漏洞扫描器AWVS扫描器简单分析
Posted 区块链市场观察家
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了漏洞扫描器AWVS扫描器简单分析相关的知识,希望对你有一定的参考价值。
文章目录
0x01 前言
0x02 抓包分析
简单抓包看了下,值得学习的一点:发送10个左右请求,计算站点的平均响应时间。
这么抓包分析目的性偏弱,上网找到一些相关资料,还是站在巨人的肩膀上进行学习吧。
从自动发包的请求来看,手动抓包并重放的方式,会影响AWVS的请求内容。抓包重放的方式,参考价值不大。
手动抓包并重放(AWVS显示发送了6个请求)(参考价值不大)
抓包方式:手动拦截请求包并重放。
第一个请求包
GET / HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第二个请求包
GET /p1KaLmIg2kB7fZp5 HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第三个请求包:GET /?gGBw=vsCx&firc=<> HTTP/1.1
第四个:GET / HTTP/1.1
第五个:GET /p1KaLmIg2kB7fZp5 HTTP/1.1
第六个:GET /?gGBw=vsCx&firc=<> HTTP/1.1
第七个:GET /p1KaLmIg2kB7fZp5 HTTP/1.1
第8个:GET / HTTP/1.1
第9个:GET /p1KaLmIg2kB7fZp5 HTTP/1.1
第10个:GET /?gGBw=vsCx&firc=<> HTTP/1.1
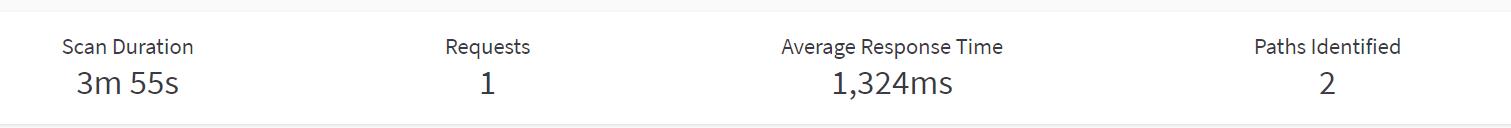
此时AWVS扫描页面:请求数量是1,计算了平均响应时间。
第11个请求包,服务器返回404
POST / HTTP/1.1
Content-Type: application/json
Accept: application/json
Accept-Encoding: gzip, deflate
Content-Length: 737
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
"operationName":"IntrospectionQuery","variables":,"query":"query IntrospectionQuery __schema queryType name mutationType name types ...FullType fragment FullType on __Type kind name description fields(includeDeprecated: false) name description args ...InputValue type ...TypeRef inputFields ...InputValue interfaces ...TypeRef enumValues(includeDeprecated: false) name description possibleTypes ...TypeRef fragment InputValue on __InputValue name description type ...TypeRef defaultValue fragment TypeRef on __Type kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name "
第12个请求包,服务器返回404
POST /graphql HTTP/1.1
Content-Type: application/json
Accept: application/json
Accept-Encoding: gzip, deflate
Content-Length: 737
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
"operationName":"IntrospectionQuery","variables":,"query":"query IntrospectionQuery __schema queryType name mutationType name types ...FullType fragment FullType on __Type kind name description fields(includeDeprecated: false) name description args ...InputValue type ...TypeRef inputFields ...InputValue interfaces ...TypeRef enumValues(includeDeprecated: false) name description possibleTypes ...TypeRef fragment InputValue on __InputValue name description type ...TypeRef defaultValue fragment TypeRef on __Type kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name "
