kali中信息收集相关的命令
Posted 互联网老辛
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了kali中信息收集相关的命令相关的知识,希望对你有一定的参考价值。
1. 域名信息查询命令
1) host && dig
a) host 查看帮助:
┌──(root💀itlaoxin)-[~]
└─# host
Usage: host [-aCdilrTvVw] [-c class] [-N ndots] [-t type] [-W time]
[-R number] [-m flag] [-p port] hostname [server]
-a is equivalent to -v -t ANY (显示DNS详细信息)
-A is like -a but omits RRSIG, NSEC, NSEC3
-c specifies query class for non-IN data (指定查询类型,默认为I/N)
-C compares SOA records on authoritative nameservers (查询指定主机的完整的SOA记录)
-d is equivalent to -v
-l lists all hosts in a domain, using AXFR
-m set memory debugging flag (trace|record|usage)
-N changes the number of dots allowed before root lookup is done
-p specifies the port on the server to query
-r disables recursive processing
-R specifies number of retries for UDP packets
-s a SERVFAIL response should stop query
-t specifies the query type (指定查询域名的信息类型)
-T enables TCP/IP mode
-U enables UDP mode
-v enables verbose output
-V print version number and exit
-w specifies to wait forever for a reply
-W specifies how long to wait for a reply
-4 use IPv4 query transport only (使用IPV4)
-6 use IPv6 query transport only (使用IPV6)
b) dig的相关参数:
└─# dig -help 1 ⨯
Usage: dig [@global-server] [domain] [q-type] [q-class] q-opt
global-d-opt host [@local-server] local-d-opt
[ host [@local-server] local-d-opt [...]]
Where: domain is in the Domain Name System
q-class is one of (in,hs,ch,...) [default: in]
q-type is one of (a,any,mx,ns,soa,hinfo,axfr,txt,...) [default:a]
(Use ixfr=version for type ixfr)
q-opt is one of:
-4 (use IPv4 query transport only)
-6 (use IPv6 query transport only)
-b address[#port] (bind to source address/port) (绑定发出查询的源IP地址)
-c class (specify query class) (指定查询类)
-f filename (batch mode) (批处理模式)
-k keyfile (specify tsig key file) (指定秘钥文件)
-m (enable memory usage debugging)
-p port (specify port number) (指定端口号)
-q name (specify query name)
-r (do not read ~/.digrc)
-t type (specify query type)
-u (display times in usec instead of msec)
-x dot-notation (shortcut for reverse lookups)(反向查找的快捷方式)
-y [hmac:]name:key (specify named base64 tsig key) (指定TSIC秘钥)
使用案例
案例一
以www.geekyunwei.com 为例,我们分别用host和dig来查看:
┌──(root💀itlaoxin)-[~]
└─# host -a geekyunwei.com 1 ⨯
Trying "geekyunwei.com"
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12854
;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;geekyunwei.com. IN ANY
;; ANSWER SECTION:
geekyunwei.com. 180 IN SOA vela.dnspod.net. freednsadmin.dnspod.com. 1611407896 3600 180 1209600 180
geekyunwei.com. 600 IN A 82.156.74.66
geekyunwei.com. 3599 IN NS opponent.dnspod.net.
geekyunwei.com. 3599 IN NS vela.dnspod.net.
Received 156 bytes from fe80::b6f1:8cff:fe0c:1d6f%2#53 in 1036 ms
可以查看到A记录,查询到A记录对应的IP地址。
用dig查看
──(root💀itlaoxin)-[~]
┌──(root💀itlaoxin)-[~]
└─# dig geekyunwei.com
; <<>> DiG 9.16.11-Debian <<>> geekyunwei.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 53320
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;geekyunwei.com. IN A
;; ANSWER SECTION:
geekyunwei.com. 600 IN A 82.156.74.66
;; Query time: 2196 msec
;; SERVER: fe80::b6f1:8cff:fe0c:1d6f%2#53(fe80::b6f1:8cff:fe0c:1d6f%2%2)
;; WHEN: 一 12月 27 08:18:13 CST 2021
;; MSG SIZE rcvd: 48
案例二
┌──(root💀itlaoxin)-[~]
└─# host www.baidu.com
www.baidu.com is an alias for www.a.shifen.com.
