云原生 | Kubernetes篇Ingress案例实战
Posted Lansonli
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了云原生 | Kubernetes篇Ingress案例实战相关的知识,希望对你有一定的参考价值。

文章目录
Ingress案例实战
一、基本配置
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
rules:
- host: itlanson.com
http:
paths:
- path: /
pathType: Prefix
backend: ## 指定需要响应的后端服务
service:
name: my-nginx-svc ## kubernetes集群的svc名称
port:
number: 80 ## service的端口号-
pathType 详细:
-
Prefix:基于以/分隔的 URL 路径前缀匹配。匹配区分大小写,并且对路径中的元素逐个完成。 路径元素指的是由/分隔符分隔的路径中的标签列表。 如果每个 p 都是请求路径 p 的元素前缀,则请求与路径 p 匹配。 -
Exact:精确匹配 URL 路径,且区分大小写。 -
ImplementationSpecific:对于这种路径类型,匹配方法取决于 IngressClass。 具体实现可以将其作为单独的pathType处理或者与Prefix或Exact类型作相同处理。
-
ingress规则会生效到所有按照了IngressController的机器的nginx配置。
二、默认后端
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
defaultBackend: ## 指定所有未匹配的默认后端
service:
name: php-apache
port:
number: 80
rules:
- host: itlanson.com
http:
paths:
- path: /abc
pathType: Prefix
backend:
service:
name: my-nginx-svc
port:
number: 80效果
itlanson.com 下的 非 /abc 开头的所有请求,都会到defaultBackend
非itlanson.com 域名下的所有请求,也会到defaultBackend
nginx的全局配置
kubectl edit cm ingress-nginx-controller -n ingress-nginx编辑配置加上
data:
配置项: 配置值
所有配置项参考
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/configmap
基于环境变量带去的
三、路径重写
Rewrite - NGINX Ingress Controller
Rewrite功能,经常被用于前后分离的场景
-
前端给服务器发送 / 请求映射前端地址。
-
后端给服务器发送 /api 请求来到对应的服务。但是后端服务没有 /api的起始路径,所以需要ingress-controller自动截串
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations: ## 写好annotion
#https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/
nginx.ingress.kubernetes.io/rewrite-target: /$2 ### 只保留哪一部分
name: rewrite-ingress-02
namespace: default
spec:
rules: ## 写好规则
- host: itlanson.com
http:
paths:
- backend:
service:
name: php-apache
port:
number: 80
path: /api(/|$)(.*)
pathType: Prefix四、配置SSL
TLS/HTTPS - NGINX Ingress Controller
生成证书:(也可以去青云申请免费证书进行配置)
$ openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout $KEY_FILE:tls.key -out $CERT_FILE:tls.cert -subj "/CN=$HOST:itlanson.com/O=$HOST:itlanson.com"
