GRE OVER IPSEC(野蛮模式)
Posted 害怕网络暴力
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了GRE OVER IPSEC(野蛮模式)相关的知识,希望对你有一定的参考价值。
## 野蛮模式适用于两端其中有一端地址不固定的情况
实验拓扑
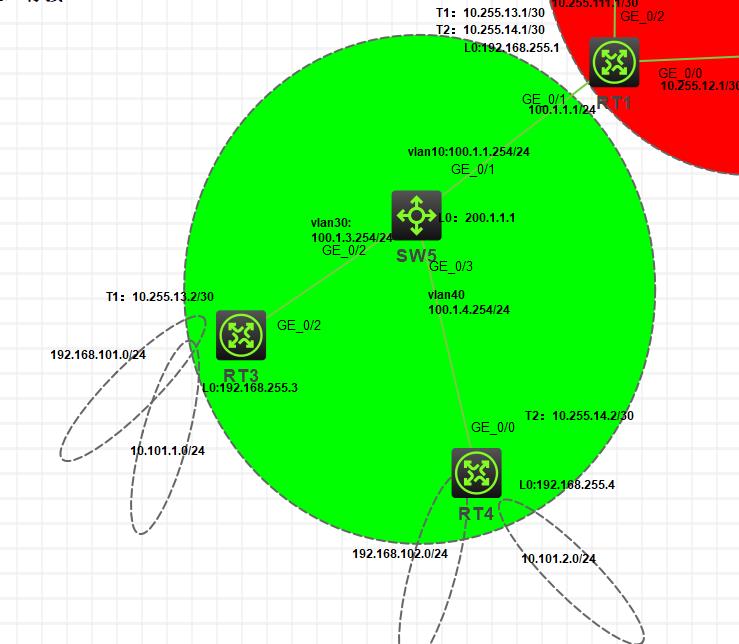
实验思路
1.配置全网地址(这里的地址已经在图上规划,不在赘述)
2.配置ike
3.配置ipsec
4.配置GRE
地址配置完成之后,首先要保证公网可达,因为RT3和RT4是DHCP获取的地址,所以他们上面会有两条默认路由,下一跳是SW5,但是RT1上面没有往公网去的路由,所以要在RT1上配置一条默认路由
RT1
[H3C]ip route-static 0.0.0.0 0 100.1.1.254
RT3 (默认路由是DHCP下发的,优先级为70)
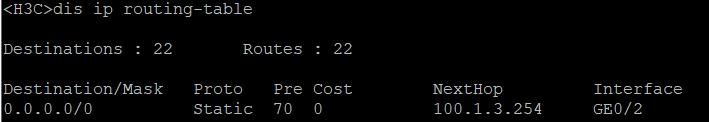
RT4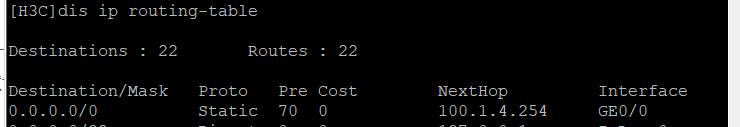
ipsec感兴趣流(只需要在地址不固定的一端配置,简化配置)
RT3
[H3C]acl advanced 3000
[H3C-acl-ipv4-adv-3000]rule 0 permit ip source 192.168.255.3 0 destination 192
.168.255.1 0
RT4
[H3C]acl advanced 3000
[H3C-acl-ipv4-adv-3000]rule 0 permit ip source 192.168.255.4 0 destination 192
.168.255.1 0
配置ike
RT1
[H3C]ike keychain r3
[H3C-ike-keychain-r3]pre-shared-key hostname r3 key simple 123 #对端地址不固定,所以采用对等体名称,
[H3C-ike-keychain-r3]qu
[H3C]ike keychain r4
[H3C-ike-keychain-r4]pre-shared-key hostname r4 key simple 123
[H3C-ike-keychain-r4]qu
[H3C]ike proposal 3
[H3C-ike-proposal-3]qu
[H3C]ike proposal 4
[H3C-ike-proposal-4]qu
[H3C]ike profile p3
[H3C-ike-profile-p3]keychain r3
[H3C-ike-profile-p3]exchange-mode aggressive # ike协商为野蛮模式
[H3C-ike-profile-p3]local-identity fqdn r1
[H3C-ike-profile-p3]match remote identity fqdn r3
[H3C-ike-profile-p3]proposal 3
[H3C-ike-profile-p3]qu
[H3C]ike profile p4
[H3C-ike-profile-p4]keychain r4
[H3C-ike-profile-p4]exchange-mode aggressive
[H3C-ike-profile-p4]local-identity fqdn r1
[H3C-ike-profile-p4]match remote identity fqdn r4
[H3C-ike-profile-p4]proposal 4
[H3C-ike-profile-p4]qu
RT3
[H3C]ike keychain r1
[H3C-ike-keychain-r1]pre-shared-key address 100.1.1.1 key simple 123 # 对端地址是固定的
[H3C-ike-keychain-r1]qu
[H3C]ike proposal 1
[H3C-ike-proposal-1]qu
[H3C]ike profile p1
[H3C-ike-profile-p1]exchange-mode aggressive
[H3C-ike-profile-p1]keychain r1
[H3C-ike-profile-p1]proposal 1
[H3C-ike-profile-p1]local-identity fqdn r3
[H3C-ike-profile-p1]match remote identity fqdn r1
RT4
[H3C]ike keychain r1
[H3C-ike-keychain-r1]pre-shared-key address 100.1.1.1 key simple 123
[H3C-ike-keychain-r1]qu
[H3C]ike proposal 1
[H3C-ike-proposal-1]qu
[H3C]ike profile p1
[H3C-ike-profile-p1]exchange-mode aggressive
[H3C-ike-profile-p1]local-identity fqdn r4
[H3C-ike-profile-p1]match remote identity fqdn r1
[H3C-ike-profile-p1]proposal 1
[H3C-ike-profile-p1]keychain r1
配置ipsec
RT1
[H3C]ipsec transform-set t3
[H3C-ipsec-transform-set-t3]esp authentication-algorithm md5
[H3C-ipsec-transform-set-t3]esp encryption-algorithm des-cbc
[H3C-ipsec-transform-set-t3]qu
[H3C]ipsec transform-set t4
[H3C-ipsec-transform-set-t4]esp encryption-algorithm des-cbc
