Rsyslog 收集tomcat日志
Posted
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了Rsyslog 收集tomcat日志相关的知识,希望对你有一定的参考价值。
参考技术A 2台liunx机器,并且 开通514 端口
- 3.17.190.209 Server
- 3.21.75.99 Client
tomcat
- apache-tomcat-8.5.60
property ( in English)
Message Properties:
These are extracted by rsyslog parsers from the original message. All message properties start with a letter.
The following message properties exist:
msg
the MSG part of the message (aka “the message” ; ))
rawmsg
the message excactly as it was received from the socket. Should be useful for debugging.
hostname
hostname from the message
source
alias for HOSTNAME
fromhost
hostname of the system the message was received from (in a relay chain, this is the system immediately in front of us and not necessarily the original sender). This is a DNS-resolved name, except if that is not possible or DNS resolution has been disabled.
fromhost-ip
The same as fromhost, but alsways as an IP address. Local inputs (like imklog) use 127.0.0.1 in this property.
syslogtag
TAG from the message
programname
the “static” part of the tag, as defined by BSD syslogd. For example, when TAG is “named[12345]”, programname is “named”.
pri
PRI part of the message - undecoded (single value)
pri-text
the PRI part of the message in a textual form with the numerical PRI appended in brackes (e.g. “local0.err<133>”)
iut
the monitorware InfoUnitType - used when talking to a MonitorWare backend (also for Adiscon LogAnalyzer)
syslogfacility
the facility from the message - in numerical form
syslogfacility-text
the facility from the message - in text form
syslogseverity
severity from the message - in numerical form
syslogseverity-text
severity from the message - in text form
syslogpriority
an alias for syslogseverity - included for historical reasons (be careful: it still is the severity, not PRI!)
syslogpriority-text
an alias for syslogseverity-text
timegenerated
timestamp when the message was RECEIVED. Always in high resolution
timereported
timestamp from the message. Resolution depends on what was provided in the message (in most cases, only seconds)
timestamp
alias for timereported
protocol-version
The contents of the PROTCOL-VERSION field from IETF draft draft-ietf-syslog-protcol
structured-data
The contents of the STRUCTURED-DATA field from IETF draft draft-ietf-syslog-protocol
app-name
The contents of the APP-NAME field from IETF draft draft-ietf-syslog-protocol
procid
The contents of the PROCID field from IETF draft draft-ietf-syslog-protocol
msgid
The contents of the MSGID field from IETF draft draft-ietf-syslog-protocol
inputname
The name of the input module that generated the message (e.g. “imuxsock”, “imudp”). Note that not all modules necessarily provide this property. If not provided, it is an empty string. Also note that the input module may provide any value of its liking. Most importantly, it is not necessarily the module input name. Internal sources can also provide inputnames. Currently, “rsyslogd” is defined as inputname for messages internally generated by rsyslogd, for example startup and shutdown and error messages. This property is considered useful when trying to filter messages based on where they originated - e.g. locally generated messages (“rsyslogd”, “imuxsock”, “imklog”) should go to a different place than messages generated somewhere.
System Properties:
These properties are provided by the rsyslog core engine. They are not related to the message. All system properties start with a dollar-sign.
For example, timereported contains the timestamp from the message. Depending on how long the message was in the relay chain, this can be quite old. In contrast, $now is the system time when the message is being processed. Depending on your needs, you need one or the other. Usually, the message-based timestamp is the more important one, but that really depdends on the use case.
The following system properties exist:
$bom
The UTF-8 encoded Unicode byte-order mask (BOM). This may be useful in templates for RFC5424 support, when the character set is know to be Unicode.
$now
The current date stamp in the format YYYY-MM-DD
$year
The current year (4-digit)
$month
The current month (2-digit)
$day
The current day of the month (2-digit)
$hour
The current hour in military (24 hour) time (2-digit)
$hhour
The current half hour we are in. From minute 0 to 29, this is always 0 while from 30 to 59 it is always 1.
