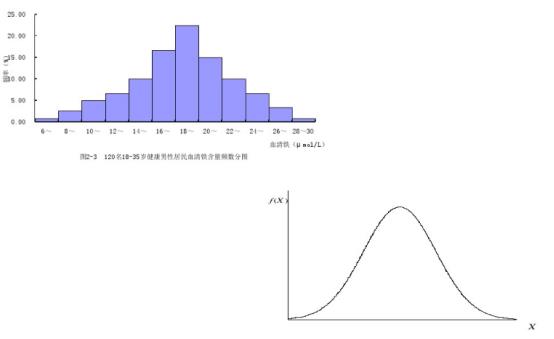

找该直线的截距和斜率,通过截距和斜率的值找到正态参数均值和方差,可对这些正态参数进行正态检验。
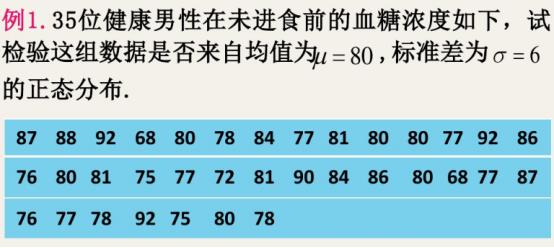
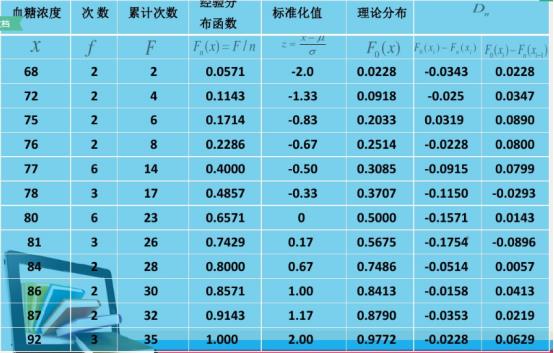
K-S检验的的特点?
并不是只针对正态分布,是针对某一分布。在大样本时针对正态分布。
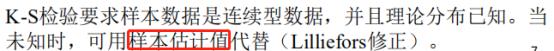


以上是关于了解K8S的RBAC的主要内容,如果未能解决你的问题,请参考以下文章