第13个:GET / HTTP/1.1
第14个,探测8161端口,伪造身份验证字段Authorization
GET /admin/ HTTP/1.1
Authorization: Basic YWRtaW46YWRtaW4=(base64解密结果是admin:admin)
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1:8161
Connection: close
第15个:GET /vYyxCPJNGO.jsp
第16个:GET /bal
第17个:伪造Referer字段
GET /ad.php HTTP/1.1
Referer: http://127.0.0.1/
Host: 127.0.0.1
第18个:伪造Referer字段
GET /adminer.php HTTP/1.1
Referer: http://127.0.0.1/
Host: 127.0.0.1
第19-22个:伪造Referer字段,同第17和18个
/_adminer.php
/Adminer.php
/ad.php
第23个:探测8161端口
GET /jobmanager/logs/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fetc%252fshells HTTP/1.1
Host: 127.0.0.1:8081
第24个:访问bxss.me域名进行认证
POST /ng/auth HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
Content-Length: 57
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: bxss.me
Connection: close
user_id=009247&token=f61f2d2d-c11e-461d-8469-0c4924bdc4a2
第25个:
POST / HTTP/1.1
Content-Type: application/json
Accept: application/json
Accept-Encoding: gzip, deflate
Content-Length: 737
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
"operationName":"IntrospectionQuery","variables":,"query":"query IntrospectionQuery __schema queryType name mutationType name types ...FullType fragment FullType on __Type kind name description fields(includeDeprecated: false) name description args ...InputValue type ...TypeRef inputFields ...InputValue interfaces ...TypeRef enumValues(includeDeprecated: false) name description possibleTypes ...TypeRef fragment InputValue on __InputValue name description type ...TypeRef defaultValue fragment TypeRef on __Type kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name "
第26个:POST数据等等都与第25个相同
POST /graphql
第27个:GET /bal
第28个:GET /adminer.php
第29个:GET /
第30个:GET /Adminer.php,伪造Referer头
第31-32个:同上开始进行目录遍历,伪造Referer头
GET /_adminer.php
GET /ad.php
第33个:GET /vYyxCPJNGO.jsp
第34个:与之前数据包重复
POST / HTTP/1.1
Content-Type: application/json
Accept: application/json
Accept-Encoding: gzip, deflate
Content-Length: 737
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
