centos7离线升级openssh,漏洞修复
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了centos7离线升级openssh,漏洞修复相关的知识,希望对你有一定的参考价值。
参考技术A yum -y install xinetd telnet-server配置/etc/xinetd.d/telnet
cat > /etc/xinetd.d/telnet <<eof p=""> </eof>
service telnet
disable = yes
flags = REUSE
socket_type = stream
wait = no
user = root
server = /usr/sbin/in.telnetd
log_on_failure += USERID
EOF
配置telnet登录的终端类型
cat >> /etc/securetty <<eof p=""> </eof>
pts/0
pts/1
pts/2
pts/3
EOF
启动telnet
systemctl enable xinetd --now
systemctl enable telnet.socket --now
wget http://ftp.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-8.8p1.tar.gz
wget https://www.openssl.org/source/openssl-1.1.1j.tar.gz --no-check-certificate
wget http://www.zlib.net/zlib-1.2.12.tar.gz
tar -zxvf zlib-1.2.12.tar.gz
cd zlib-1.2.12
./configure --prefix=/usr/local/zlib
make && make install
tar -zxvf openssl-1.1.1j.tar.gz
cd openssl-1.1.1j
./config --prefix=/usr/local/ssl -d shared
make && make install
echo '/usr/local/ssl/lib' >> /etc/ld.so.conf
ldconfig -v
openssl version -a
tar -zxvf openssh-8.8p1.tar.gz
cd openssh-8.8p1
./configure --prefix=/usr/local/openssh --with-zlib=/usr/local/zlib --with-ssl-dir=/usr/local/ssl
make && make install
配置文件备份和修改
#sshd_config文件修改
echo 'PermitRootLogin yes' >>/usr/local/openssh/etc/sshd_config
echo 'PubkeyAuthentication yes' >>/usr/local/openssh/etc/sshd_config
echo 'PasswordAuthentication yes' >>/usr/local/openssh/etc/sshd_config
# 备份原有文件,并将新的配置复制到指定目录
mv /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
cp /usr/local/openssh/etc/sshd_config /etc/ssh/sshd_config
mv /usr/sbin/sshd /usr/sbin/sshd.bak
cp /usr/local/openssh/sbin/sshd /usr/sbin/sshd
mv /usr/bin/ssh /usr/bin/ssh.bak
cp /usr/local/openssh/bin/ssh /usr/bin/ssh
mv /usr/bin/ssh-keygen /usr/bin/ssh-keygen.bak
cp /usr/local/openssh/bin/ssh-keygen /usr/bin/ssh-keygen
mv /etc/ssh/ssh_host_ecdsa_key.pub /etc/ssh/ssh_host_ecdsa_key.pub.bak
cp /usr/local/openssh/etc/ssh_host_ecdsa_key.pub /etc/ssh/ssh_host_ecdsa_key.pub
# 修改systemd参数(去掉Type或改为Type=simple)
vim /usr/lib/systemd/system/sshd.service
[Unit]
Description=OpenSSH server daemon
Documentation=man:sshd(8) man:sshd_config(5)
After=network.target sshd-keygen.service
Wants=sshd-keygen.service
[Service]
#Type=notify
Type=simple
EnvironmentFile=/etc/sysconfig/sshd
ExecStart=/usr/sbin/sshd -D $OPTIONS
ExecReload=/bin/kill -HUP $MAINPID
KillMode=process
Restart=on-failure
RestartSec=42s
[Install]
WantedBy=multi-user.target
重启sshd服务
systemctl daemon-reload
systemctl restart sshd
systemctl status sshd
# 验证是否升级成功
ssh -V