www.a.shifen.com has address 110.242.68.4
www.a.shifen.com has address 110.242.68.3
可以看到百度的IP以及alias ip 地址
┌──(root💀itlaoxin)-[~]
└─# dig www.baidu.com
; <<>> DiG 9.16.11-Debian <<>> www.baidu.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 29577
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;www.baidu.com. IN A
;; ANSWER SECTION:
www.baidu.com. 103 IN CNAME www.a.shifen.com.
www.a.shifen.com. 289 IN A 110.242.68.3
www.a.shifen.com. 289 IN A 110.242.68.4
;; Query time: 2012 msec
;; SERVER: fe80::b6f1:8cff:fe0c:1d6f%2#53(fe80::b6f1:8cff:fe0c:1d6f%2%2)
;; WHEN: 一 12月 27 08:23:12 CST 2021
;; MSG SIZE rcvd: 101
┌──(root💀itlaoxin)-[~]
└─#
使用host -t 查看邮件地址
is handled by 20 usmx01.baidu.com.
baidu.com mail is handled by 15 mx.n.shifen.com.
baidu.com mail is handled by 20 jpmx.baidu.com.
baidu.com mail is handled by 20 mx1.baidu.com.
baidu.com mail is handled by 20 mx50.baidu.com.
baidu.com mail is handled by 10 mx.maillb.baidu.com.
使用host -t ns baidu.com 查询baidu.com域的权威域名服务器记录
┌──(root💀itlaoxin)-[~]
└─# host -t ns baidu.com
baidu.com name server dns.baidu.com.
baidu.com name server ns7.baidu.com.
baidu.com name server ns4.baidu.com.
baidu.com name server ns2.baidu.com.
baidu.com name server ns3.baidu.com.
可以看到,一共5个权威域名服务器
使用dig baidu.com +trace 追踪互联网解析baidu.com域的完整过程。
──(root💀itlaoxin)-[~]
└─# dig baidu.com +trace
; <<>> DiG 9.16.11-Debian <<>> baidu.com +trace
;; global options: +cmd
. 897 IN NS f.root-servers.net.
. 897 IN NS i.root-servers.net.
. 897 IN NS g.root-servers.net.
. 897 IN NS h.root-servers.net.
. 897 IN NS m.root-servers.net.
. 897 IN NS a.root-servers.net.
. 897 IN NS b.root-servers.net.
. 897 IN NS k.root-servers.net.
. 897 IN NS l.root-servers.net.
. 897 IN NS j.root-servers.net.
. 897 IN NS c.root-servers.net.
. 897 IN NS d.root-servers.net.
. 897 IN NS e.root-servers.net.
;; Received 239 bytes from 192.168.3.1#53(192.168.3.1) in 4 ms
com. 172800 IN NS a.gtld-servers.net.
com. 172800 IN NS b.gtld-servers.net.
com. 172800 IN NS c.gtld-servers.net.
com. 172800 IN NS d.gtld-servers.net.
com. 172800 IN NS e.gtld-servers.net.
com. 172800 IN NS f.gtld-servers.net.
com. 172800 IN NS g.gtld-servers.net.
com. 172800 IN NS h.gtld-servers.net.
com. 172800 IN NS i.gtld-servers.net.
com. 172800 IN NS j.gtld-servers.net.
com. 172800 IN NS k.gtld-servers.net.
com. 172800 IN NS l.gtld-servers.net.
com. 172800 IN NS m.gtld-servers.net.
