浏览器直播源抓取浏览器抓取真实直播源地址(2022/11/16)
Posted 优小U
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了浏览器直播源抓取浏览器抓取真实直播源地址(2022/11/16)相关的知识,希望对你有一定的参考价值。

距离上次抓取直播源已经过去一年了,最近发现官方已更新了,以前的方法并不适用了,于是再来一波解析,小伙伴们准备好发车了吗?
一、版本回顾
之前直播源解析是从H5版本入手,直接从H5页面拿到全局变量liveLineUrl,这是一个m3u8的播放地址,可以用VLC等播放器直接播放;另发现 一起看 模块的直播源地址和一般房间不同,fm参数已经变成了seqid:
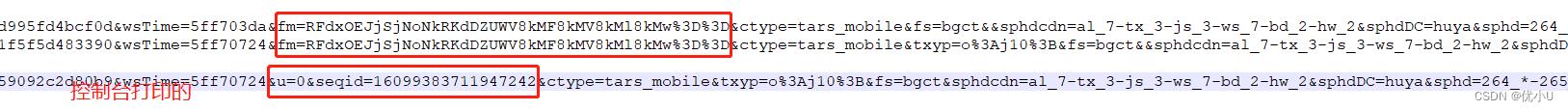
如今版本发现全局变量中的liveLineUrl已经变成加密的了,类似 Ly9hbC5obHMuaHV5YS5jb20vc3JjLzE2Nzc5NDIzMzMtMTY3Nzk0MjMzMy03MjA2NzA3NDQ0ODA4OTQxNTY4LTMzNTYwMDgxMjItMTAwNTctQS0wLTEubTN1OD9yYXRpbz0yMDAwJndzU2VjcmV0PWVkZjE3ZmNkMTk0ZDY2ZTY4MjIxYjQ4NjIxMWZiNWEyJndzVGltZT02Mzc2MmJiNSZmbT1SRmR4T0VKalNqTm9Oa1JLZERaVVdWOGtNRjhrTVY4a01sOGtNdyUzRCUzRCZjdHlwZT10YXJzX21vYmlsZSZmcz1iZ2N0JnNwaGRjZG49YWxfNy10eF8zLWpzXzMtd3NfNy1iZF8yLWh3XzImc3BoZERDPWh1eWEmc3BoZD0yNjRfKi0yNjVfKiZleHNwaGQ9MjY0XzUwMCwmdD0xMDM=,炸一看感觉很可怕,其实跟简单这个就是典型的 base64 加密,我们用 在线工具 解密一下,得到结果 //al.hls.****.com/src/1677942333-1677942333-7206707444808941568-3356008122-10057-A-0-1.m3u8?ratio=2000&wsSecret=edf17fcd194d66e68221b486211fb5a2&wsTime=63762bb5&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103
上面播放地址看似正常但是不能播放。。。
二、地址参数解析
查看下真实的播放地址是:
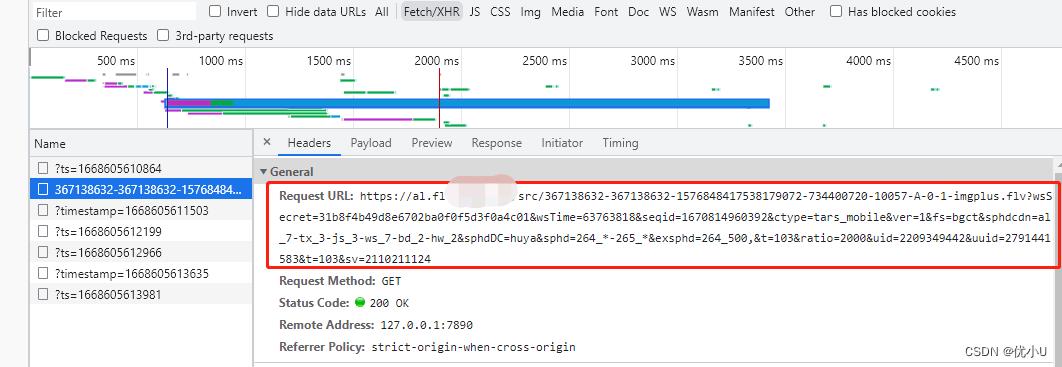
对比发现m3u8格式变成了flv格式,这个其实不重要,官方支持多种直播源格式,但是里面有 seqid 参数,没有 fm 参数,其他的参数其实在全局变量都有(只保留了重要的数据):
"roomProfile":
"lUid": 367138632,
"liveLineUrl": "Ly9hbC5obHMuaHV5YS5jb20vc3JjLzM2NzEzODYzMi0zNjcxMzg2MzItMTU3Njg0ODQxNzUzODE3OTA3Mi03MzQ0MDA3MjAtMTAwNTctQS0wLTEtaW1ncGx1cy5tM3U4P3JhdGlvPTIwMDAmd3NTZWNyZXQ9ZTY3NzBjZTEwNTc5ZDVkZmU3ZjAzNjM1MWRiMzgzMmYmd3NUaW1lPTYzNzYzODE4JmZtPVJGZHhPRUpqU2pOb05rUktkRFpVV1Y4a01GOGtNVjhrTWw4a013JTNEJTNEJmN0eXBlPXRhcnNfbW9iaWxlJmZzPWJnY3Qmc3BoZGNkbj1hbF83LXR4XzMtanNfMy13c183LWJkXzItaHdfMiZzcGhkREM9aHV5YSZzcGhkPTI2NF8qLTI2NV8qJmV4c3BoZD0yNjRfNTAwLCZ0PTEwMw=="
