C++程序正向编译Ghidra逆向反编译
Posted 向往生
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了C++程序正向编译Ghidra逆向反编译相关的知识,希望对你有一定的参考价值。
1.需求:
逆向工程师必须先是一个正向开发工程师,如果没有C++/MFC的开发经验,就不会懂得如何逆向分析C++/MFC的程序,本文完成一个helloworld的C++正逆向过程。
2.C++程序源码:
编译环境:visual studio 2022
#include <iostream>
#include <cstdlib>
using namespace std;
int main()
int a;
a = 100;
for (int i = 0; i < a; i++)
cout << "Hello World! " << endl;
system("pause");
return 0;
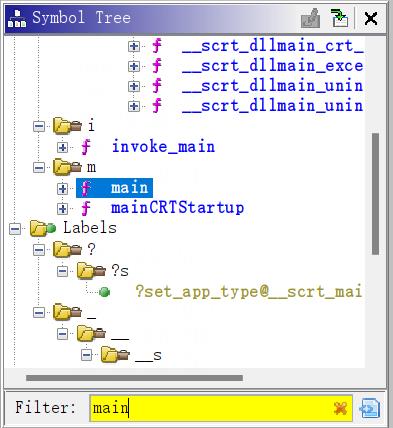
编译完毕后生成exe程序,导入Ghidra,分析完毕后,在symbol tree窗口,输入main查找到主函数位置:
3.Ghidra反编译结果:
int main(int _Argc,char **_Argv,char **_Env)
ulonglong i;
__CheckForDebuggerJustMyCode(&__C0892E22_helloc++@cpp);
for (i = 0; i < 100; i = i + 1)
std::operator<<<std::char_traits<char>_>
((basic_ostream<char,std::char_traits<char>_> *)cout_exref,"Hello World! ");
system("pause");
return 0;
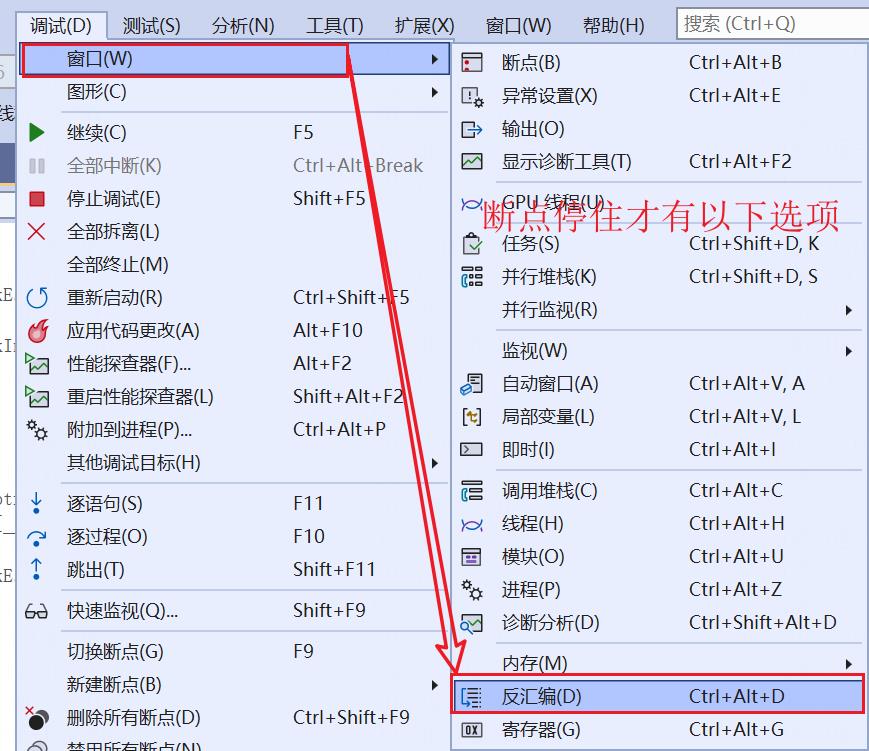
4.Visual studio 里查看汇编代码
在正向开发的过程中,可以在编译器Visual studio里,查看C++代码的汇编代码,在程序中设置断点,F5编译,等程序停住后,才有查看汇编选项:
汇编代码如下:
--- C:\\Users\\paul\\source\\repos\\helloc++\\helloc++\\helloc++.cpp ------------------
1: // helloc++.cpp : 此文件包含 "main" 函数。程序执行将在此处开始并结束。
2: //
3:
4: #include <iostream>
5: #include <cstdlib>
6: using namespace std;
7:
8:
9: int main()
10:
00691D06 00 00 add byte ptr [eax],al
00691D08 00 53 56 add byte ptr [ebx+56h],dl
00691D0B 57 push edi
00691D0C 8D 7D E4 lea edi,[ebp-1Ch]
00691D0F B9 07 00 00 00 mov ecx,7
00691D14 B8 CC CC CC CC mov eax,0CCCCCCCCh
00691D19 F3 AB rep stos dword ptr es:[edi]
00691D1B A1 04 C0 69 00 mov eax,dword ptr [__security_cookie (069C004h)]
00691D20 33 C5 xor eax,ebp
00691D22 89 45 FC mov dword ptr [ebp-4],eax
11: int a;
12: a = 100;
00691D25 C7 45 F4 64 00 00 00 mov dword ptr [a],64h
13: for (int i = 0; i < a; i++)
00691D2C C7 45 E8 00 00 00 00 mov dword ptr [ebp-18h],0
00691D33 EB 09 jmp __$EncStackInitStart+32h (0691D3Eh)
00691D35 8B 45 E8 mov eax,dword ptr [ebp-18h]
00691D38 83 C0 01 add eax,1
00691D3B 89 45 E8 mov dword ptr [ebp-18h],eax
00691D3E 8B 45 E8 mov eax,dword ptr [ebp-18h]
00691D41 3B 45 F4 cmp eax,dword ptr [a]
00691D44 7D 2B jge __$EncStackInitStart+65h (0691D71h)
14:
