Kerberos http身份认证原理及例子
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Kerberos http身份认证原理及例子相关的知识,希望对你有一定的参考价值。
参考技术A4. 特别注意!!这里请求的服务端的hostname一定要和principal的角色名一样(principal组成:用户名/角色@realm域),并配置好相关的hosts,千万不能用ip访问(切记kerberos规则都是用域名的)
CDH6.3.2 开启Kerberos 认证
CDH6.3.2 开启Kerberos 认证
标签(空格分隔): 大数据平台构建
一:如何安装及配置KDC服务
二:如何通过CDH启用Kerberos
- 三:如何登录Kerberos并访问Hadoop相关服务
一:如何安装及配置KDC服务
1.1 系统环境
1.操作系统:CentOS7.5x64
2.CDH6.3.2
3.采用root用户进行操作1.2 KDC服务安装及配置
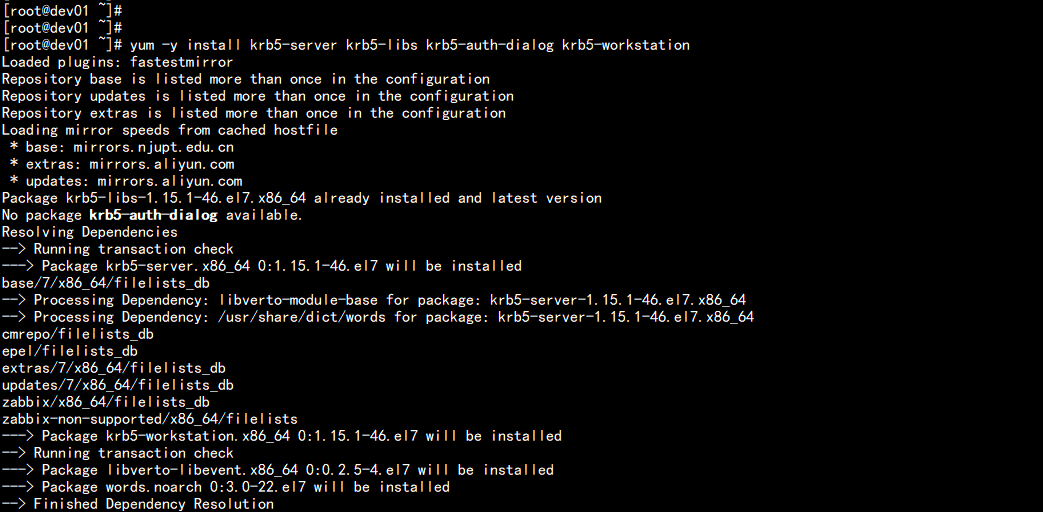
1.在Cloudera Manager服务器上安装KDC服务
yum -y install krb5-server krb5-libs krb5-auth-dialog krb5-workstation