,
"roomInfo":
"tLiveInfo":
"tLiveStreamInfo":
"vStreamInfo":
"value": [
"sCdnType": "AL",
"iIsMaster": 0,
"lChannelId": 367138632,
"lSubChannelId": 367138632,
"lPresenterUid": 367138632,
"sStreamName": "367138632-367138632-1576848417538179072-734400720-10057-A-0-1-imgplus",
"sFlvUrl": "http://al.flv.****.com/src",
"sFlvUrlSuffix": "flv",
"sFlvAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"sHlsUrl": "http://al.hls.****.com/src",
"sHlsUrlSuffix": "m3u8",
"sHlsAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"iIsP2PSupport": 2,
"sP2pUrl": "http://al.p2p.****.com/****live",
"sP2pUrlSuffix": "slice",
"sP2pAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103"
,
"sCdnType": "TX",
"iIsMaster": 0,
"lChannelId": 367138632,
"lSubChannelId": 367138632,
"lPresenterUid": 367138632,
"sStreamName": "367138632-367138632-1576848417538179072-734400720-10057-A-0-1-imgplus",
"sFlvUrl": "http://tx.flv.****.com/src",
"sFlvUrlSuffix": "flv",
"sFlvAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"sHlsUrl": "http://tx.hls.****.com/src",
"sHlsUrlSuffix": "m3u8",
"sHlsAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"sP2pUrl": "http://tx.p2p.****.com/****live",
"sP2pUrlSuffix": "slice",
"sP2pAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103"
,
"sCdnType": "HW",
"iIsMaster": 0,
"lChannelId": 367138632,
"lSubChannelId": 367138632,
"lPresenterUid": 367138632,