OpenSSH漏洞修复——Ubuntu系统
OpenSSH 升级加固实例
(一) 升级条件准备
² 关闭防火墙
# ufw disable
² 安装与启用telnet
开启telnet server,以防止升级OpenSSH时导致远程连接异常,具体Telnet服务安装与开启命令操作如下。
# apt-get install -y openbsd-inetd
# apt-get install -y telnetd
# service openbsd-inetd start
² 下载相关升级包
# wget https://cloudflare.cdn.openbsd.org/pub/OpenBSD/OpenSSH/portable/openssh-7.4p1.tar.gz --no-check-certificate
# wget http://www.zlib.net/zlib-1.2.11.tar.gz
# wget https://www.openssl.org/source/openssl-1.0.2k.tar.gz
² 安装zlib依赖库
# tar zxvf zlib-1.2.11.tar.gz
# cd zlib-1.2.11
# ./configure
# make && make install
# echo "/usr/local/lib" >> /etc/ld.so.conf
# ldconfig
² 添加普通账户
# useradd iflytek
# passwd iflytek
(二) OpenSSL升级
# tar zxvf openssl-1.0.2k.tar.gz
# cd openssl-1.0.2k
# ./config shared -fPIC
# make && make install
# echo "/usr/local/ssl/lib " >> /etc/ld.so.conf
# ldconfig
# rm -rf /usr/bin/openssl
# ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl
# openssl version
(三) OpenSSH升级
使用命令“telnet IP”远程连接服务器,关闭SSH服务以便升级。
# 停止sshd服务
# service sshd stop
# apt安装libpam0g-dev
# apt-get install libpam0g-dev # 缺少libpam0g-dev会报错
# 删除原ssh中的相关配置文件
# rm -rf /etc/ssh /usr/bin/scp /usr/bin/sftp /usr/bin/ssh* /usr/sbin/sshd
# rm -rf /lib/x86_64-linux-gnu/libssl.so.1.0.0
# rm -rf /lib/x86_64-linux-gnu/libcrypto.so.1.0.0
# cp /usr/local/ssl/lib/libssl.so.1.0.0 /lib/x86_64-linux-gnu/
# cp /usr/local/ssl/lib/libcrypto.so.1.0.0 /lib/x86_64-linux-gnu/
# 解压新版openssh并编译安装
# tar zxvf openssh-7.4p1.tar.gz
# cd openssh-7.4p1
# ./configure --prefix=/usr/local/ssh --sysconfdir=/etc/ssh --with-md5-passwords --with-pam --with-ssl-dir=/usr/local/ssl --mandir=/usr/share/man --with-zlib=/usr/local/lib --with-privsep-path=/var/empty --with-privsep-user=sshd --with-ssl-engine
# make && make install
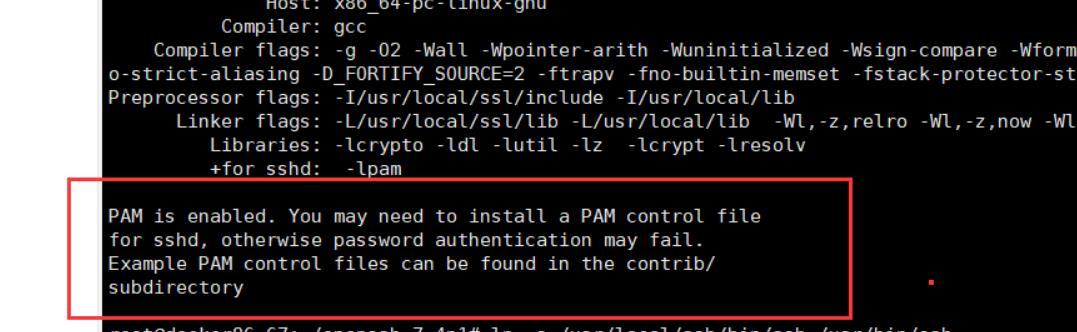
如果遇到这个错误,说明pam没装,需要装下:apt-get install pam
# 创建新版ssh服务的相关软链接
# ln -s /usr/local/ssh/bin/ssh /usr/bin/ssh
# ln -s /usr/local/ssh/bin/scp /usr/bin/scp
# ln -s /usr/local/ssh/bin/sftp /usr/bin/sftp
# ln -s /usr/local/ssh/bin/ssh-add /usr/bin/ssh-add
# ln -s /usr/local/ssh/bin/ssh-agent /usr/bin/ssh-agent
# ln -s /usr/local/ssh/bin/ssh-keygen /usr/bin/ssh-keygen
# ln -s /usr/local/ssh/bin/ssh-keyscan /usr/bin/ssh-keyscan
# ln -s /usr/local/ssh/sbin/sshd /usr/sbin/sshd
#配置允许root远程使用ssh登录(建议使用普通账号作为远程运维登录使用,不要开启root远程登录)
# vi /etc/ssh/sshd_config
去除“#PermitRootLogin prohibit-password”中注释,并修改“prohibit-password”为“yes”,最后保存退出;
# service sshd start
如果出错按照提示操作
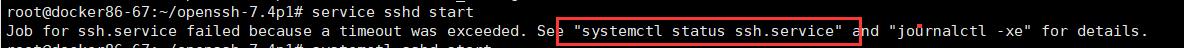
# ssh -V
以上是关于centos7离线升级openssh,漏洞修复的主要内容,如果未能解决你的问题,请参考以下文章