kubectl create secret tls $CERT_NAME:itlanson-tls --key $KEY_FILE:tls.key --cert $CERT_FILE:tls.cert
## 示例命令如下
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.cert -subj "/CN=it666.com/O=it666.com"
kubectl create secret tls it666-tls --key tls.key --cert tls.certapiVersion: v1
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJekNDQWd1Z0F3SUJBZ0lKQVB6YXVMQ1ZjdlVKTUEwR0NTcUdTSWIzRFFFQkN3VUFNQ2d4RWpBUUJnTlYKQkFNTUNXbDBOalkyTG1OdmJURVNNQkFHQTFVRUNnd0phWFEyTmpZdVkyOXRNQjRYRFRJeE1EVXhNREV5TURZdwpNRm9YRFRJeU1EVXhNREV5TURZd01Gb3dLREVTTUJBR0ExVUVBd3dKYVhRMk5qWXVZMjl0TVJJd0VBWURWUVFLCkRBbHBkRFkyTmk1amIyMHdnZ0VpTUEwR0NTcUdTSWIzRFFFQkFRVUFBNElCRHdBd2dnRUtBb0lCQVFDbkNYa0wKNjdlYzNjYW5IU1V2VDR6YXZmMGpsOEFPWlBtUERhdUFRTElEby80LzlhV2JPSy9yZm5OelVXV3lTRFBqb3pZVApWa2xmQTZYRG1xRU5FSWRHRlhjdExTSlRNRkM5Y2pMeTlwYVFaaDVYemZId0ZoZXZCR1J3MmlJNXdVdk5iTGdWCmNzcmRlNXlKMEZYOFlMZFRhdjhibzhjTXpxN2FqZXhXMWc1dkxmTWZhczAvd2VyVk9Qc0ZmS3RwZ1dwSWMxMXEKekx6RnlmWHNjcVNhVTV2NFo5WHFqQjRtQjhZZ043U2FSa2pzU0VsSFU4SXhENEdTOUtTNGtkR2xZak45V2hOcAp6aG5MdllpSDIrZThQWE9LdU8wK2Jla1MrS3lUS2hnNnFWK21kWTN0MWJGenpCdjFONTVobTNQTldjNk9ROTh3CkYrQk9uUUNhWExKVmRRcS9BZ01CQUFHalVEQk9NQjBHQTFVZERnUVdCQlNzSUFvMHZ4RFZjVWtIZ1V1TFlwY0wKdjBFSERqQWZCZ05WSFNNRUdEQVdnQlNzSUFvMHZ4RFZjVWtIZ1V1TFlwY0x2MEVIRGpBTUJnTlZIUk1FQlRBRApBUUgvTUEwR0NTcUdTSWIzRFFFQkN3VUFBNElCQVFDSjFEdGJoQnBacTE1ODVEMGlYV1RTdmU3Q2YvQ3VnakxZCjNYb2gwSU9sNy9mVmNndFJkWXlmRFBmRDFLN0l4bElETWtUbTVEVWEyQzBXaFY5UlZLU0poSTUzMmIyeVRGcm8Kc053eGhkcUZpOC9CU1lsQTl0Tk5HeXhKT1RKZWNtSUhsaFhjRlEvUzFaK3FjVWNrTVh6UHlIcFl0VjRaU0hheQpFWVF2bUVBZTFMNmlnRk8wc2xhbUllTFBCTWhlTDNnSDZQNlV3TVpQbTRqdFR1d2FGSmZGRlRIakQydmhSQkJKCmZjTGY5QjN3U3k2cjBDaXF2VXQxQUNQVnpSdFZrcWJJV1d5VTBDdkdjVDVIUUxPLzdhTE4vQkxpNGdYV2o1MUwKVXdTQzhoY2xodVp3SmRzckNkRlltcjhTMnk0UDhsaDdBc0ZNOGorNjh1ZHJlYXovWmFNbwotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2QUlCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktZd2dnU2lBZ0VBQW9JQkFRQ25DWGtMNjdlYzNjYW4KSFNVdlQ0emF2ZjBqbDhBT1pQbVBEYXVBUUxJRG8vNC85YVdiT0svcmZuTnpVV1d5U0RQam96WVRWa2xmQTZYRAptcUVORUlkR0ZYY3RMU0pUTUZDOWNqTHk5cGFRWmg1WHpmSHdGaGV2QkdSdzJpSTV3VXZOYkxnVmNzcmRlNXlKCjBGWDhZTGRUYXY4Ym84Y016cTdhamV4VzFnNXZMZk1mYXMwL3dlclZPUHNGZkt0cGdXcEljMTFxekx6RnlmWHMKY3FTYVU1djRaOVhxakI0bUI4WWdON1NhUmtqc1NFbEhVOEl4RDRHUzlLUzRrZEdsWWpOOVdoTnB6aG5MdllpSAoyK2U4UFhPS3VPMCtiZWtTK0t5VEtoZzZxVittZFkzdDFiRnp6QnYxTjU1aG0zUE5XYzZPUTk4d0YrQk9uUUNhClhMSlZkUXEvQWdNQkFBRUNnZ0VBTDZ0Tlp6Q0MrdnB6cWRkd2VEcjhtS1JsckpXdkVxeVFaOW5mMnI4Ynpsd3IKdi9jTHB1dWJrTnBLZWx0OWFVNmZ1RlFvcDRZVmRFOG5MRlpocGNmVXd4UjNLV1piQ0dDZWVpSXdGaFIzVFloSApHb25FaE43WkxYSlVjN3hjemh5eTFGSTFpckZ5NFpoWVNTQXltYzdFSXNORFFKRVJ5ajdsdWF1TkNnOFdtWFdPCmd0OHIzZHVTazNHV2ZZeGdWclFZSHlGTVpCbUpvNDliRzVzdGcwR01JNUZRQXord3RERlIyaWk2NkVkNzBJOUwKYXJNMHpQZkM3Tk1acmhEcHVseVdVYWNXRDY1V1g1Yys5TnpIMW15MEVrbjJGOWQzNXE1czZRakdTVElMVXlhbwpJUVl5bGU0OVdKdlV4YjN2YTZ1OTVBUHAyWFFVaFEyS09GcGxabncwTVFLQmdRRFN2cDAzYlBvQVlEb3BqWGlxCndxemxKdk9IY2M4V3ZhVytoM0tvVFBLZ1dRZWpvVnNZTFEzM2lMeXdFY0FXaWtoSzE2UjVmTkt5VUFRZ2JDNm4KNTdkcUJ3L1RqYlV2UGR6K0llMnNKN1BlSlpCQktXZUNHNjBOeGgzUDVJcSsxRHVjdExpQTBKdVZyOUlaUzdqSApJOVpUMitDMTNlNkRlZkJaajFDb0ZhemJ1UUtCZ1FESzZCaVkzSk5FYVhmWVpKUzh1NFViVW9KUjRhUURBcmlpCjFGRlEzMDFPOEF0b1A2US9IcjFjbTdBNGZkQ3JoSkxPMFNqWnpldnF4NEVHSnBueG5pZGowL24yTHE3Z2x6Q2UKbVlKZFVVVFo0MkxJNGpWelBlUk1RaGhueW9CTHpmaEFYcEtZSU1NcmpTd1JUcnYyclRpQkhxSEZRbDN6YngvKwptcjdEVWtlR053S0JnRllPdEpDUGxiOVZqQ3F2dEppMmluZkE0aTFyRWcvTlBjT0IrQlkxNWRZSXhRL1NzaW83Cks3cnJRWEg4clo0R3RlS3FFR1h6ek80M3NwZXkxWktIRXVUZklWMVlQcWFkOG9Kc1JHdktncTZ5VkNmbnluYmMKNmx2M2pQRDUrSlpZZ0VkTG5SUXRHM3VTb283bDF2eXE2N2l1enlJMUVGTHNGblBjRENtM1FERXhBb0dBSDQrdQprOGhybDg2WDk2N2RlK1huTkhMSEZwbDBlNHRtME4wWnNPeXJCOFpLMy9KV1NBTXVEVU9pUzRjMmVCZHRCb0orClNqSy9xWXRTeEhRb3FlNmh6ZU5oRkN2Nnc3Q0F2WXEvUG1pdnZ2eWhsd0dvc3I1RHpxRFJUd091cFJ2cXE0aUsKWU9ObnVGU0RNRVlBOHNQSzhEcWxpeHRocGNYNVFnOHI4UkhSVWswQ2dZQlF3WFdQU3FGRElrUWQvdFg3dk1mTwp3WDdWTVFMK1NUVFA4UXNRSFo2djdpRlFOL3g3Vk1XT3BMOEp6TDdIaGdJV3JzdkxlV1pubDh5N1J3WnZIbm9zCkY3dkliUm00L1Y1YzZHeFFQZXk5RXVmWUw4ejRGMWhSeUc2ZjJnWU1jV25NSWpnaUh2dTA3cStuajFORkh4YVkKa2ZSSERia01YaUcybU42REtyL3RtQT09Ci0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