com. 86400 IN DS 30909 8 2 E2D3C916F6DEEAC73294E8268FB5885044A833FC5459588F4A9184CF C41A5766
com. 86400 IN RRSIG DS 8 1 86400 20220108170000 20211226160000 14748 . Kv7eGvX/htRlOnH+b7oDUeauCS+4svIQOmRNi+CtZIhhxEYyH/eVGghj 7puyN+8xjtM4ig4yF+uHL40yU6X+Qi3fXXgTRfdO9DpzA2zot2EZ/NBm SvQ9tgQOyZEtsp+lJ7XTgXgtoINMRBE13mmvP2JOhM7gUCYsjqikR9tb GKNp5XLHCrV2pfxaKwkzrE3INllnjiFpaNyGsGIOorR0on3BNz6nK04G 8TBe1rhbsJRUGrGgehlkEKvC0iQ/k8Ogcxd+Bfvxn6ToJ//Pbr1epufI wB+G+JA/vRy1XkbF6W3w7aC6s3fdQMV71ZijBIUxHGKbqkcFa3rhoikl uB7Ahg==
;; Received 1169 bytes from 199.7.83.42#53(l.root-servers.net) in 20 ms
baidu.com. 172800 IN NS ns2.baidu.com.
baidu.com. 172800 IN NS ns3.baidu.com.
baidu.com. 172800 IN NS ns4.baidu.com.
baidu.com. 172800 IN NS ns1.baidu.com.
baidu.com. 172800 IN NS ns7.baidu.com.
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN NSEC3 1 1 0 - CK0Q1GIN43N1ARRC9OSM6QPQR81H5M9A NS SOA RRSIG DNSKEY NSEC3PARAM
CK0POJMG874LJREF7EFN8430QVIT8BSM.com. 86400 IN RRSIG NSEC3 8 2 86400 20211230052358 20211223041358 15549 com. Cejn59yby3+v8HejsHQH+xk/vWuYG5m8gj5xACzw47bDmPffV7BfSC0U qGSEfAsHiGcH3lLeqO8Yd+TW6Qy+fYj5yQMPTpdKG/MVEG/j+K9CoZhj M3bdUC0LHaATbuBMQRIJduiZ7g4NjblnPmIqwsmn+s6OBaVEjzUcoU6p pK5phlm7/XcUn6YlSkUMIP9agnmOV+r6SqiXvAWivbc6fg==
HPVU6NQB275TGI2CDHPDMVDOJC9LNG86.com. 86400 IN NSEC3 1 1 0 - HPVV8SARM2LDLRBTVC5EP1CUB1EF7LOP NS DS RRSIG
HPVU6NQB275TGI2CDHPDMVDOJC9LNG86.com. 86400 IN RRSIG NSEC3 8 2 86400 20211231053230 20211224042230 15549 com. tH1TT8h2clMqY3ZoHHC4GorRlTgYMtROVEBpyExt1eTlHm4g5VX4jakv BxYllbV5e5HyhpvgJWEAkhsTQEsCFtcLRDipKEXSQ8gmA/fxVk1FdNPJ xnmiJjoHhtjiBPky21DqmBAzX0tcGRlfZ0lOlVM3m11rf/HFnUAKTCWn A6oUAZrQNVlb9s3EDwQ6/mHJwQwfmxvS6oxeDhkfKidrrw==
;; Received 757 bytes from 2001:503:d2d::30#53(k.gtld-servers.net) in 180 ms
baidu.com. 600 IN A 220.181.38.251
baidu.com. 600 IN A 220.181.38.148
baidu.com. 86400 IN NS ns2.baidu.com.
baidu.com. 86400 IN NS ns7.baidu.com.
baidu.com. 86400 IN NS ns3.baidu.com.
baidu.com. 86400 IN NS dns.baidu.com.
baidu.com. 86400 IN NS ns4.baidu.com.
;; Received 296 bytes from 220.181.33.31#53(ns2.baidu.com) in 16 ms

。
左边的. 表示根域,一共13台根域服务器,从A到M,信息由192.168.3.1返回,最后尝试从ns2.baidu.con,也就是220.181.33.31服务器获得www.baidu.com 的IP地址, 该域名对应两个地址:
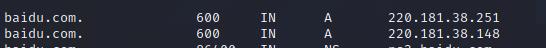
到此解析结束。
以上是关于kali中信息收集相关的命令的主要内容,如果未能解决你的问题,请参考以下文章