2.修改/etc/krb5.conf配置
vim /etc/krb5.conf
----
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = LANXIN.COM
#default_ccache_name = KEYRING:persistent:%{uid}
[realms]
LANXIN.COM = {
kdc = 192.168.11.160
admin_server = 192.168.11.160
}
[domain_realm]
.lanxin.com = LANXIN.COM
lanxin.com = LANXIN.COM
---
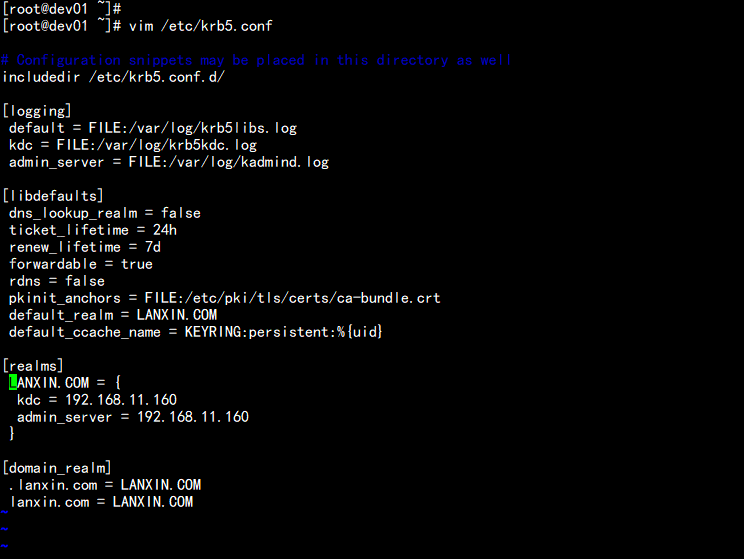
3.修改/var/kerberos/krb5kdc/kadm5.acl配置
vim /var/kerberos/krb5kdc/kadm5.acl
----
*/admin@LANXIN.COM *
----
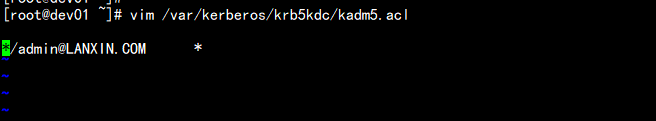
4.修改/var/kerberos/krb5kdc/kdc.conf配置
[kdcdefaults]
kdc_ports = 88
kdc_tcp_ports = 88
[realms]
LANXIN.COM = {
#master_key_type = aes256-cts
max_renewable_life= 7d 0h 0m 0s
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
5.创建Kerberos数据库
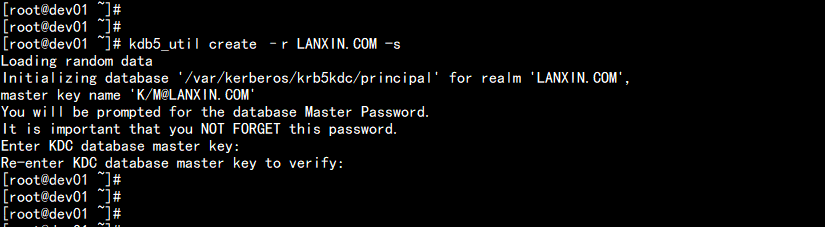
kdb5_util create –r LANXIN.COM -s
密码:LANXIN.COM
---
Loading random data
Initializing database ‘/var/kerberos/krb5kdc/principal‘ for realm ‘LANXIN.COM‘,
master key name ‘K/M@LANXIN.COM‘
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key:
Re-enter KDC database master key to verify:
---
此处需要输入Kerberos数据库的密码。
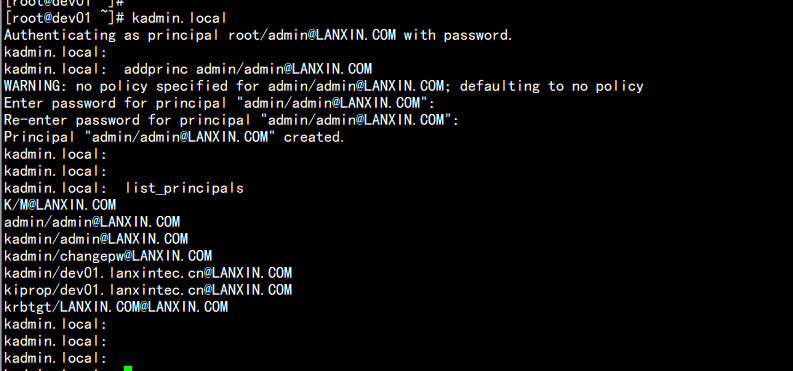
6.创建Kerberos的管理账号
admin/admin@LANXIN.COM
----