[H3C-ipsec-transform-set-t4]esp authentication-algorithm md5
[H3C-ipsec-transform-set-t4]qu
[H3C]ipsec policy-template tem 3
[H3C-ipsec-policy-template-tem-3]transform-set t3
[H3C-ipsec-policy-template-tem-3]ike-profile p3
[H3C-ipsec-policy-template-tem-3]qu
[H3C]ipsec policy-template tem 4
[H3C-ipsec-policy-template-tem-4]transform-set t4
[H3C-ipsec-policy-template-tem-4]ike-profile p4
[H3C-ipsec-policy-template-tem-4]qu
[H3C]ipsec policy H3C 1 isakmp template tem
[H3C-GigabitEthernet0/1]ipsec apply policy H3C
RT3
[H3C]ipsec transform-set t1
[H3C-ipsec-transform-set-t1]esp encryption-algorithm des-cbc
[H3C-ipsec-transform-set-t1]esp authentication-algorithm md5
[H3C-ipsec-transform-set-t1]qu
[H3C]ipsec policy H3C 1 isakmp
[H3C-ipsec-policy-isakmp-H3C-1]security acl 3000
[H3C-ipsec-policy-isakmp-H3C-1]transform-set t1
[H3C-ipsec-policy-isakmp-H3C-1]ike-profile p1
[H3C-ipsec-policy-isakmp-H3C-1]remote-address 100.1.1.1
[H3C-ipsec-policy-isakmp-H3C-1]qu
[H3C]interface g0/2
[H3C-GigabitEthernet0/2]ipsec apply policy H3C
RT4
[H3C]ipsec transform-set t1
[H3C-ipsec-transform-set-t1]esp encryption-algorithm des-cbc
[H3C-ipsec-transform-set-t1]esp authentication-algorithm md5
[H3C-ipsec-transform-set-t1]qu
[H3C]ipsec policy H3C 1 isakmp
[H3C-ipsec-policy-isakmp-H3C-1]transform-set t1
[H3C-ipsec-policy-isakmp-H3C-1]security acl 3000
[H3C-ipsec-policy-isakmp-H3C-1]ike-profile p1
[H3C-ipsec-policy-isakmp-H3C-1]remote-address 100.1.1.
[H3C-ipsec-policy-isakmp-H3C-1]qu
[H3C]interface g0/0
[H3C-GigabitEthernet0/0]ipsec apply policy H3C
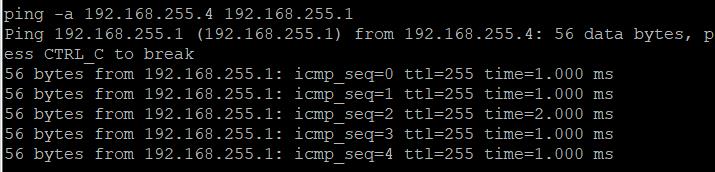
测试连通性,地址不固定一端发起请求
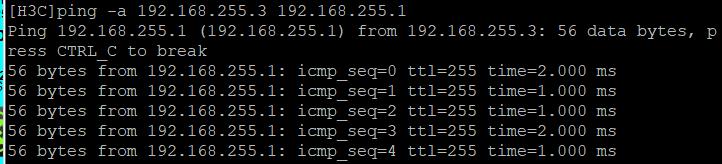
配置GRE
RT1
[H3C]interface Tunnel 1 mode gre
[H3C-Tunnel1]ip address 10.255.13.1 30
[H3C-Tunnel1]source 192.168.255.1
[H3C-Tunnel1]destination 192.168.255.3
[H3C-Tunnel1]qu
[H3C]interface Tunnel 2 mode gre
[H3C-Tunnel2]ip address 10.255.14.1 30
[H3C-Tunnel2]source 192.168.255.1
[H3C-Tunnel2]destination 192.168.255.4
[H3C-Tunnel2]qu
RT3
[H3C]interface Tunnel 1 mode gre
[H3C-Tunnel1]ip address 10.255.13.2 30
[H3C-Tunnel1]source 192.168.255.3
[H3C-Tunnel1]destination 192.168.255.1
RT4
[H3C]interface Tunnel 1 mode gre
[H3C-Tunnel1]ip address 10.255.14.2 30
[H3C-Tunnel1]source 192.168.255.4
[H3C-Tunnel1]destination 192.168.255.1
这个时候GRE over IPSEC就已经配置完成了,可以在两边运行路由协议,进行路由的通告。
RT1
[H3C]rip 1
[H3C-rip-1]v
[H3C-rip-1]version 2
[H3C-rip-1]undo s
[H3C-rip-1]undo summary
[H3C-rip-1]net
[H3C-rip-1]network 10.255.13.1 0.0.0.0
RT3
[H3C]rip 1
[H3C-rip-1]version 2
[H3C-rip-1]undo summary
[H3C-rip-1]network 10.255.13.2 0.0.0.0
[H3C-rip-1]network 192.168.101.0 0.0.0.255
[H3C-rip-1]network 10.101.1.0 0.0.0.255
以上是关于GRE OVER IPSEC(野蛮模式)的主要内容,如果未能解决你的问题,请参考以下文章