HHOUR, but values range from 0 to 3 (for the four quater hours that are in each hour)
$minute
The current minute (2-digit)
$myhostname
The name of the current host as it knows itself (probably useful for filtering in a generic way)
Rsyslog日志收集服务并结合Loganalyzer工具展示
一、日志概述
1、rsyslog简介
syslog是日志收集存储系统,负责记录遵守此服务的内核、程序的日志信息。一般记录为:“日期时间,主机,进程:事件”。syslog不仅可以记录本地的系统日志,也可以通过tcp, udp协议记录远程主机的程序日志信息。
syslog:系统日志,是一种服务,有两个进程
syslogd:记录应用程序相关的日志
klogd:记录内核相关的日志
rsyslog:是syslog的升级版,使用多线程并发记录本地或远程日志,支持存储日志信息在MySQL,PGSQL, Oracle等RDBMS中。同时拥有强大的过滤器功能,可以对日志中任意内容进行过滤。
rsyslog是CentOS 6以后的系统使用的日志系统,与之前的syslog日志系统相比,具有以下优点:
支持多线程
支持TCP、SSL、TLS、RELP等协议
强大的过滤器,可实现过滤日志信息中的任意部分
支持自定义输出格式
适用于企业级别日志记录需求
模块化
日志的记录格式:
日期时间 主机 进程[pid]:事件内容
2、rsyslog的一些概念
系统上的应用程序指定某一信道记录日志,信道默认已经设定了日志的记录级别,一旦应用程序产生了日志信息,通过该信道就会把日志文件记录在指定的本地文件、数据库或远程rsyslog服务器中。
当然应用程序输出的日志一般也会按照级别划分,比如sshd_conf中就定义了信道为authpriv,级别为info的日志输出:
# Logging — SyslogFacility AUTHPRIV — #LogLevel INFO
3、rsyslog支持的facility与priority
facility:设施、信道
从功能或程序上对日志进行分类,并由专门的工具负责记录其日志
常用的facility:
lpr: 打印相关的日志
auth: 认证相关的日志
user: 用户相关的日志
cron: 计划任务相关的日志
kern: 内核相关的日志
mail: 邮件相关的日志
mark: 标记相关的日志
news: 新闻相关的日志
uucp: 文件copy相关的日志
daemon: 系统服务相关的日志
authpri: 授权相关的日志
security: 安全相关的日志
syslog: 由syslogd服务产生的日志信息,虽然服务名称改为rsyslogd,但是很多配置都还是沿用了syslogd的,这里并没有修改服务名
local0-local7:自定义相关的日志信息(自定义时可以使用通配符)
priority:级别
debug #有调式信息的,日志信息最多 info #一般信息的日志,最常用 notice #最具有重要性的普通条件的信息 warning, warn #警告级别 err, error #错误级别,阻止某个功能或者模块不能正常工作的信息 crit #严重级别,阻止整个系统或者整个软件不能正常工作的信息 alert #需要立刻修改的信息 emerg, panic #内核崩溃等严重信息 ###从上到下,级别从低到高,记录的信息越来越少,如果设置的日志内性为err,则日志不会记录比err级别低的日志
二、rsyslog配置
1、程序环境
程序包:rsyslog
配置文件:/etc/rsyslog.conf, /etc/rsyslog.d/*.conf
主程序:/usr/sbin/rsyslogd
模块路径:/lib64/rsyslog/
Unit File:/usr/lib/systemd/system/rsyslog.service
2、配置文件/etc/rsyslog.conf格式详解
由三部分组成,必须严格按照配置段位置添加配置
1 2 3 4 | [[email protected]~]# grep "####" /etc/rsyslog.conf#### MODULES ######## GLOBAL DIRECTIVES ######## RULES #### |
MODULES:定义装载的模块,如接下来的使用mysql模块记录日志则需要在这里配置
GLOBAL DIRECTIVES:定义了全局的环境
RULES:定义了记录日志的设施以及等级等信息
定义规则的格式为:
facility.priority Target
facility可以使用的通配符:
*:所有
,:列表,如f1,f2,f3...
!:取反
priority可以使用的通配符:
*:所有日志级别
none:没有任何级别,也就是不记录日志信息
Target:目标,指日志保存的位置
可以使用的有:
文件,如/var/log/messages
用户:* 表示当前登录系统的所有用户