Authenticating as principal root/admin@LANXIN.COM with password.
kadmin.local:
kadmin.local: addprinc admin/admin@LANXIN.COM
WARNING: no policy specified for admin/admin@LANXIN.COM; defaulting to no policy
Enter password for principal "admin/admin@LANXIN.COM": 【输入密码为admin】
Re-enter password for principal "admin/admin@LANXIN.COM":
Principal "admin/admin@LANXIN.COM" created.
kadmin.local:
kadmin.local:
kadmin.local: list_principals
K/M@LANXIN.COM
admin/admin@LANXIN.COM
kadmin/admin@LANXIN.COM
kadmin/changepw@LANXIN.COM
kadmin/dev01.lanxintec.cn@LANXIN.COM
kiprop/dev01.lanxintec.cn@LANXIN.COM
krbtgt/LANXIN.COM@LANXIN.COM
----
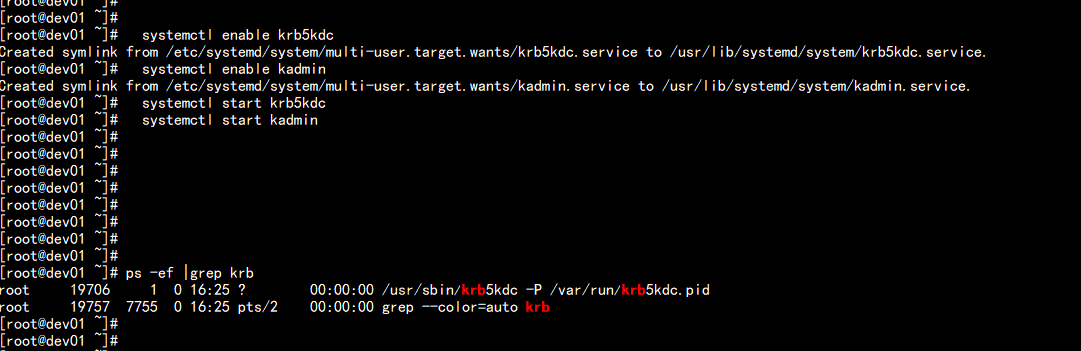
7.将Kerberos服务添加到自启动服务,并启动krb5kdc和kadmin服务
systemctl enable krb5kdc
systemctl enable kadmin
systemctl start krb5kdc
systemctl start kadmin
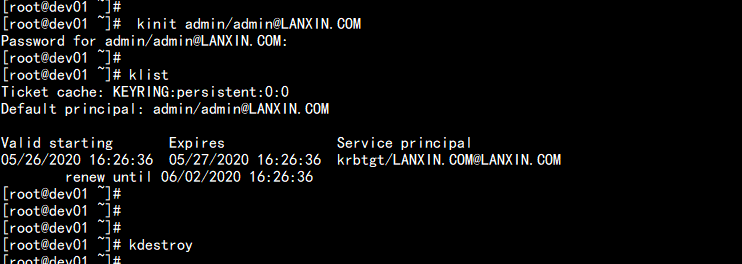
8.测试Kerberos的管理员账号
kinit admin/admin@LANXIN.COM
---
Password for admin/admin@LANXIN.COM:
[root@dev01 ~]#
[root@dev01 ~]# klist
Ticket cache: KEYRING:persistent:0:0
Default principal: admin/admin@LANXIN.COM
Valid starting Expires Service principal
05/26/2020 16:26:36 05/27/2020 16:26:36 krbtgt/LANXIN.COM@LANXIN.COM
renew until 06/02/2020 16:26:36
---