15: cout << "Hello World! " << endl;
00691D46 8B F4 mov esi,esp
00691D48 68 3C 10 69 00 push offset std::endl<char,std::char_traits<char> > (069103Ch)
00691D4D 68 30 9B 69 00 push offset string "Hello World! " (0699B30h)
00691D52 A1 D4 D0 69 00 mov eax,dword ptr [__imp_std::cout (069D0D4h)]
00691D57 50 push eax
00691D58 E8 4C F4 FF FF call std::operator<<<std::char_traits<char> > (06911A9h)
00691D5D 83 C4 08 add esp,8
00691D60 8B C8 mov ecx,eax
00691D62 FF 15 A0 D0 69 00 call dword ptr [__imp_std::basic_ostream<char,std::char_traits<char> >::operator<< (069D0A0h)]
00691D68 3B F4 cmp esi,esp
00691D6A E8 20 F5 FF FF call __RTC_CheckEsp (069128Fh)
16:
00691D6F EB C4 jmp __$EncStackInitStart+29h (0691D35h)
17: //system("pause");
18: cin >> a;
00691D71 8B F4 mov esi,esp
00691D73 8D 45 F4 lea eax,[a]
00691D76 50 push eax
00691D77 8B 0D DC D0 69 00 mov ecx,dword ptr [__imp_std::cin (069D0DCh)]
00691D7D FF 15 E0 D0 69 00 call dword ptr [__imp_std::basic_istream<char,std::char_traits<char> >::operator>> (069D0E0h)]
00691D83 3B F4 cmp esi,esp
00691D85 E8 05 F5 FF FF call __RTC_CheckEsp (069128Fh)
19: return 0;
00691D8A 33 C0 xor eax,eax
20:
21:
00691D8C 52 push edx
00691D8D 8B CD mov ecx,ebp
00691D8F 50 push eax
00691D90 8D 15 BC 1D 69 00 lea edx,ds:[691DBCh]
00691D96 E8 90 F4 FF FF call @_RTC_CheckStackVars@8 (069122Bh)
00691D9B 58 pop eax
00691D9C 5A pop edx
00691D9D 5F pop edi
00691D9E 5E pop esi
00691D9F 5B pop ebx
00691DA0 8B 4D FC mov ecx,dword ptr [ebp-4]
00691DA3 33 CD xor ecx,ebp
00691DA5 E8 D2 F3 FF FF call @__security_check_cookie@4 (069117Ch)
00691DAA 81 C4 DC 00 00 00 add esp,0DCh
00691DB0 3B EC cmp ebp,esp
00691DB2 E8 D8 F4 FF FF call __RTC_CheckEsp (069128Fh)
00691DB7 8B E5 mov esp,ebp
00691DB9 5D pop ebp
00691DBA C3 ret
00691DBB 90 nop
00691DBC 01 00 add dword ptr [eax],eax
00691DBE 00 00 add byte ptr [eax],al
00691DC0 C4 1D 69 00 F4 FF les ebx,fword ptr ds:[0FFF40069h]
00691DC6 FF ?? ??????
20:
21:
00691DC7 FF 04 00 inc dword ptr [eax+eax]
00691DCA 00 00 add byte ptr [eax],al
00691DCC D0 1D 69 00 61 00 rcr byte ptr ds:[610069h],1 以上是关于C++程序正向编译Ghidra逆向反编译的主要内容,如果未能解决你的问题,请参考以下文章