kind: Secret
metadata:
creationTimestamp: "2022-06-10T12:06:22Z"
name: it666-tls
namespace: default
resourceVersion: "2264722"
uid: 16f8a4b6-1600-4ded-8458-b0480ce075ba
type: kubernetes.io/tls配置域名使用证书
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: itlanson-ingress
namespace: default
spec:
tls:
- hosts:
- itlanson.com
secretName: itlanson-tls
rules:
- host: itlanson.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-nginx-svc
port:
number: 80配置好证书,访问域名,就会默认跳转到https
五、限速
Annotations - NGINX Ingress Controller
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-222333
namespace: default
annotations: ##注解
nginx.ingress.kubernetes.io/limit-rps: "1" ### 限流的配置
spec:
defaultBackend: ## 只要未指定的映射路径
service:
name: php-apache
port:
number: 80
rules:
- host: it666.com
http:
paths:
- path: /bbbbb
pathType: Prefix
backend:
service:
name: cluster-service-222
port:
number: 80六、灰度发布-Canary
以前可以使用k8s的Service配合Deployment进行金丝雀部署。原理如下
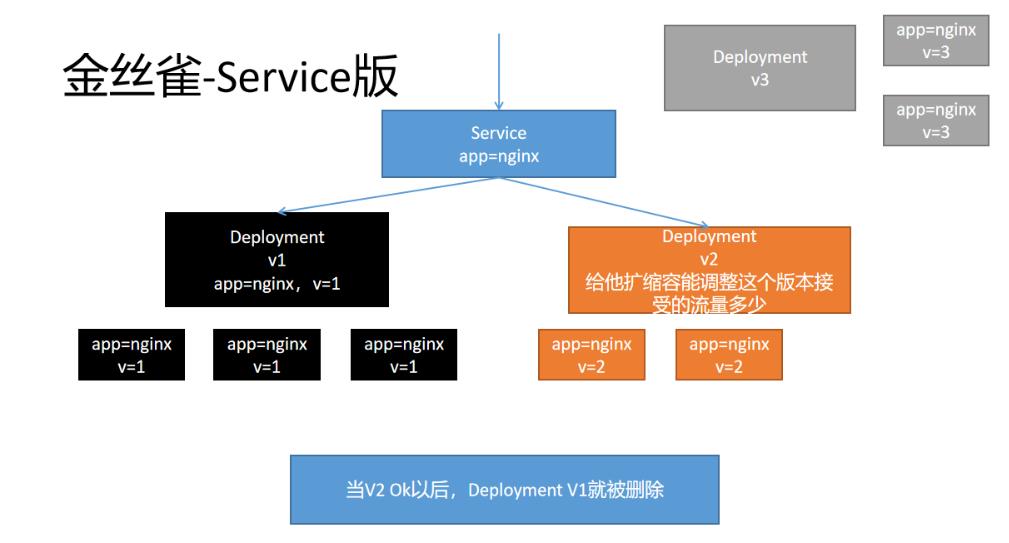
缺点:
-
不能自定义灰度逻辑,比如指定用户进行灰度
现在可以使用Ingress进行灰度。原理如下
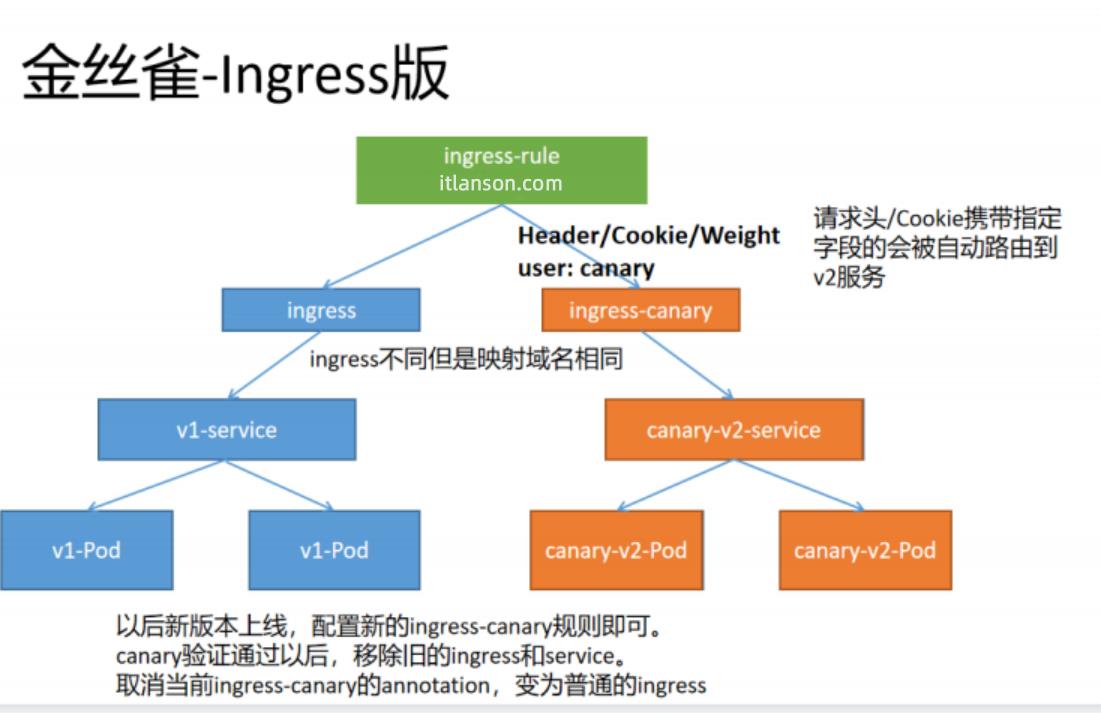
## 使用如下文件部署两个service版本。v1版本返回nginx默认页,v2版本返回 11111
apiVersion: v1
kind: Service
metadata:
name: v1-service
namespace: default
spec:
selector:
app: v1-pod
type: ClusterIP
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: v1-deploy
namespace: default
labels:
app: v1-deploy
spec:
selector:
matchLabels:
app: v1-pod
replicas: 1
template:
metadata:
labels:
app: v1-pod
spec:
containers:
- name: nginx
image: nginx
---
apiVersion: v1
kind: Service
metadata:
name: canary-v2-service
namespace: default
spec:
selector:
app: canary-v2-pod
type: ClusterIP
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: canary-v2-deploy