"sStreamName": "367138632-367138632-1576848417538179072-734400720-10057-A-0-1-imgplus",
"sFlvUrl": "http://hw.flv.****.com/src",
"sFlvUrlSuffix": "flv",
"sFlvAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"sHlsUrl": "http://hw.hls.****.com/src",
"sHlsUrlSuffix": "m3u8",
"sHlsAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103",
"iIsP2PSupport": 2,
"sP2pUrl": "http://hw.p2p.****.com/****live",
"sP2pUrlSuffix": "slice",
"sP2pAntiCode": "wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103"
]
,
"iDefaultLiveStreamBitRate": 2000,
"sDefaultLiveStreamLine": "AL",
"sDefaultLiveStreamSuffix": "m3u8",
"sDefaultLiveStreamUrl": "http://al.hls.****.com/src/367138632-367138632-1576848417538179072-734400720-10057-A-0-1-imgplus.m3u8?ratio=2000&wsSecret=e6770ce10579d5dfe7f036351db3832f&wsTime=63763818&fm=RFdxOEJjSjNoNkRKdDZUWV8kMF8kMV8kMl8kMw%3D%3D&ctype=tars_mobile&fs=bgct&sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2&sphdDC=****&sphd=264_*-265_*&exsphd=264_500,&t=103"
可以看到地址的参数基本都有了,也有很多默认的地址,但是都不能直接播放,不是真实的播放地址,也没有看到 seqid 参数,所以我们还是需要去找一下。
大致步骤:
-
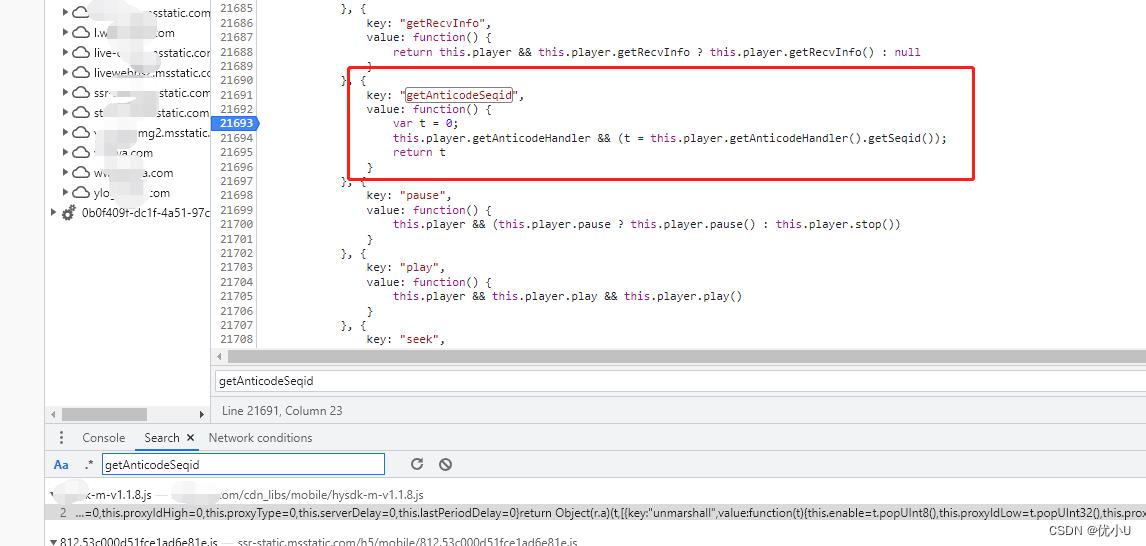
找到
seqid位置,getAnticodeSeqid方法是关键
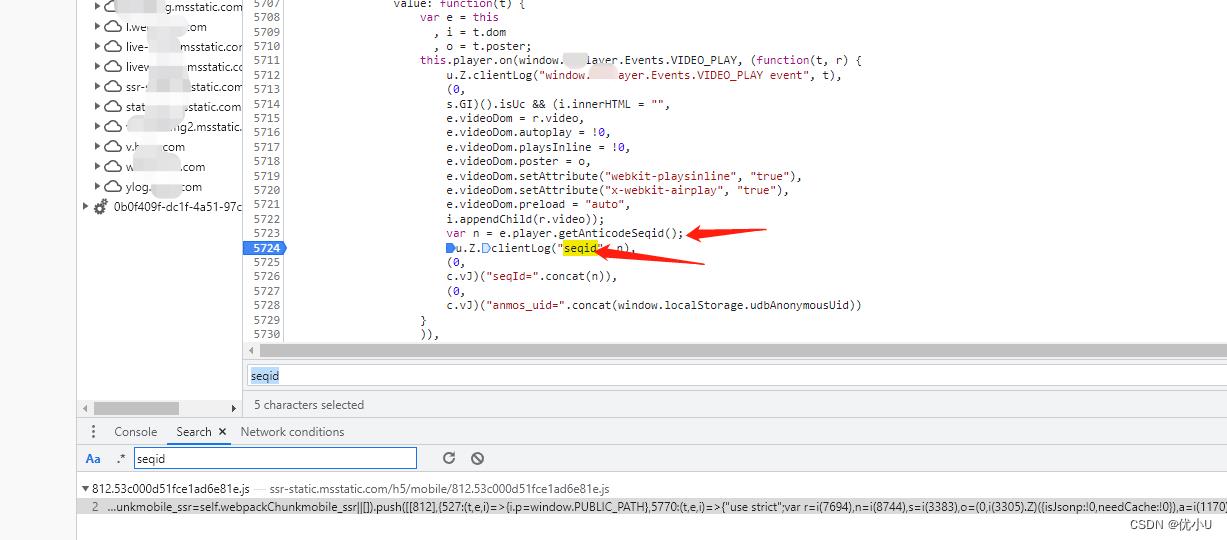
-
搜索
getAnticodeSeqid方法,在官方sdk中
-
搜索
getAnticode相关的方法
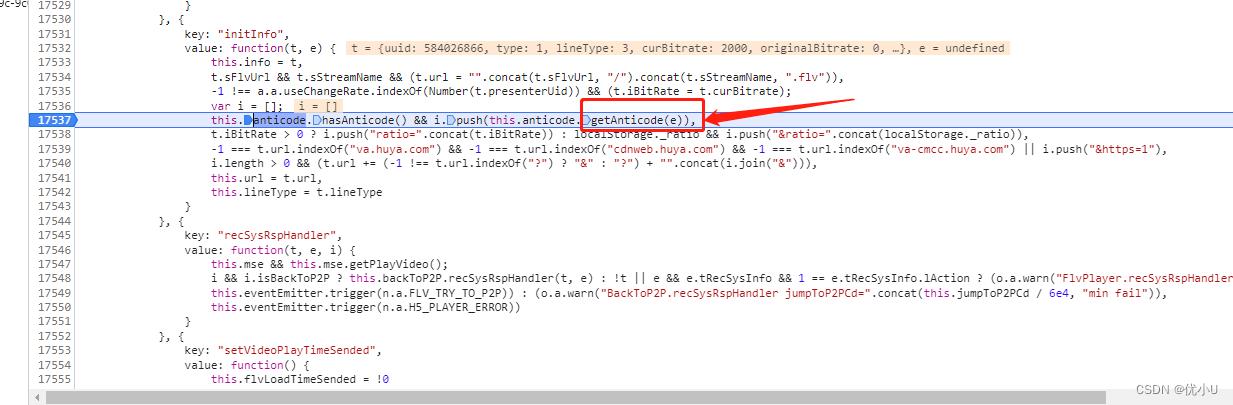
getAnticode方法进入加密方法,这个方法返回的参数里面包含了seqid,接下来就是找出各个加密方法和参数:
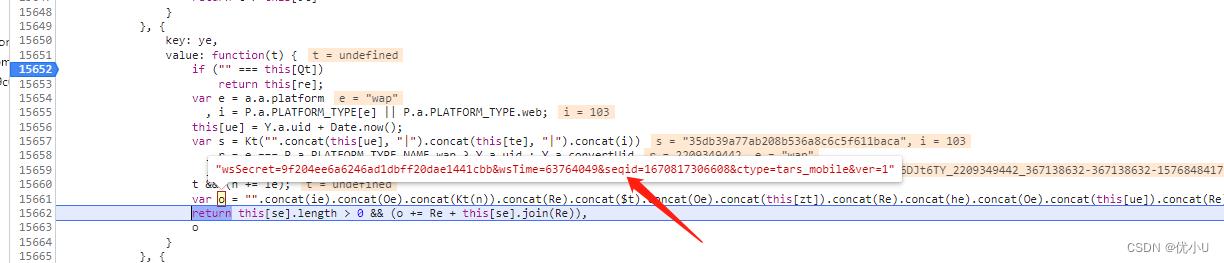
this[Qt]是fm参数解密出来的,结果类似DWq8BcJ3h6DJt6TY_$0_$1_$2_$3:
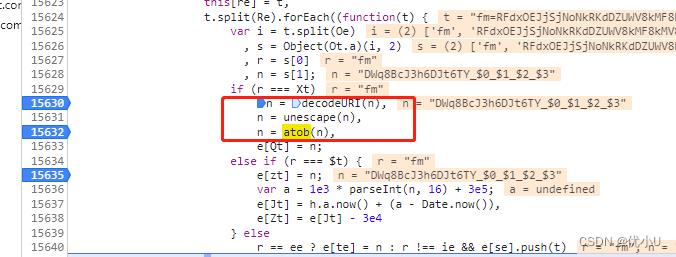
this[ae] 是 sStreamName
this[zt] 是 wsTime
- 加密方法和参数,总结以下方法:
// 主方法