"operationName":"IntrospectionQuery","variables":,"query":"query IntrospectionQuery __schema queryType name mutationType name types ...FullType fragment FullType on __Type kind name description fields(includeDeprecated: false) name description args ...InputValue type ...TypeRef inputFields ...InputValue interfaces ...TypeRef enumValues(includeDeprecated: false) name description possibleTypes ...TypeRef fragment InputValue on __InputValue name description type ...TypeRef defaultValue fragment TypeRef on __Type kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name ofType kind name "
第35个:与第34个相似,POST /graphql
第36个:GET /
第37个:GET /bal
第38-42个:伪造Referer头
GET /ad.php
GET /Adminer.php
GET /ad.php
GET /_adminer.php
GET /adminer.php
第43-44个:
GET /vYyxCPJNGO.jsp
GET /7DB6s5TmTI.php
第45个:
GET / HTTP/1.1
Max-Forwards: 0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第46-54个:伪造Referer头
GET /adminer-4.3.1-mysql.php
GET /adminer-4.3.0-mysql-en.php
GET /adminer-4.3.1-mysql-en.php
GET /adminer-4.3.0-en.php
GET /adminer-4.3.1-en.php
GET /adminer-4.3.1.php
GET /adminer-4.3.0-mysql.php
GET /adminer-4.3.0.php
GET /adminer-4.3.1.php
第55个
GET / HTTP/1.1
Max-Forwards: 0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第56-60个:伪造Referer头
GET /adminer-4.3.1-mysql.php
GET /adminer-4.3.0-mysql-en.php
GET /adminer-4.3.1-mysql-en.php
GET /adminer-4.3.0-mysql.php
GET /adminer-4.3.1-en.php
第61个:
GET /7DB6s5TmTI.php HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第62-63个:伪造Referer头
GET /adminer-4.3.0.php
GET /adminer-4.3.0-en.php
第64个:
GET / HTTP/1.1
Max-Forwards: 0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4512.0 Safari/537.36
Host: 127.0.0.1
Connection: close
第65-72个:伪造Referer头
GET /adminer-4.3.0-en.php
GET /adminer-4.3.1-mysql-en.php
GET /adminer-4.3.1-mysql.php
GET /adminer-4.3.1.php
GET /adminer-4.3.1-en.php
GET /adminer-4.3.0-mysql.php
GET /adminer-4.3.0.php
GET /adminer-4.3.0-mysql-en.php
第73个:GET /7DB6s5TmTI.php。
此时AWVS显示页面
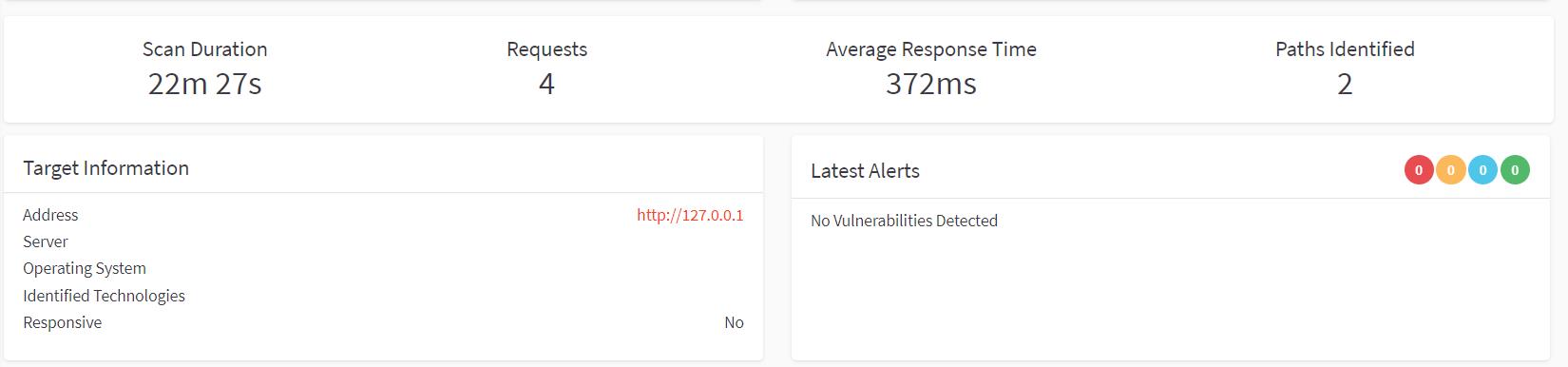
暂停扫描任务,下班。
通过发包历史查看请求
Burpsuite支持查看 HTTP history,故无需手动抓包重放,查看历史就能看到扫描器的每个请求。
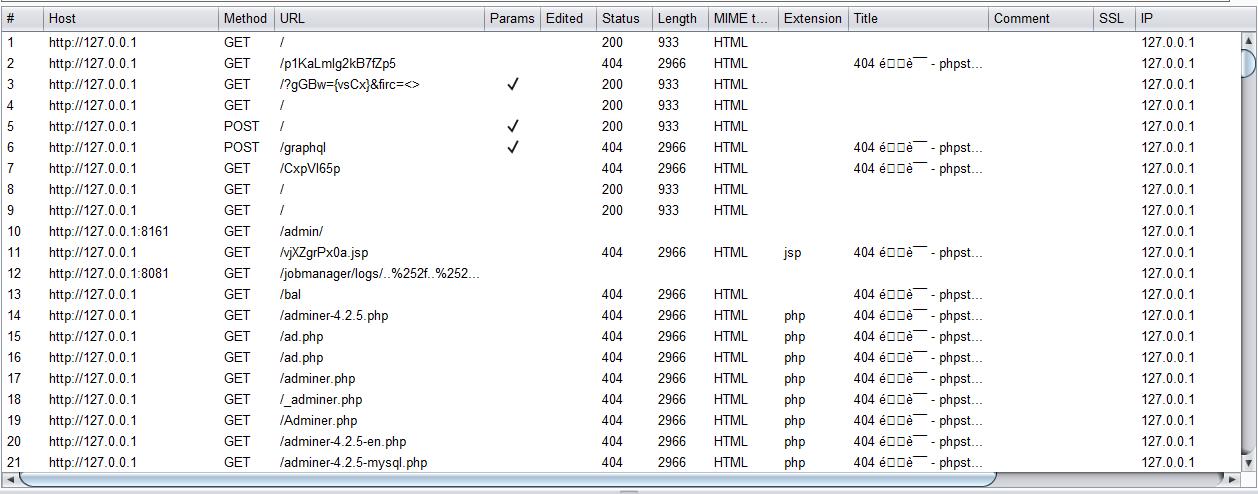
请求数量:截至到暂停扫描任务,一共发送了17000+个请求。
从请求的URL来看,也是目录枚举爬取+Fuzz扫描的方式。目前看,大多数Web扫描器都是基于这样的一种模式。
0x03 小结
AWVS 可借鉴的内容,参考文章中提到一些。
总体对个人的启发如下,当下可以考虑先编写Golang实现的目录枚举和页面链接提取两个工作,然后考虑对枚举和提取的URL进行mark分类。
- 不可或缺的目录枚举工作
- URL的分类和专门扫描工作
以上是关于漏洞扫描器AWVS扫描器简单分析的主要内容,如果未能解决你的问题,请参考以下文章