namespace: default
labels:
app: canary-v2-deploy
spec:
selector:
matchLabels:
app: canary-v2-pod
replicas: 1
template:
metadata:
labels:
app: canary-v2-pod
spec:
containers:
- name: nginx
image: registry.cn-hangzhou.aliyuncs.com/lanson_k8s_images/nginx-test:env-msg七、会话保持-Session亲和性
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#session-affinity https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#session-affinity 第一次访问,ingress-nginx会返回给浏览器一个Cookie,以后浏览器带着这个Cookie,保证访问总是抵达之前的Pod;
https://kubernetes.github.io/ingress-nginx/user-guide/nginx-configuration/annotations/#session-affinity 第一次访问,ingress-nginx会返回给浏览器一个Cookie,以后浏览器带着这个Cookie,保证访问总是抵达之前的Pod;
## 部署一个三个Pod的Deployment并设置Service
apiVersion: v1
kind: Service
metadata:
name: session-affinity
namespace: default
spec:
selector:
app: session-affinity
type: ClusterIP
ports:
- name: session-affinity
port: 80
targetPort: 80
protocol: TCP
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: session-affinity
namespace: default
labels:
app: session-affinity
spec:
selector:
matchLabels:
app: session-affinity
replicas: 3
template:
metadata:
labels:
app: session-affinity
spec:
containers:
- name: session-affinity
image: nginx编写具有会话亲和的ingress
### 利用每次请求携带同样的cookie,来标识是否是同一个会话
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: session-test
namespace: default
annotations:
nginx.ingress.kubernetes.io/affinity: "cookie"
nginx.ingress.kubernetes.io/session-cookie-name: "itlanson-session"
spec:
rules:
- host: it666.com
http:
paths:
- path: / ### 如果以前这个域名下的这个路径相同的功能有配置过,以最后一次生效
pathType: Prefix
backend:
service:
name: session-affinity ###
port:
number: 80- 📢博客主页:https://lansonli.blog.csdn.net
- 📢欢迎点赞 👍 收藏 ⭐留言 📝 如有错误敬请指正!
- 📢本文由 Lansonli 原创,首发于 CSDN博客🙉
- 📢停下休息的时候不要忘了别人还在奔跑,希望大家抓紧时间学习,全力奔赴更美好的生活✨
 开发者涨薪指南
开发者涨薪指南
 48位大咖的思考法则、工作方式、逻辑体系
48位大咖的思考法则、工作方式、逻辑体系
以上是关于云原生 | Kubernetes篇Ingress案例实战的主要内容,如果未能解决你的问题,请参考以下文章
云原生之kubernetes实战在k8s集群下部署ingress对外访问服务