日志服务器:@host ##host: 必须要监听在tcp或udp协议514端口上提供服务;
管道:| COMMAND
例如:
mail.info /var/log/maillog
表示将mail产生的info日志级别以上的信息都记录在/var/log/maillog文件中
mail.=info 表示仅记录info级别日志
mail.!info 表示记录info以下级别的日志
*.info 表示所有设施的info级别
mail,news.info 表示mail和news都使用info级别
有些日志记录二进制格式:/var/log/wtmp,/var/log/btmp
/var/log/wtmp: 当前系统上成功登录的日志; last
/var/log/btmp:当前系统上失败的登录尝试; lastb
lastlog命令:显示当前系统每一个用户最近一次的登录时间;
3、配置文件/etc/rsyslog.conf详解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | #### MODULES 日志的模块####$ModLoad imuxsock #imuxsock是模块名,支持本地系统日志的模块$ModLoad imklog #imklog是模块名, 支持内核日志的模块#$ModLoad immark #immark是模块名,支持日志标记#$ModLoad imudp #imupd是模块名,支持udp协议#$UDPServerRun 514 #允许514端口接收使用UDP和TCP协议转发过来的日志#$ModLoad imtcp #imtcp是模块名,支持tcp协议#$InputTCPServerRun 514#### GLOBAL DIRECTIVES ####定义全局日志格式的指令$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat #定义日志格式默认模板$IncludeConfig /etc/rsyslog.d/*.conf #载入rsyslog.d文件中所有以conf结尾的文件#### RULES ####*.info;mail.none;authpriv.none;cron.none /var/log/messages#####记录所有日志类型的info级别以及大于info级别的信息到/var/log/messages,但是mail邮件信息,authpriv验证方面的信息和cron时间#任务相关的信息除外authpriv.* /var/log/secure#####authpriv验证相关的所有信息存放在/var/log/securemail.* -/var/log/maillog#####邮件的所有信息存放在/var/log/maillog; 这里有一个-符号, 表示是使用异步的方式记录, 因为日志一般会比较大cron.* /var/log/cron####计划任务有关的信息存放在/var/log/cron*.emerg * (*表示所有用户)###记录所有的大于等于emerg级别信息, 以wall方式发送给每个登录到系统的人uucp,news.crit /var/log/spooler####记录uucp,news.crit等存放在/var/log/spoolerlocal7.* /var/log/boot.log####本地服务器的启动的所有日志存放在/var/log/boot.log中 |
三、配置使用基于mysql存储日志信息,并结合前端loganalyzer工具分析日志
1、配置rsyslog日志存储于mysql中
(1) 准备好MySQL服务器,创建用户,授权对Syslog数据库的全部访问权限;
mysql> grant all on Syslog.* to ‘syslog‘@‘192.168.137.%‘ identified by ‘123456‘;
(2) rsyslog服务起上安装rsyslog-mysql程序包;
yum install -y rsyslog-mysql
(3) 创建rsyslog-mysql依赖的数据库;
rpm -ql rsyslog-mysql
/lib64/rsyslog/ommysql.so
/usr/share/doc/rsyslog-mysql-5.8.10
/usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql ##建库脚本位置
# yum install mysql -y ##rsyslog服务器安装mysql客户端
# mysql -usyslog -p123456 -h192.168.137.130 --default-character-set=utf8 < /usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql
mysql> use Syslog
Database changed
mysql> show tables;
+------------------------+
| Tables_in_Syslog |
+------------------------+
| SystemEvents |