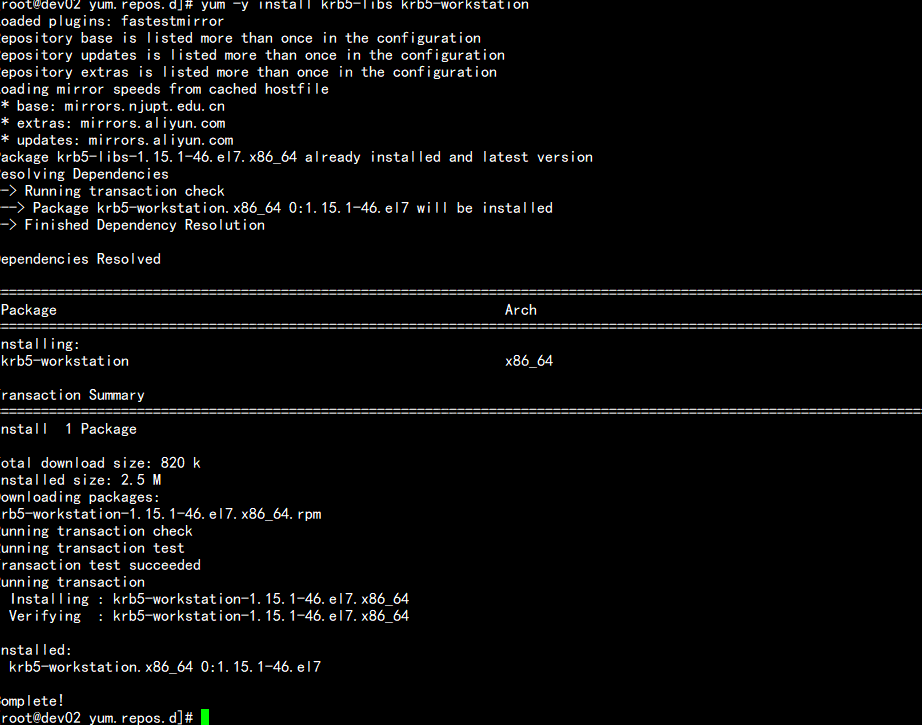
为集群安装所有Kerberos客户端,包括Cloudera Manager
yum -y install krb5-libs krb5-workstation
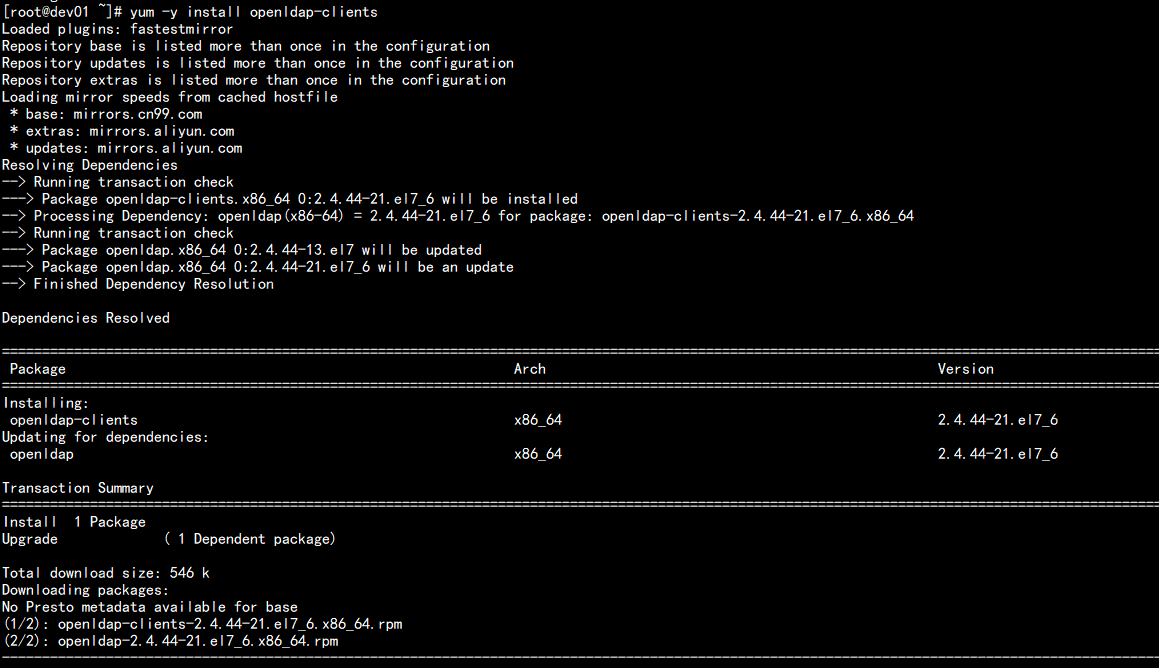
10.在Cloudera Manager Server服务器上安装额外的包
yum -y install openldap-clients
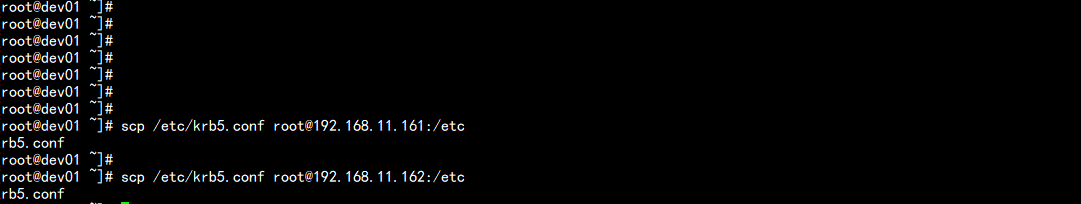
11.将KDC Server上的krb5.conf文件拷贝到所有Kerberos客户端
scp /etc/krb5.conf root@192.168.11.161:/etc
scp /etc/krb5.conf root@192.168.11.162:/etc
二:CDH集群启用Kerberos
1.在KDC中给Cloudera Manager添加管理员账号
cloudera/admin@LANXIN.COM
----
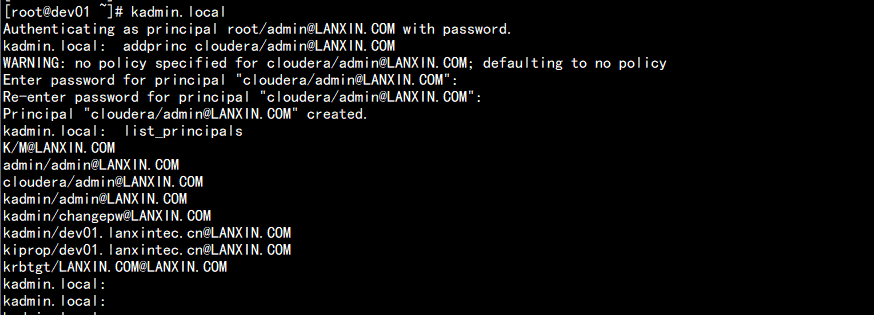
[root@dev01 ~]# kadmin.local
Authenticating as principal root/admin@LANXIN.COM with password.