export function getUrl(sStreamName, wsTime, fm)
let uid = 2209349442; // uid 可固定
let ue = uid + 1668612439268; // Date.now(); 这里时间和wsTime等参数需要配套使用,这里做测试使用,正常是需要使用Date.now();
let s = Kt(""+ue+"|tars_mobile|103")
let r = uid
let n = parseFm(fm).replace("$0", r).replace("$1", sStreamName).replace("$2", s).replace("$3", wsTime);
let o = `wsSecret=$Kt(n)&wsTime=$wsTime&seqid=$ue&ctype=tars_mobile&ver=1`;
let se = ["fs=bgct","sphdcdn=al_7-tx_3-js_3-ws_7-bd_2-hw_2","sphdDC=****","sphd=264_*-265_*","t=103","exsphd=264_500,264_2000,"];
let res = sStreamName + ".flv?" + o + "&" + se.join('&')
return res;
// 以上用的加密方法
function parseFm(_fm)
let fm = decodeURI(_fm);
fm = unescape(fm);
return atob(fm)
function Kt(t)
return Bt(Ht(t))
function Bt(t)
var e, i, s = "";
for (i = 0; i < t.length; i += 1)
e = t.charCodeAt(i),
s += "0123456789abcdef".charAt(e >>> 4 & 15) + "0123456789abcdef".charAt(15 & e);
return s
function Ht(t)
return function(t)
return Vt(Ft(xt(t), 8 * t.length))
(Gt(t))
function Gt(t)
return unescape(encodeURIComponent(t))
function Vt(t)
var e, i = "", s = 32 * t.length;
for (e = 0; e < s; e += 8)
i += String.fromCharCode(t[e >> 5] >>> e % 32 & 255);
return i
function Ft(t, e)
var i, s, r, n, a;
t[e >> 5] |= 128 << e % 32,
t[14 + (e + 64 >>> 9 << 4)] = e;
var o = 1732584193, h = -271733879 , u = -1732584194 , l = 271733878;
for (i = 0; i < t.length; i += 16)
s = o,
r = h,
n = u,
a = l,
o = Dt(o, h, u, l, t[i], 7, -680876936),
l = Dt(l, o, h, u, t[i + 1], 12, -389564586),
u = Dt(u, l, o, h, t[i + 2], 17, 606105819),
h = Dt(h, u, l, o, t[i + 3], 22, -1044525330),