| SystemEventsProperties |
(4) 配置rsyslog使用ommysql模块
vim /etc/rsyslog.conf
#### MODULES ####
$ModLoad ommysql
#### RULES ####
*.info;mail.none;authpriv.none;cron.none :ommysql:192.168.137.130,Syslog,syslog,123456
重启rsyslog服务: service rsyslog restart
(5)测试日志记录
rsyslog服务器:yum remove lrzsz
mysql> select * from SystemEvents\G
2、安装loganalyzer(rsyslog专用前端展示工具)
(1)准备环境,loganalyzer为php程序开发的web页面
yum install -y httpd php php-mysql (mysql mysql-server rsyslog-mysql前期已安装)
测试httpd能否正常工作,能否通过php工作
[[email protected] ~]# cd /var/www/html/
[[email protected] html]# vim index.php
Hello word!
My Blog is "http://guopeng7216.blog.51cto.com/"
<?php
phpinfo();
?>
测试php和mysql结合
[[email protected] html]# cat index.php<?php
$link=mysql_connect(‘192.168.137.150‘,‘syslog‘,‘123456‘);
if($link){
echo "success..frank!";
}else{
echo "failed..frank!".mysql_error();
}
mysql_close($link);
phpinfo();
?>
(2)、下载loganalyzer并进行安装配置;
http://pan.baidu.com/s/1nvsN5rz
~]# tar xf loganalyzer-3.6.4.tar.gz
~]# cd loganalyzer-3.6.4
loganalyzer-3.6.4]# cp -r src /var/www/html/loganalyzer
loganalyzer-3.6.4]# cp contrib/*.sh /var/www/html/loganalyzer/
loganalyzer-3.6.4]# cd /var/www/html/loganalyzer/
loganalyzer]# chmod u+x *.sh
loganalyzer]# ./configure.sh
loganalyzer]# ./secure.sh
loganalyzer]# chown -R apache:apache ./*
修改rsyslog的配置文件rsyslog.conf,只需开启两个模块以及允许通过tcp,udp发出接受信息,并且设置信息都保存至mysql数据库的Syslog中,
# Provides UDP syslog reception
$ModLoad imudp
$UDPServerRun 514
# Provides TCP syslog reception
$ModLoad imtcp
$InputTCPServerRun 514
日志数据存储在数据库中,其它全部注释掉
*.* :ommysql:192.168.137.150,Syslog,syslog,123456
安装loganalyzer:
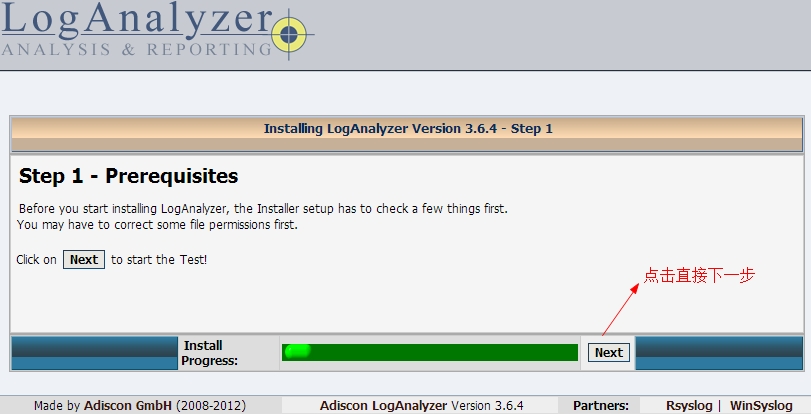
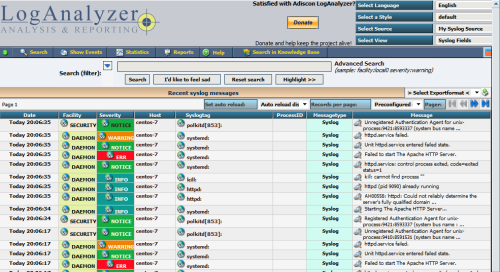
http://192.168.137.150/loganalyzer/install.php
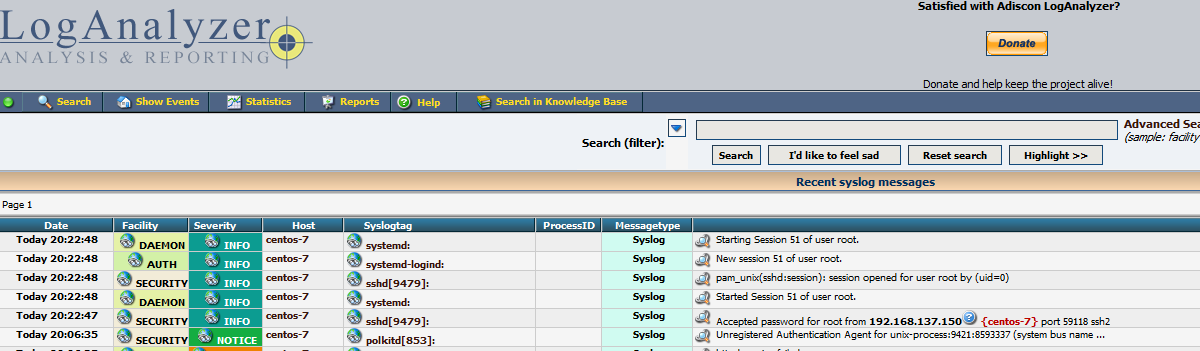
对loganalyzer日志系统进行测试,在本机上通过ssh连接192.168.137.150
[[email protected] loganalyzer]# ssh 192.168.137.150
[email protected]‘s password:
Last login: Thu May 11 19:37:06 2017 from centos-7
重新配置loganalyzer:
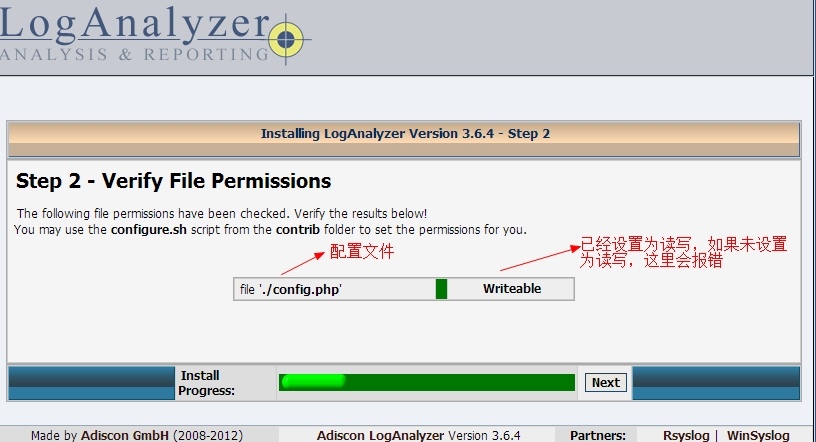
loganalyzer]# rm -f config.php
loganalyzer]# ./configure.sh
loganalyzer]# ./secure.sh
loganalyzer]# chmod 666 config.php
http://192.168.137.150/loganalyzer/install.php
以上是关于Rsyslog 收集tomcat日志的主要内容,如果未能解决你的问题,请参考以下文章