kadmin.local: addprinc cloudera/admin@LANXIN.COM
WARNING: no policy specified for cloudera/admin@LANXIN.COM; defaulting to no policy
Enter password for principal "cloudera/admin@LANXIN.COM": [密码:cloudera]
Re-enter password for principal "cloudera/admin@LANXIN.COM":
Principal "cloudera/admin@LANXIN.COM" created.
kadmin.local: list_principals
K/M@LANXIN.COM
admin/admin@LANXIN.COM
cloudera/admin@LANXIN.COM
kadmin/admin@LANXIN.COM
kadmin/changepw@LANXIN.COM
kadmin/dev01.lanxintec.cn@LANXIN.COM
kiprop/dev01.lanxintec.cn@LANXIN.COM
krbtgt/LANXIN.COM@LANXIN.COM
----
2.进入Cloudera Manager的“管理”->“安全”界面
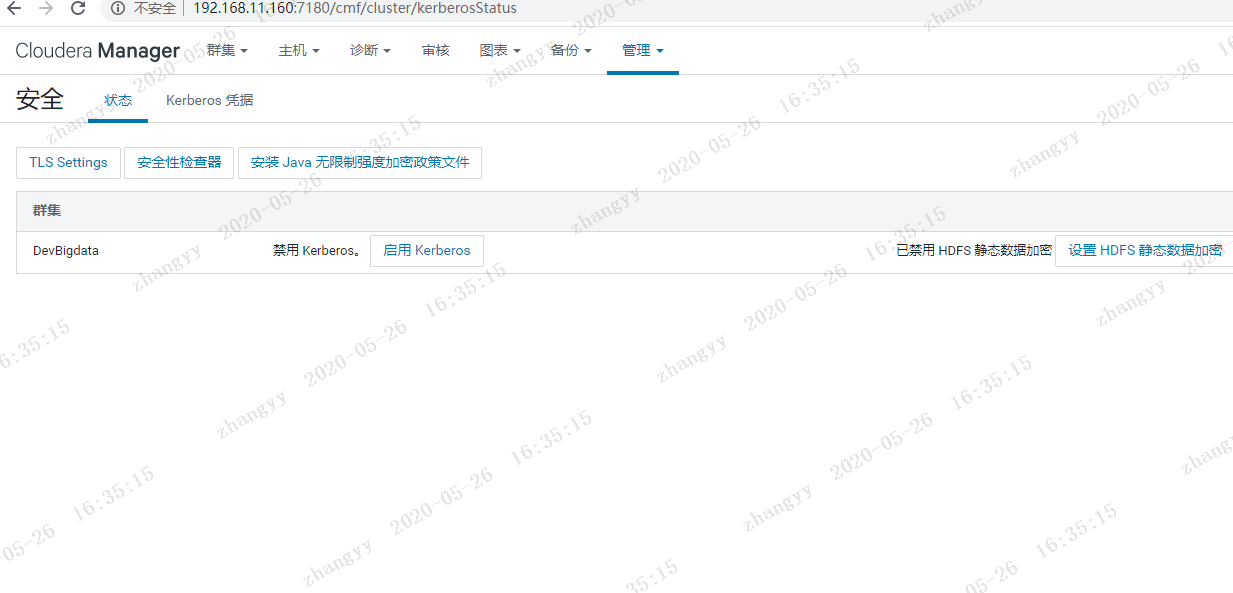
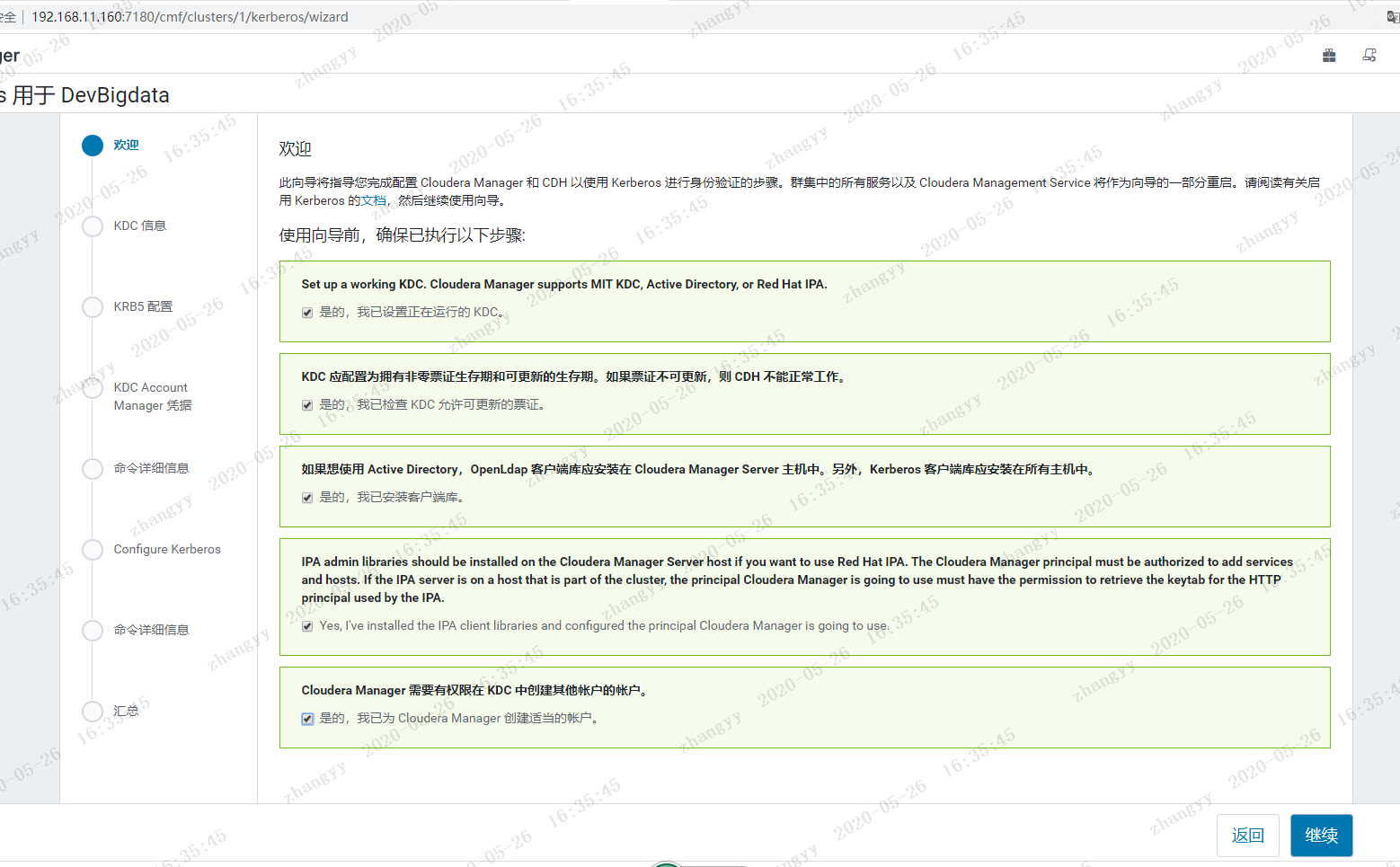
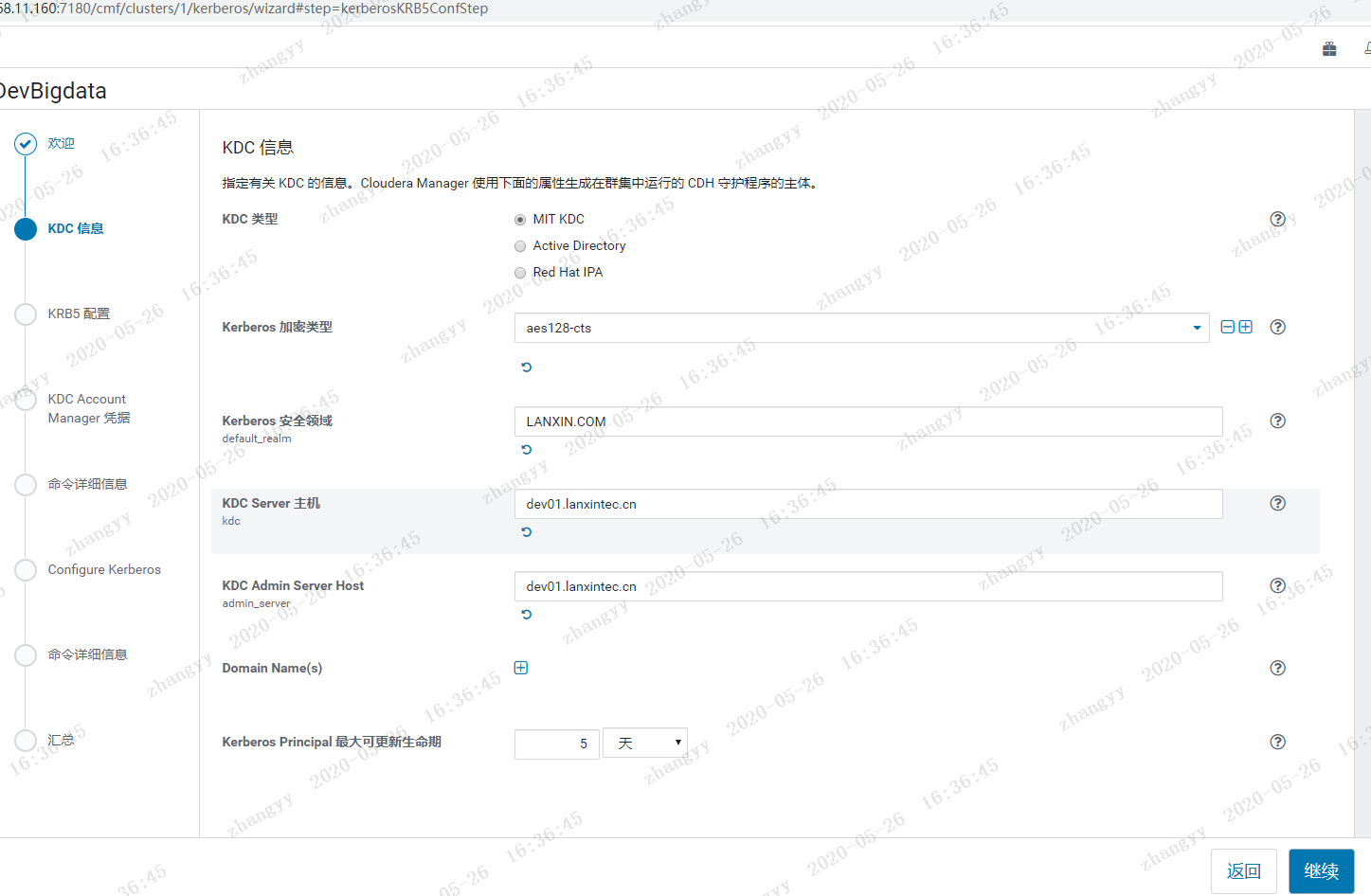
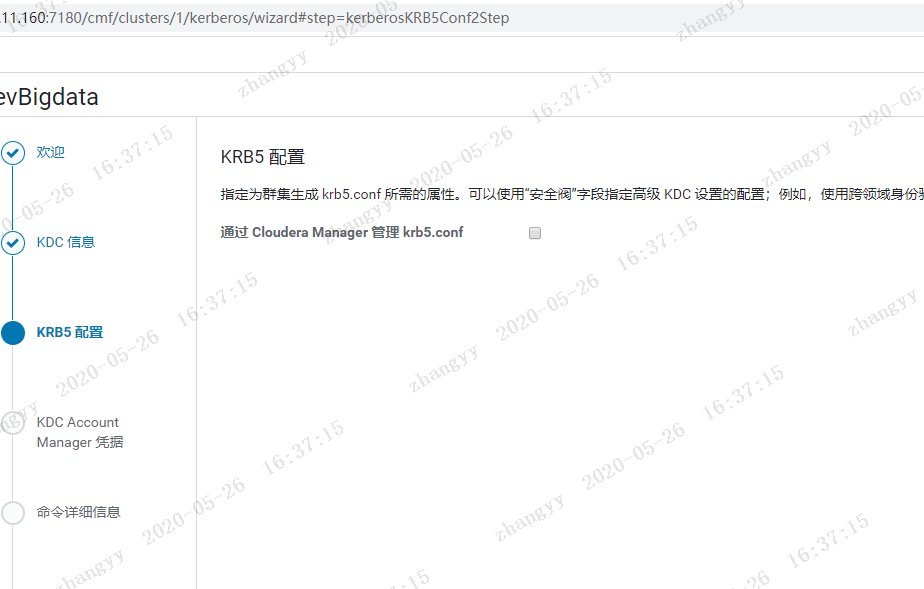

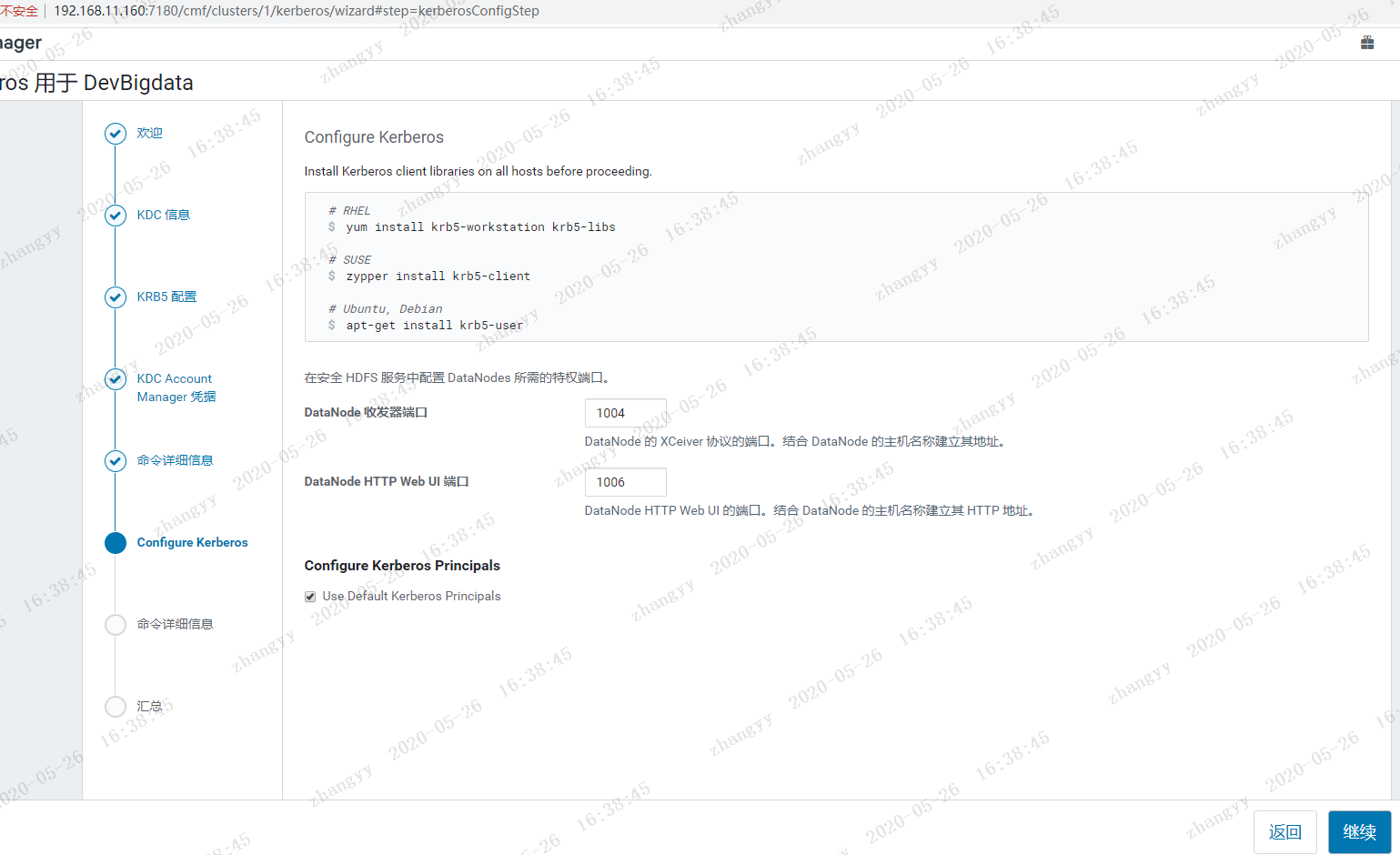
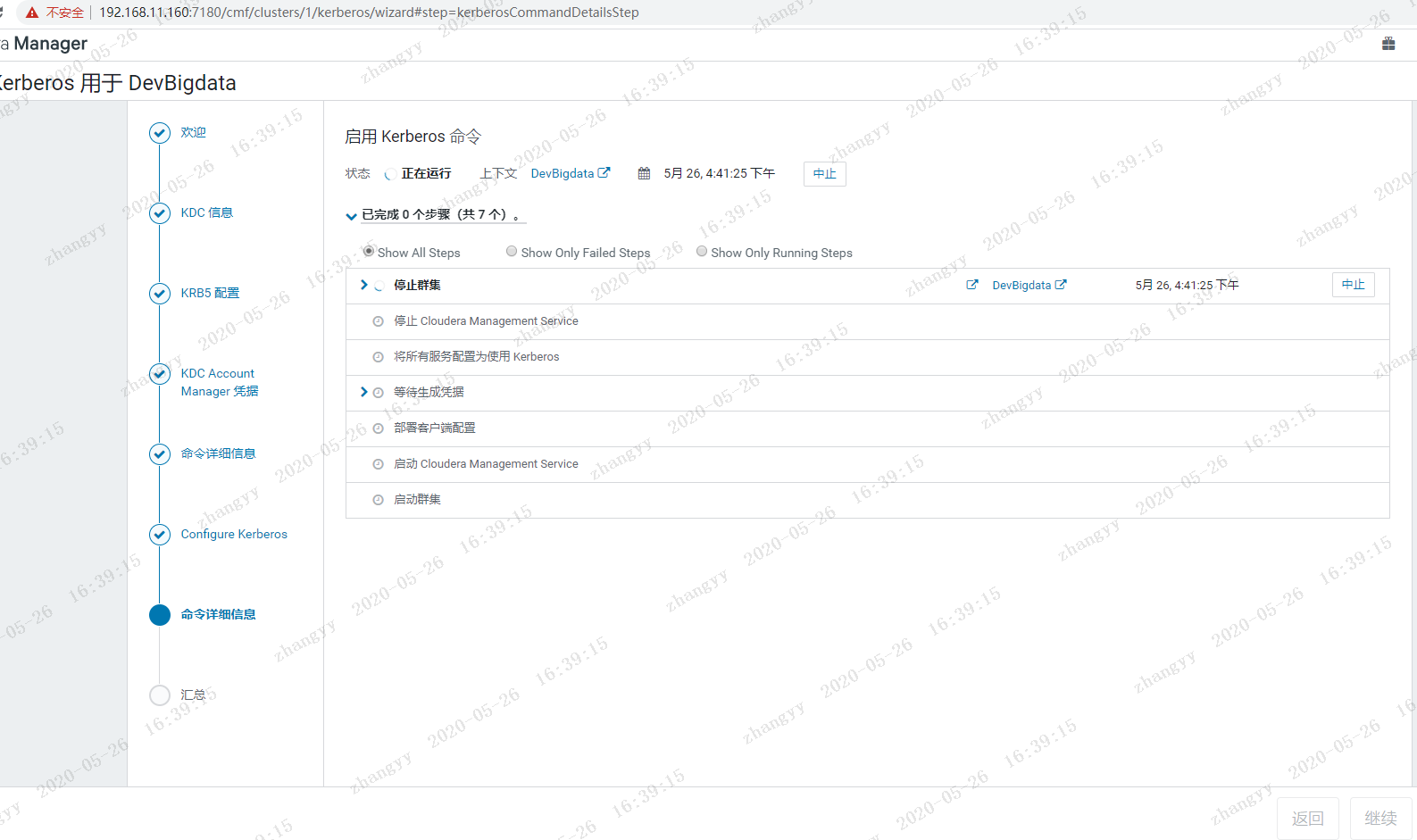
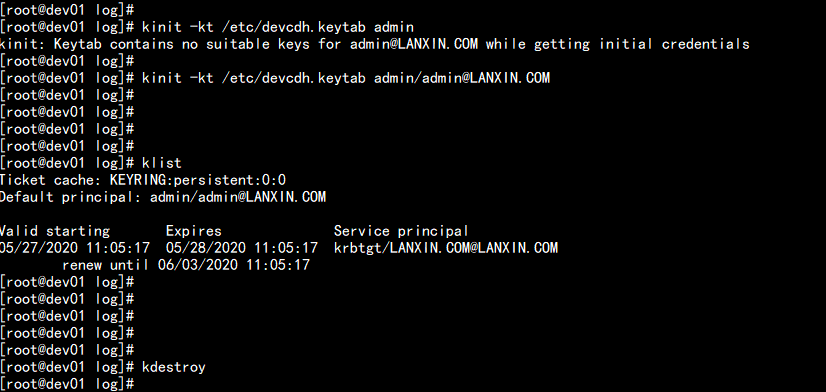
使用 xst -k 命令:将所有的principal 导入到一个 /etc/devcdh.keytab 测试
kadminl.local
xst -k /etc/devcdh.keytab admin/admin@LANXIN.COM
xst -k /etc/devcdh.keytab cloudera/admin@LANXIN.COM
xst -k /etc/devcdh.keytab hdfs/dev01.lanxintec.cn@LANXIN.COM
.......
以上是关于Kerberos http身份认证原理及例子的主要内容,如果未能解决你的问题,请参考以下文章