o = Dt(o, h, u, l, t[i + 4], 7, -176418897),
l = Dt(l, o, h, u, t[i + 5], 12, 1200080426),
u = Dt(u, l, o, h, t[i + 6], 17, -1473231341),
h = Dt(h, u, l, o, t[i + 7], 22, -45705983),
o = Dt(o, h, u, l, t[i + 8], 7, 1770035416),
l = Dt(l, o, h, u, t[i + 9], 12, -1958414417),
u = Dt(u, l, o, h, t[i + 10], 17, -42063),
h = Dt(h, u, l, o, t[i + 11], 22, -1990404162),
o = Dt(o, h, u, l, t[i + 12], 7, 1804603682),
l = Dt(l, o, h, u, t[i + 13], 12, -40341101),
u = Dt(u, l, o, h, t[i + 14], 17, -1502002290),
o = bt(o, h = Dt(h, u, l, o, t[i + 15], 22, 1236535329), u, l, t[i + 1], 5, -165796510),
l = bt(l, o, h, u, t[i + 6], 9, -1069501632),
u = bt(u, l, o, h, t[i + 11], 14, 643717713),
h = bt(h, u, l, o, t[i], 20, -373897302),
o = bt(o, h, u, l, t[i + 5], 5, -701558691),
l = bt(l, o, h, u, t[i + 10], 9, 38016083),
u = bt(u, l, o, h, t[i + 15], 14, -660478335),
h = bt(h, u, l, o, t[i + 4], 20, -405537848),
o = bt(o, h, u, l, t[i + 9], 5, 568446438),
l = bt(l, o, h, u, t[i + 14], 9, -1019803690),
u = bt(u, l, o, h, t[i + 3], 14, -187363961),
h = bt(h, u, l, o, t[i + 8], 20, 1163531501),
o = bt(o, h, u, l, t[i + 13], 5, -1444681467),
l = bt(l, o, h, u, t[i + 2], 9, -51403784),
u = bt(u, l, o, h, t[i + 7], 14, 1735328473),
o = Nt(o, h = bt(h, u, l, o, t[i + 12], 20, -1926607734), u, l, t[i + 5], 4, -378558),
l = Nt(l, o, h, u, t[i + 8], 11, -2022574463),
u = Nt(u, l, o, h, t[i + 11], 16, 1839030562),
h = Nt(h, u, l, o, t[i + 14], 23, -35309556),
o = Nt(o, h, u, l, t[i + 1], 4, -1530992060),
l = Nt(l, o, h, u, t[i + 4], 11, 1272893353),
u = Nt(u, l, o, h, t[i + 7], 16,